Windows - How to Configure Agentless Password Automation
This document will help you to configure Powershell Script Service for Monopam for Password Rotation. Before you continue, you need to make sure you have a valid license and configuration on your Monopam.
📘 Instructions
This documentation will contain 2 main steps.
Configure for Credentials
Conditional - Configure Machine Policy
Monopam uses WMI - Windows Management Infrastructure to do remote actions on machine. You can see the following url for more information.
https://learn.microsoft.com/en-us/windows/win32/wmisdk/wmi-start-page
WMI by default using port 135. This port should be added as firewall rule if not allowed.
If your WMI giving an error about access, you can add following filter and test it.
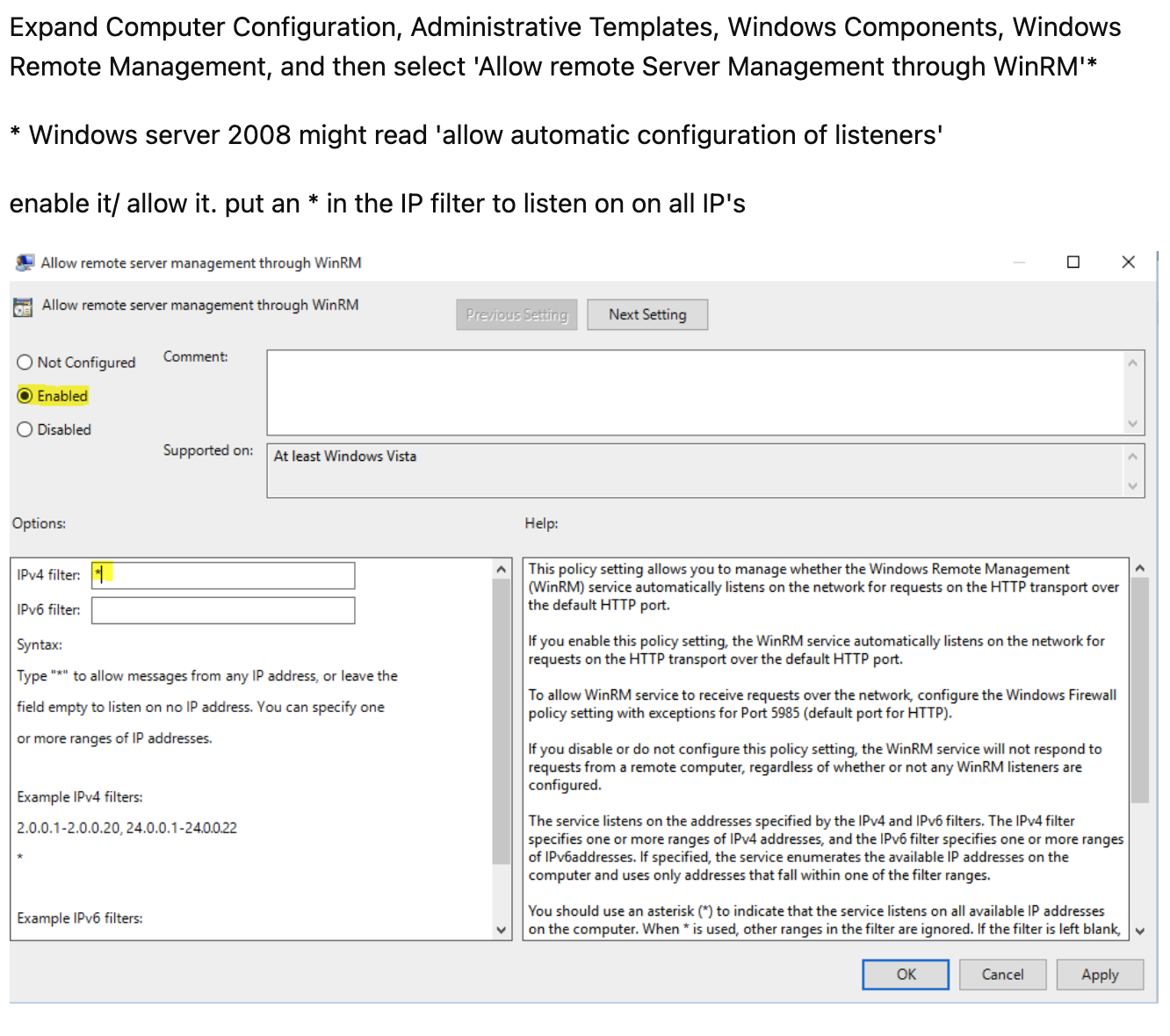
1. Configure Machine Credentials
Monopam local admin user should be added to the machine. This can be a Domain User or Local User to manage the machine’s local users.
Remember, this user should be local admin in the machine.
If you want to use Local Windows Account
Recommended username for local:
monopamormonopam_localThis section also requires
Configure Machine Policyto disable Admin Approval Mode for Administrators
If you want to use Domain Account that has Admin Rights on Machine
Recommended username for AD:
monopam_adpThis step does not require
Configure Machine PolicyStep.
Conditional - Configure Machine Policy (If you want to use Local Account)
Important
This configuration should be configured only that you will use Local Account for operations. If you are using Active Directory Account that has Admin Rights on Machine, you should skip this step!
Monopam uses WMI to detect local accounts on Windows machines. So, you need to enable Windows Management Instrumentation (WMI) if it is not enabled before.
You can use one of the following 3 commands following;
Policy Management
Regedit
Powershell
Recommended - Policy Management
Add a firewall rule for Windows Management Instrumentation (WMI)
Make sure Monopam admin user is in Administrator group on the local machine
Disable the UAC (User Access Control) for the
Administrator's groupType
gpedit.mscand RunGo to the Computer Configuration > Windows Settings > Security Settings > Security Options and find
User Account Control: Run all administrators in Admin Approval Modeand set valueDisabledThat requires Restart and Policy Update.
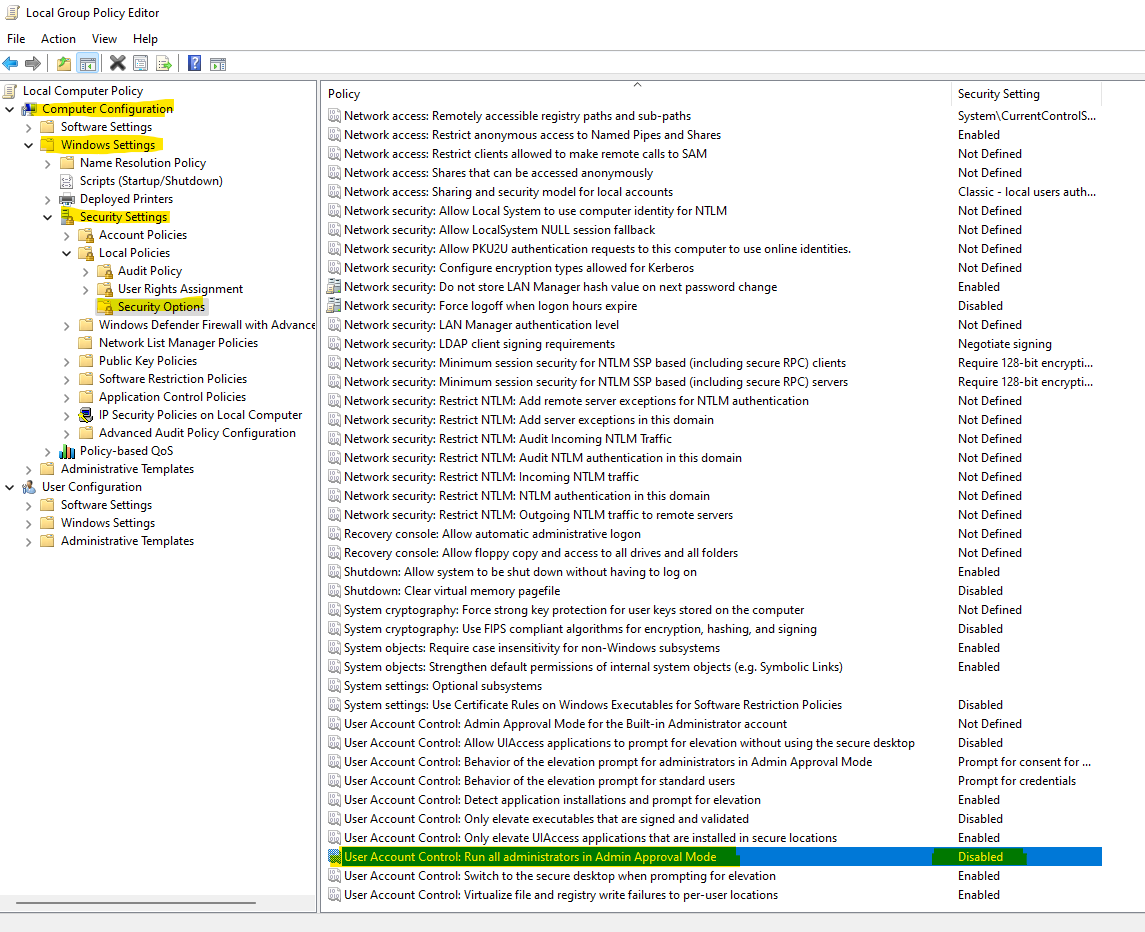
You can see the setting on the UI.
Optional - Regedit
You can also set this option from Regedit (regedit.exe). If you want to do it (still requires restart), do the following.
Open regedit
Go to the
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Systemand create newD-WORD (32-Bit) Valueand name it asEnableLUAkey (or update if you have that already).Type value as
0and OK.Restart the computer.
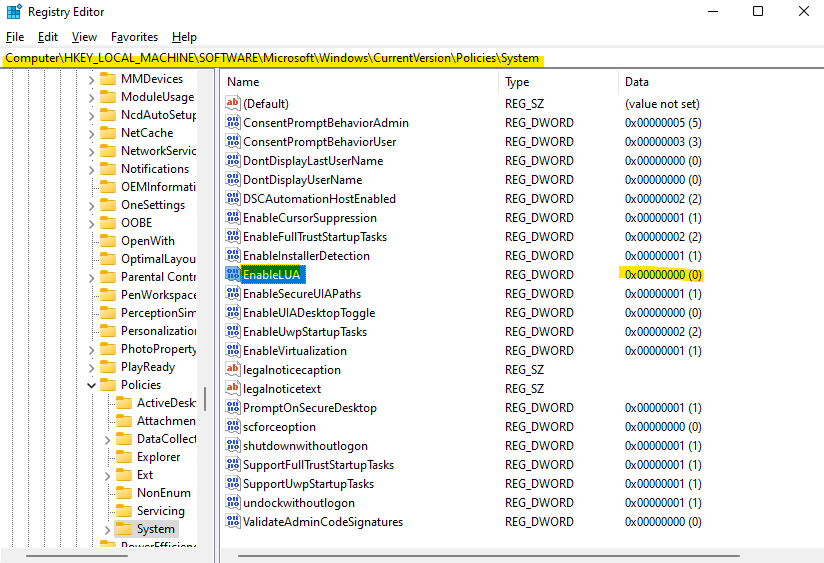
Optional - Powershell Script
Another way that you can use is Powershell. You need to run Powershell as an Administrator before you continue;
Open Powershell as Administrator
Run the following command. Your computer will restart automatically.
# Run this command in an elevated PowerShell prompt (as an administrator)
# Set the registry key to disable "Admin Approval Mode"
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" -Name "EnableLUA" -Value 0
# After making these changes, you should restart the computer for the changes to take effect.
Restart-Computer