AdminSDHolder - User Account Permission Issue
Identifying Accounts with Security Inheritance Disabled
Monosync integration with Active Directory you can face an issue about permission one or more AD accounts. The error Result: 50 - Insufficient Access Rights . It means this user inheritance is disabled and some permissions are broken. For example in the past that user is memberOf Domain admins and now it is not.
You can check if an individual service or user account has security inheritance disabled in AD Users and Computers. Enable Advanced Settings, open the properties of the user account, and click the Advanced… button in the Security tab to see if inheritance is enabled or disabled.
You can also use the Active Directory PowerShell module to check directly if security inheritance is disabled:
For Specific user
Please replace OU NAME and USERNAME with exact value
Get-ADUser -SearchBase "OU NAME" -Filter 'SamAccountName -like "USERNAME"' -Properties nTSecurityDescriptor | ?{ $_.nTSecurityDescriptor.AreAccessRulesProtected -eq "True" }
Alternative
Get-ADUser USERNAME -Properties ntsecuritydescriptor | Select -expand ntsecuritydescriptor | Select areaccessrulesprotected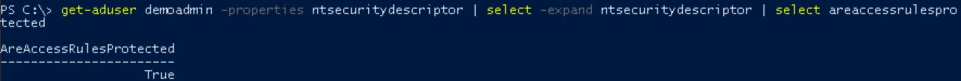
If the result is True then inheritance is disabled; if it is False, then inheritance is enabled.
For All user
Please replace OU NAME with exact value
Get-ADUser -SearchBase "OU=AlkanLAB,DC=alkanlab,DC=com" -Filter * -Properties SamAccountName,nTSecurityDescriptor | Where-Object { $_.nTSecurityDescriptor.AreAccessRulesProtected -eq "True" } | Select-Object SamAccountName, @{Name="AreAccessRulesProtected"; Expression={$_.nTSecurityDescriptor.AreAccessRulesProtected}}
If this command return result(s) then it means inheritance is disabled. If this command returns no results then user inheritance is enabled.
Finding Users and Groups affected by AdminSDHolder
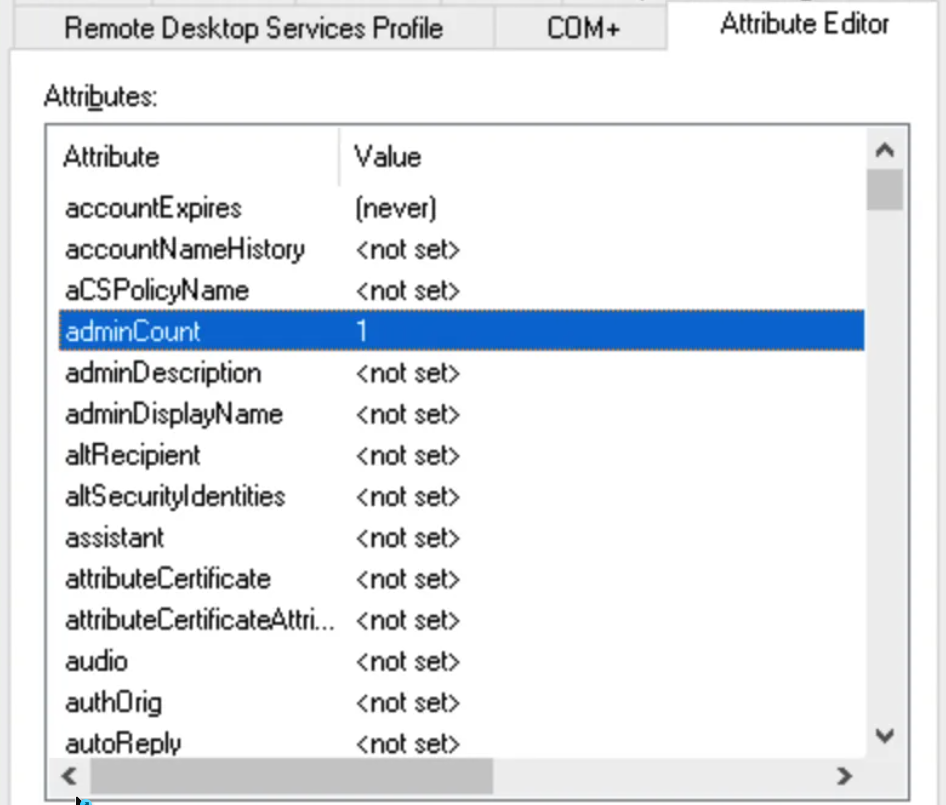
If the adminCount attribute on a user is set to 1 or 0, we can assume it is (or was at some point in the past) a member of a protected group and affected by the AdminSDHolder role.
You can check the adminCount attribute on a user in ADUC (with advanced features enabled) or ADSIEdit:
Alternatively, use PowerShell
Get-ADUser USERNAME -Properties admincount | Select admincount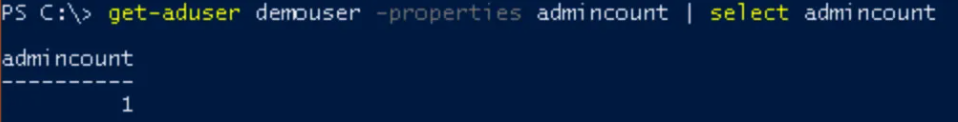
Note: If this command returns no results, the adminCount attribute is not set and the user is not affected by AdminSDHolder.
To find all users in your AD scope with the adminCount attribute set, use another PowerShell query on your AD scope:
Get-ADUser -SearchBase "OU NAME" -Filter * -Properties adminCount | where {$_.adminCount -eq 1 }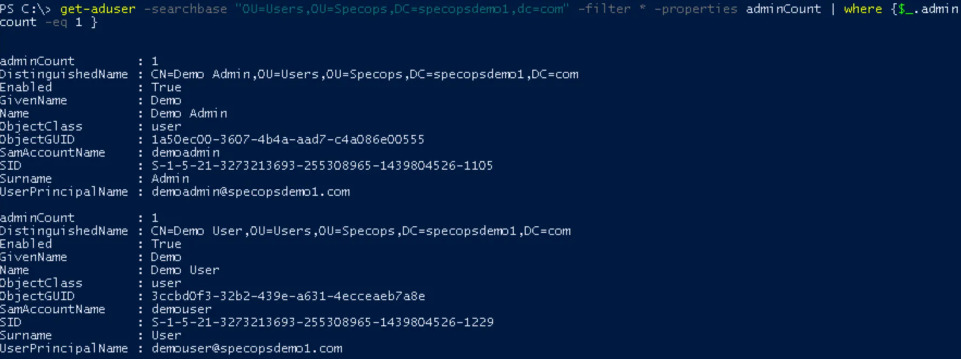
Which Admin Groups is Account In (if any)?
At this stage, it helps to focus on one or two key user accounts and check which admin groups they are in, if any.
$user = Get-ADUser USERNAME -Properties memberof
foreach ($group in $user.memberof) { Get-ADGroup $group -properties adminCount | where {$_.adminCount -eq 1} }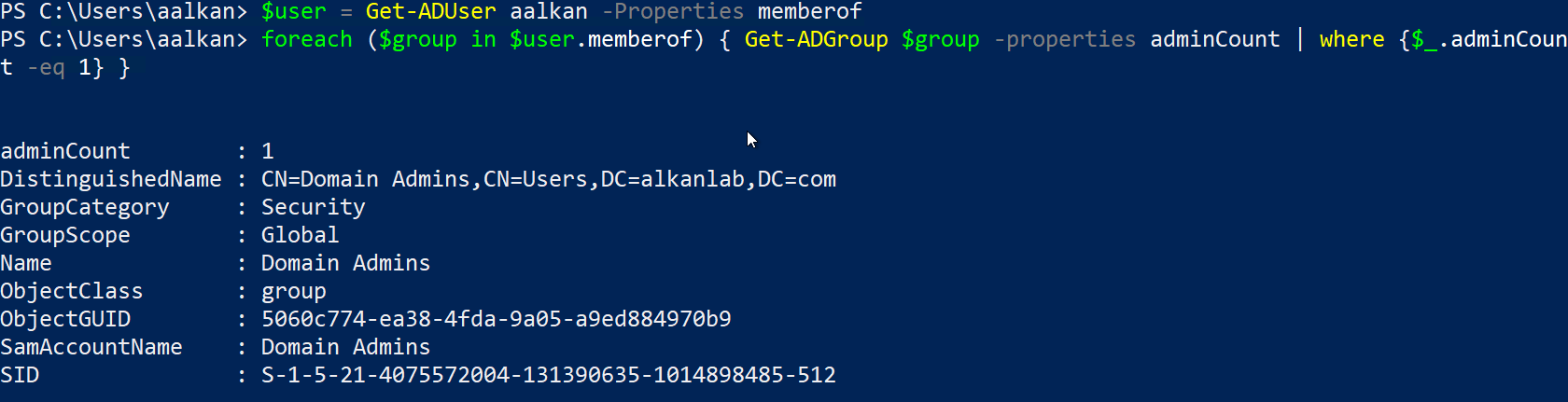
Cleanup
Once you’re sure the accounts with security inheritance disabled are no longer affected by AdminSDHolder, re-enable security inheritance and clear the adminCount attribute manually on each affected account.
Replace USERNAME with existing value. Sometimes admincount is set to to 0 and it will cause and issue. For this you need to change @{adminCount=1} to @{adminCount=0} below example.
Set-ADUser USERNAME -remove @{adminCount=1}
$user = Get-ADUser USERNAME -properties ntsecuritydescriptor
$user.ntsecuritydescriptor.SetAccessRuleProtection($false,$true)
Set-ADUser USERNAME -replace @{ntsecuritydescriptor=$user.ntsecuritydescriptor}