Google Workspace SAML Integration
This document explains how to implement MonoSign with Google Workspace. It covers Single Sign-On. Before you continue, it is better to start with Google Workspace’s Single Sign-On implementation page.
Creating Google Workspace Application on MonoSign
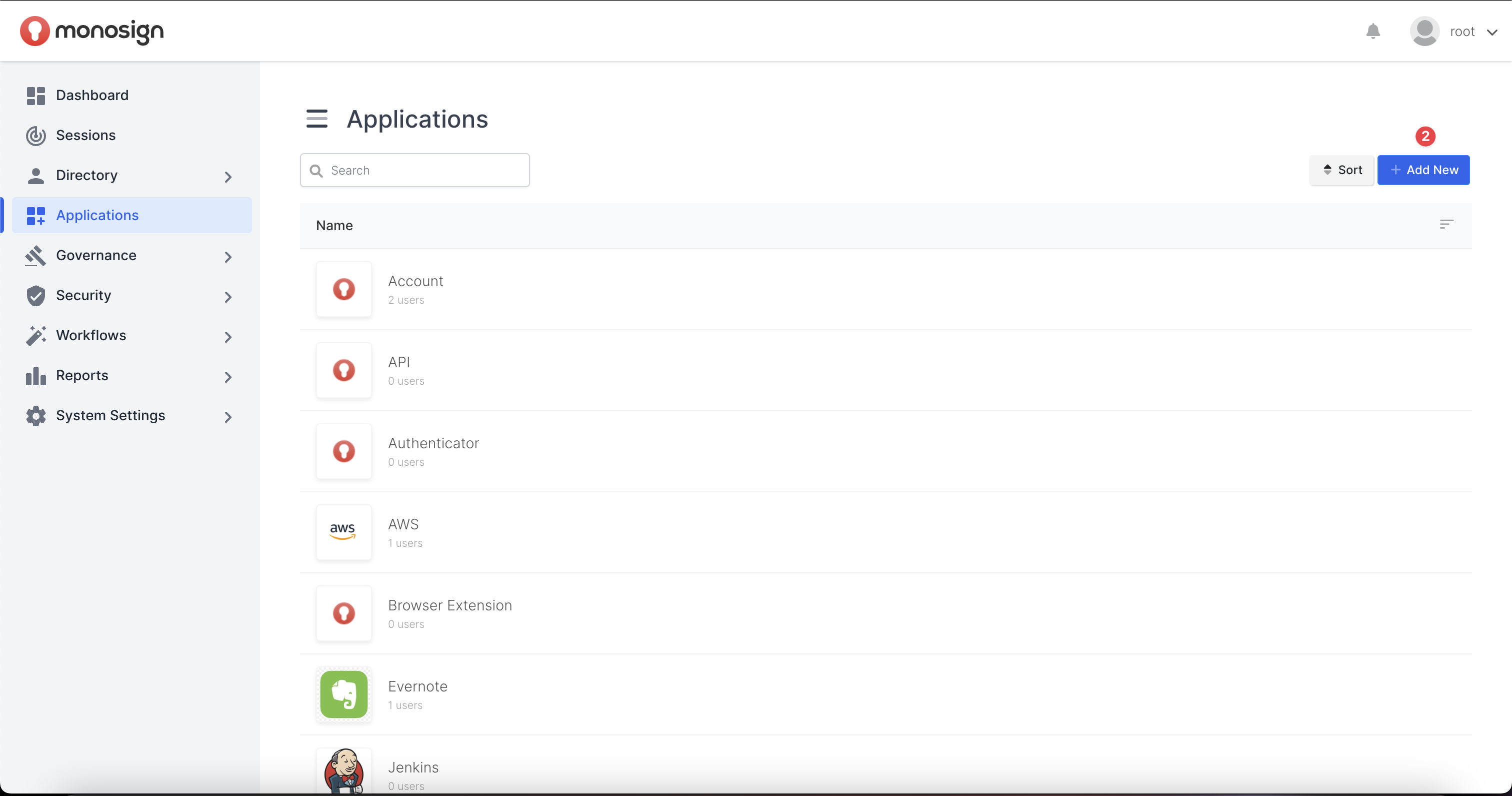
Navigate to Applications page by clicking Applications button on the navigation bar. To create a new application, please click the “Add New“ button. “Add New“ button navigate you to Application Create Page.
Navigate To Applications Page
Add a New Application
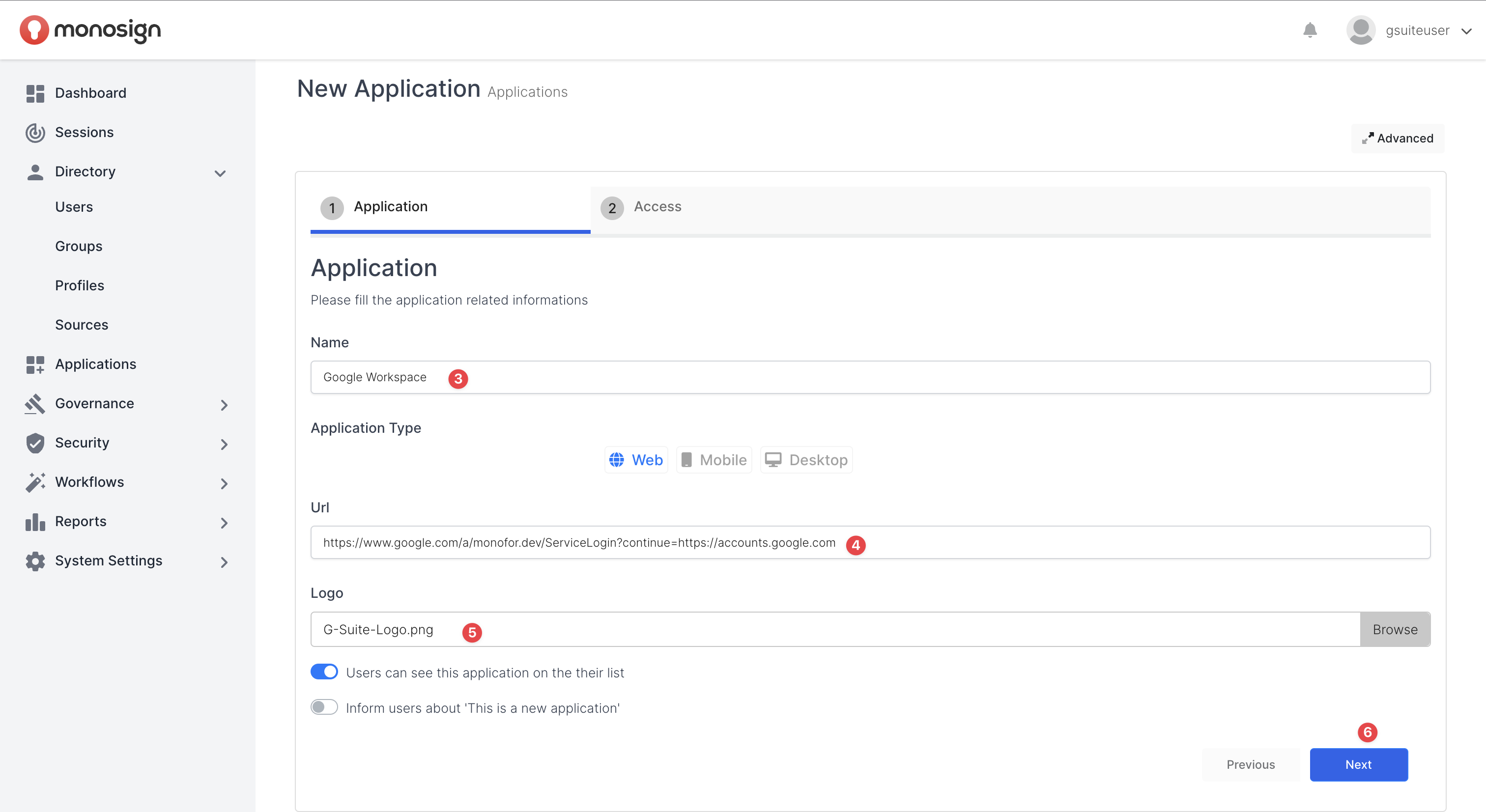
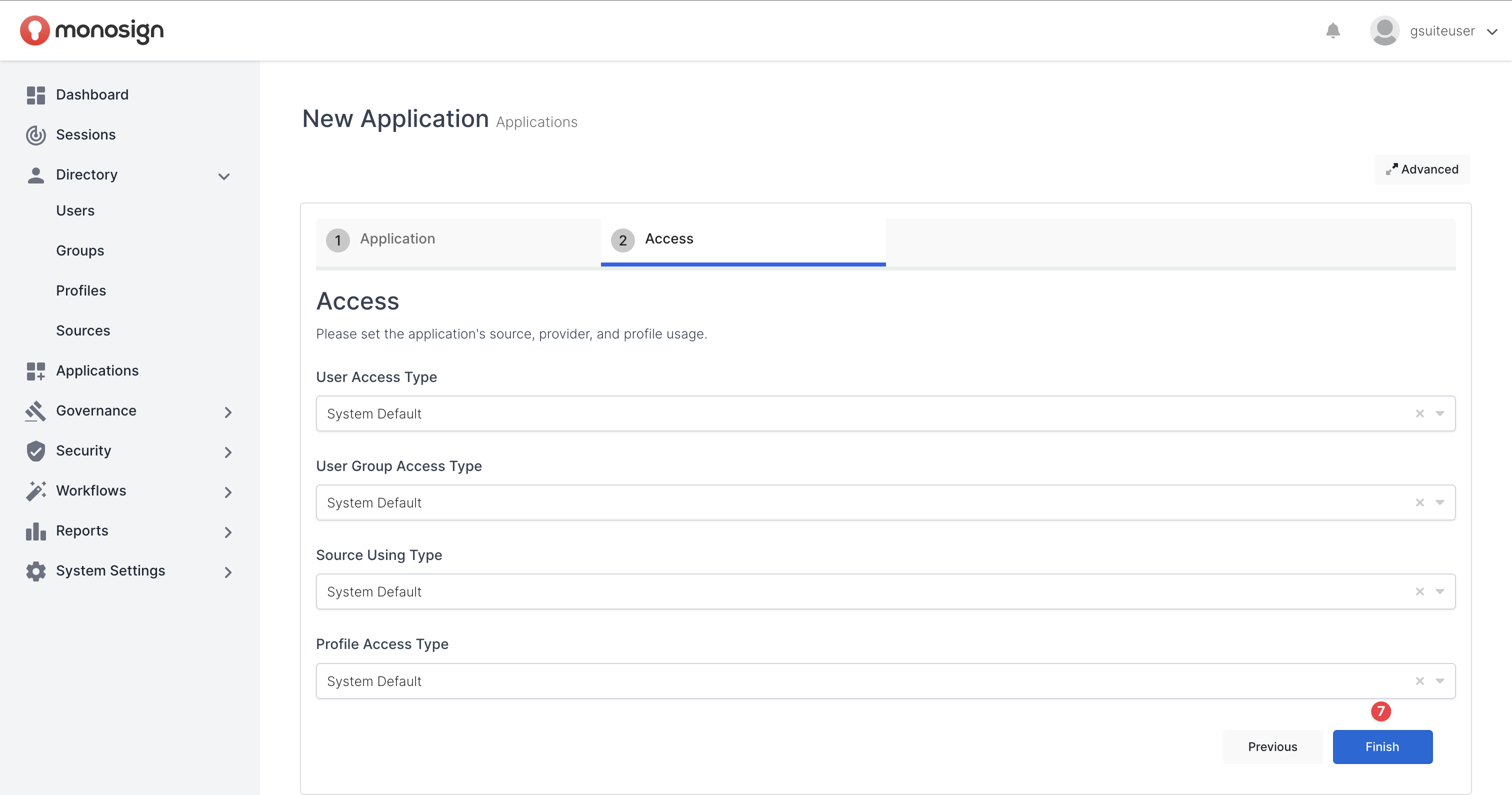
Firstly, let’s start setting up the Application Name, Application URL and Application Logo on Application Create Page. Application URL must be the one that “Google Workspace“ will give us while configuring SAML Authentication method.
Please go to MonoSign Management “Application Create“ page, fill in the inputs as shown and click the “Finish“ button.
Application Settings
Application Settings
Fields | Description |
|---|---|
Name | Application Name that will be displayed applications page |
URL | Application URL that copied from “Google Workspace“ application SSO SAML authentication configuration document |
Logo | Application Logo that will be displayed applications page |
Profile Access Type | User Profile Information that “Google Workspace“ application needs to be mapped |
Once application is created successfully, system will navigate you to Application Detail page.
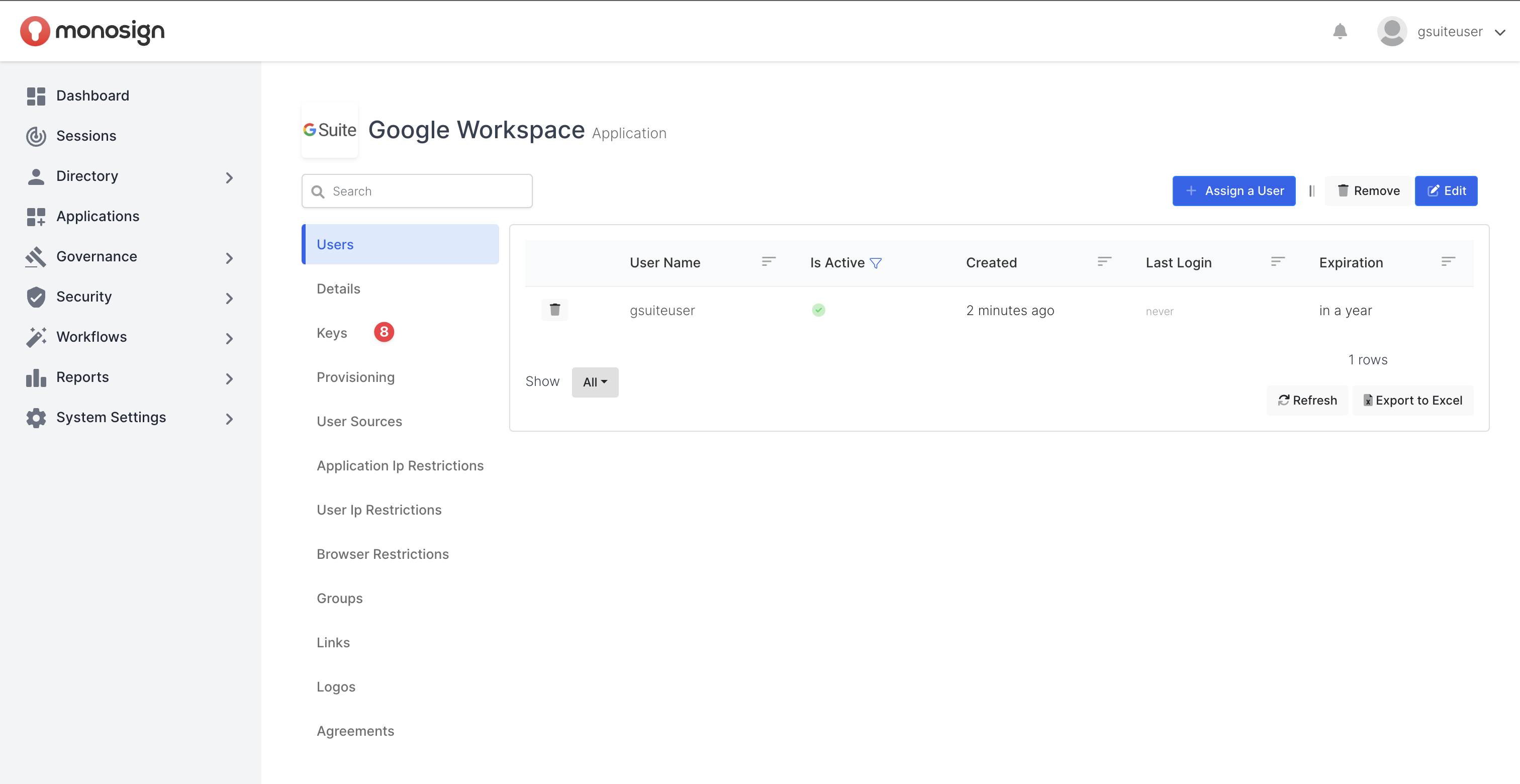
Navigate To Keys
Click the “Keys“ tab on Application Detail Page and then click the “Add New Access Key“ to add a SAML access key to the “Google Workspace” Application.
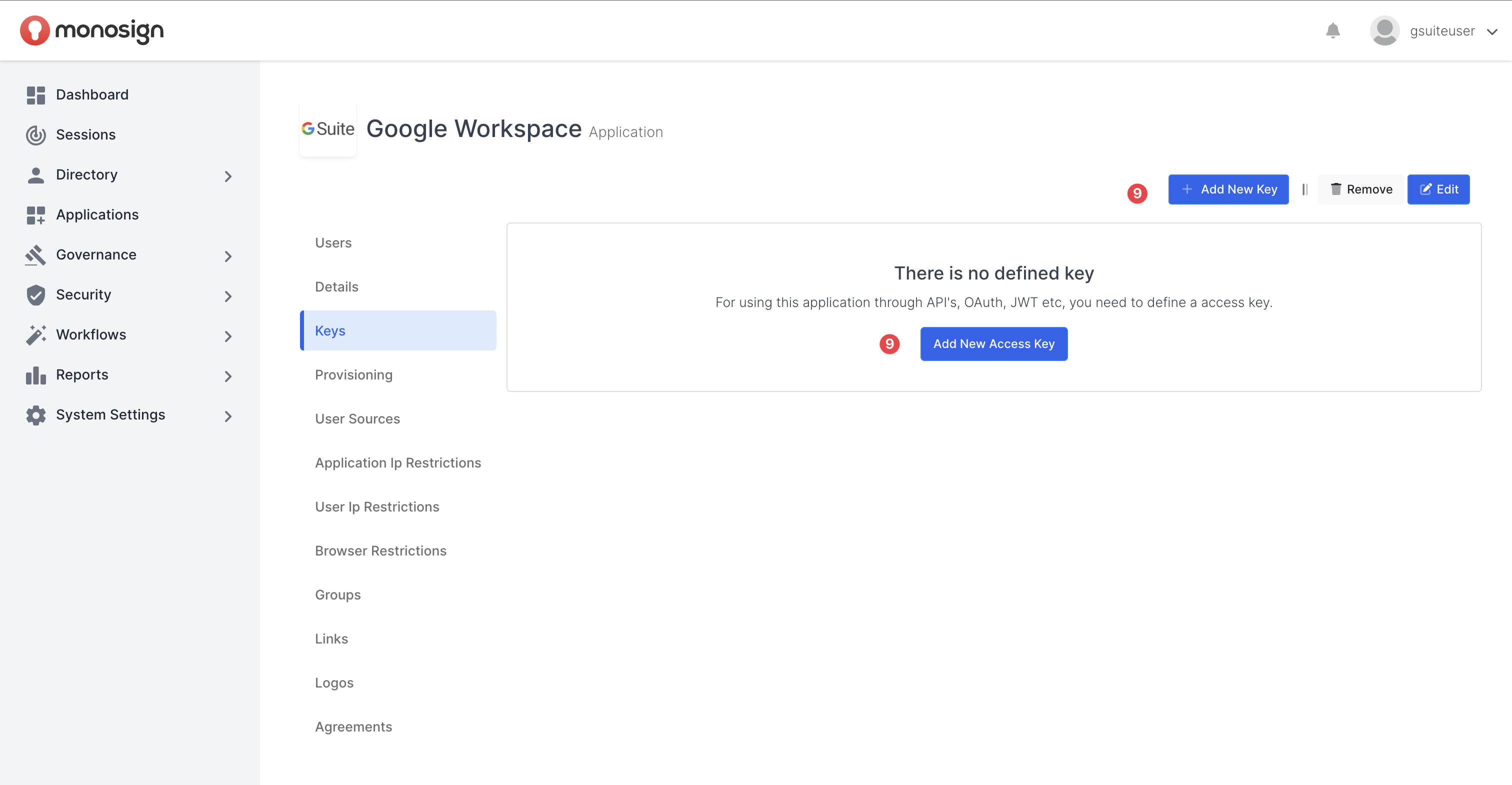
Add an Application Access Key
A modal will open when the button clicked. SAML2 Settings tab will be generated when you select “SAML” key type on the modal.
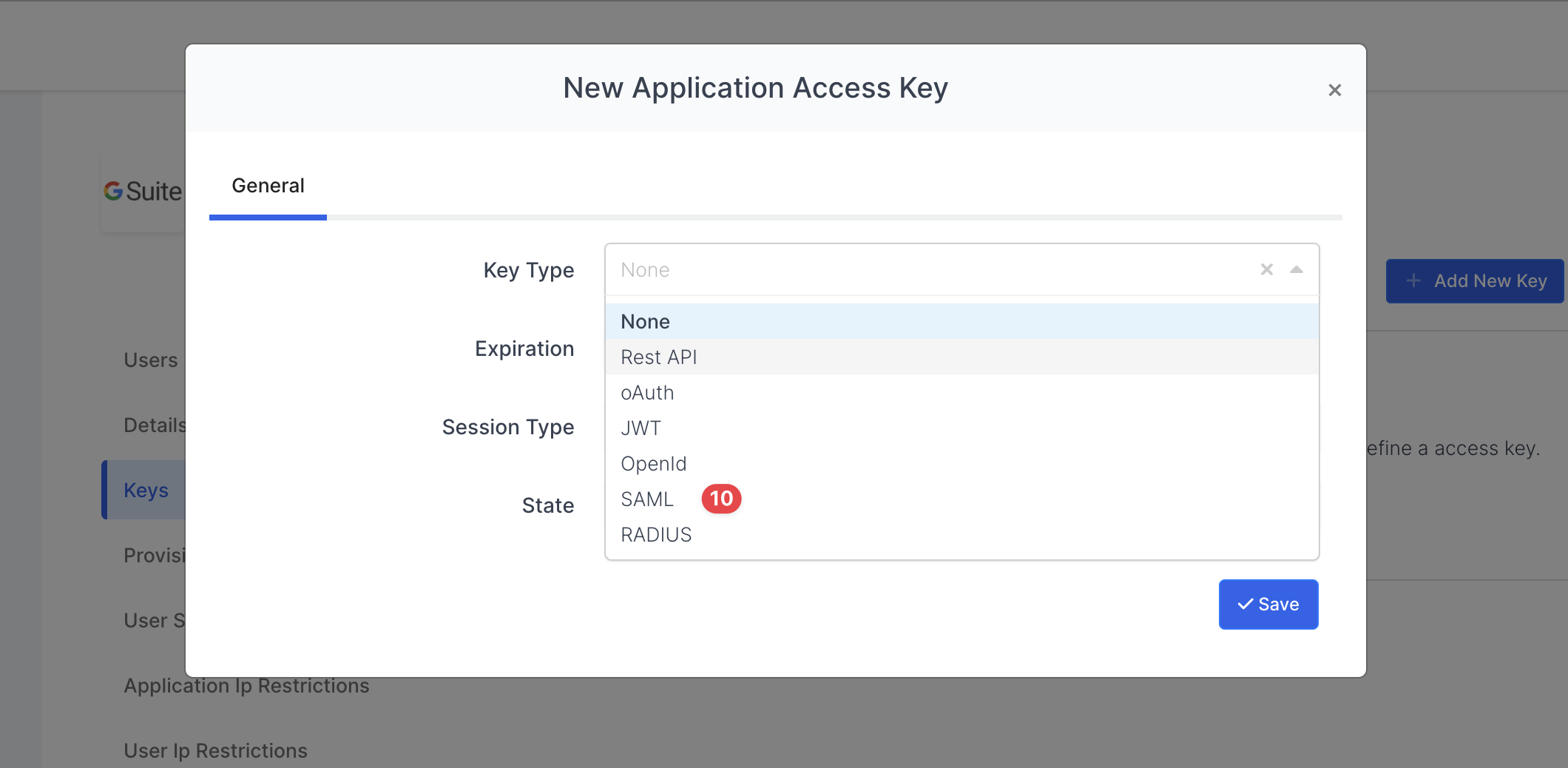
Selecting Key Type
We will configure “SAML2 Settings“ after key is generated on MonoSign. To generate “SAML2 Application Access Key”, please click the “Save“ button.
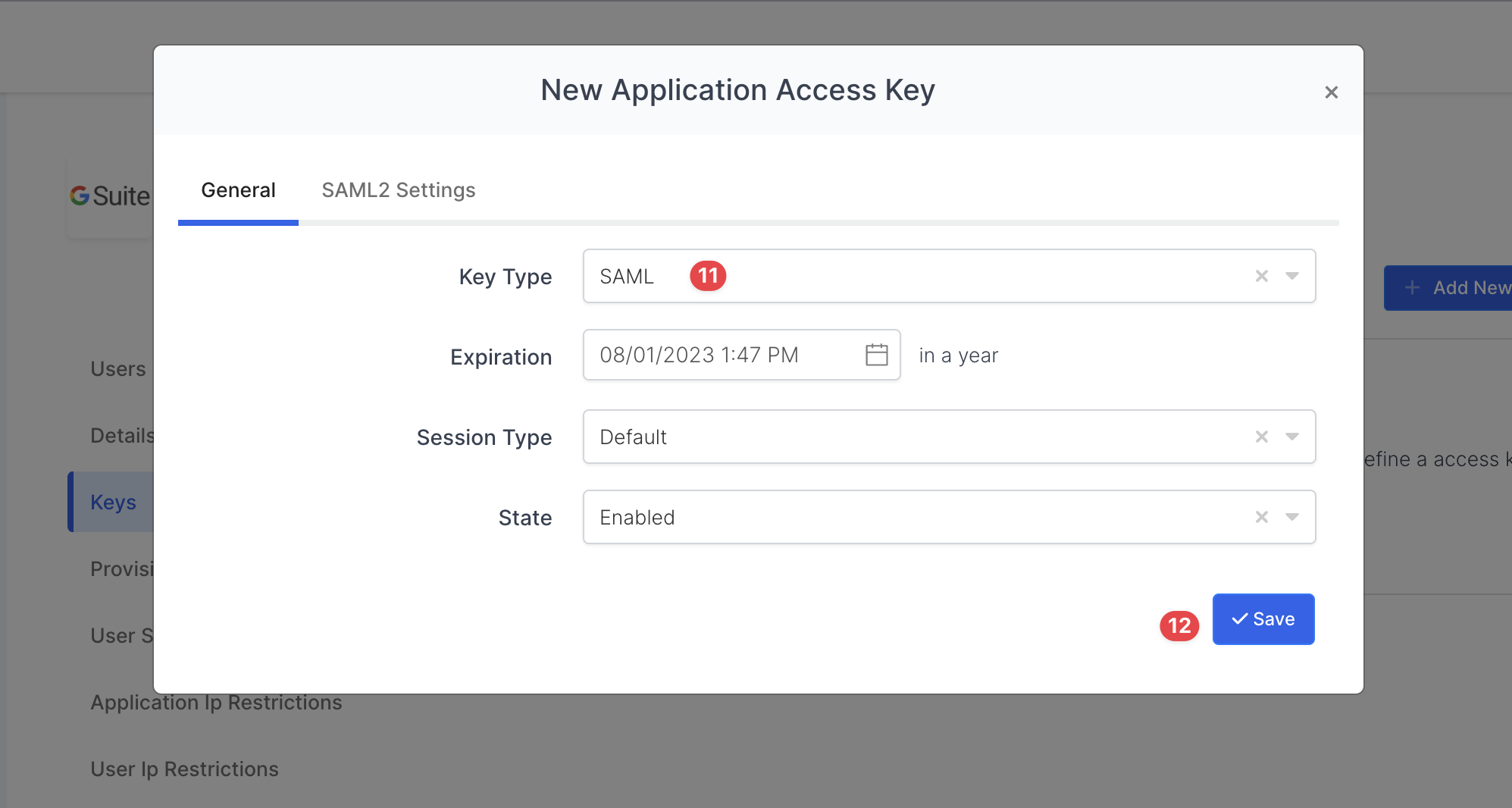
Generate SAML2 Application Access Key
The SAML application key will be generated as shown.
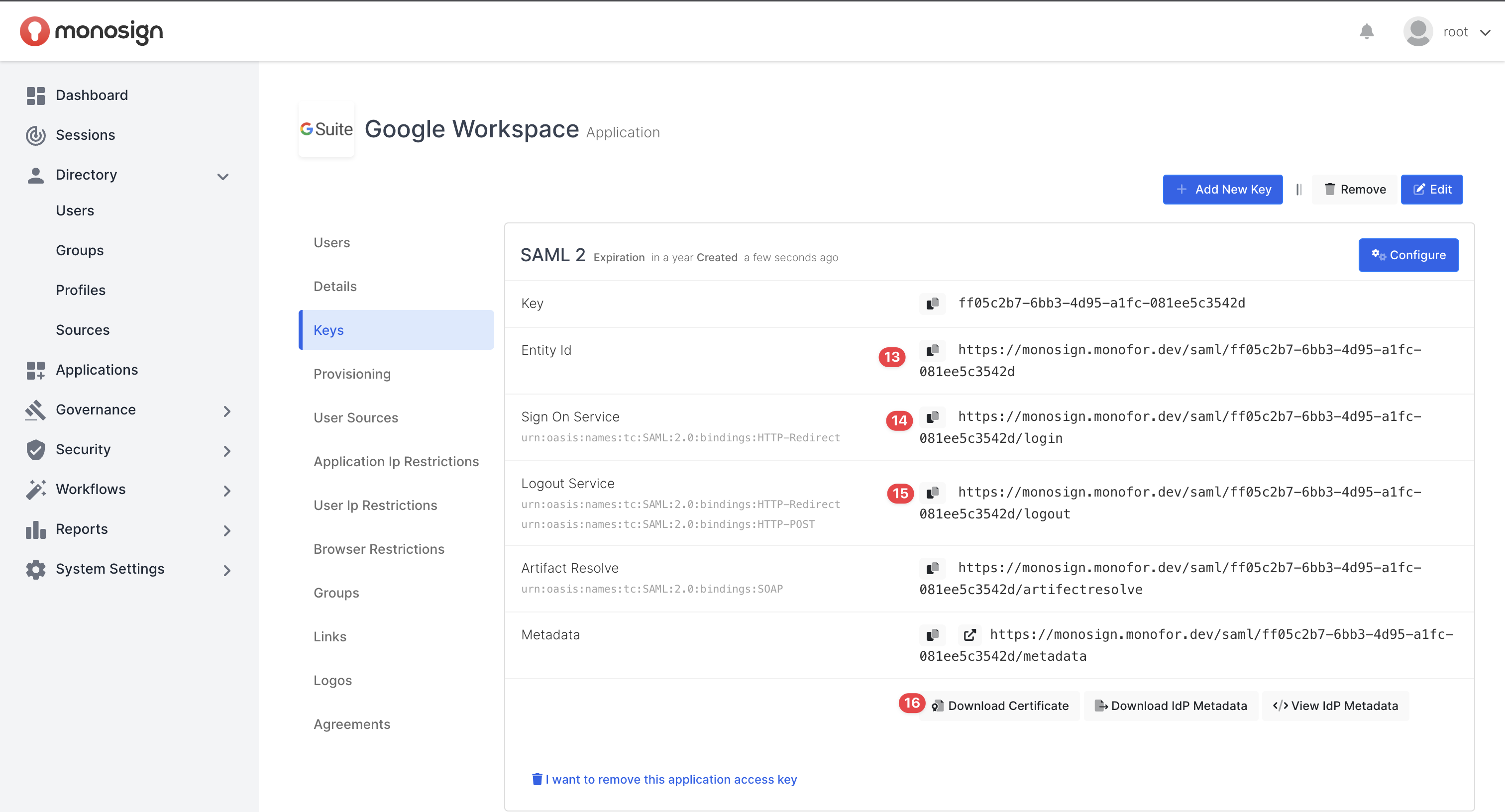
Generated SAML Application Access Key
Once Google Workspace Admin user created on Google Workspace for your organization, first of all, verify your domain with a TXT record.
Please follow the instructions to verify your organization domain.
Once your organization domain verified by Google DNS servers, you can start configuring SAML on both application.
To configure the SAML authentication method on Google Workspace and MonoSign, firstly admin user needs to navigate to Google Workspace Admin Panel via following the instructions on Google Workspace SAML SSO configuration instructions page as shown.
Navigate To Google Workspace Admin Panel
Admin user will be redirect to the Google Workspace Admin Panel for the organization.
Google Workspace Admin Panel
Navigate to Security → Authentication → SSO with third-party IdP page as shown.
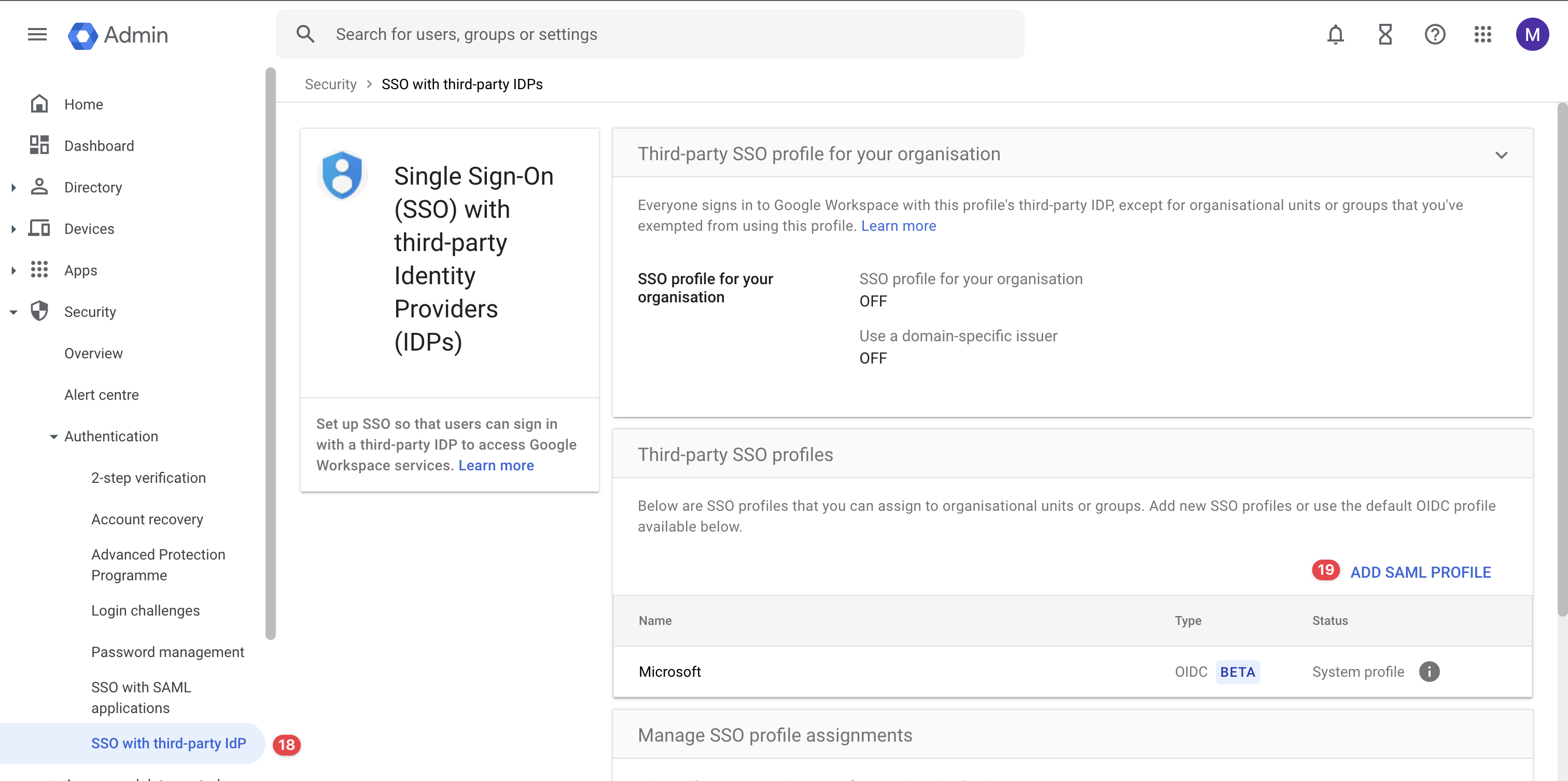
Navigate To SSO with third-party IdP
You will see the SSO configuration page for third-party IdPs. Now you will configure the settings for MonoSign IdP.
Firstly, you need to add a SAML Profile for MonoSign by clicking the “Add SAML Profile“ button.
Once the button clicked, “Add a new SAML SSO Profile“ page will be shown.
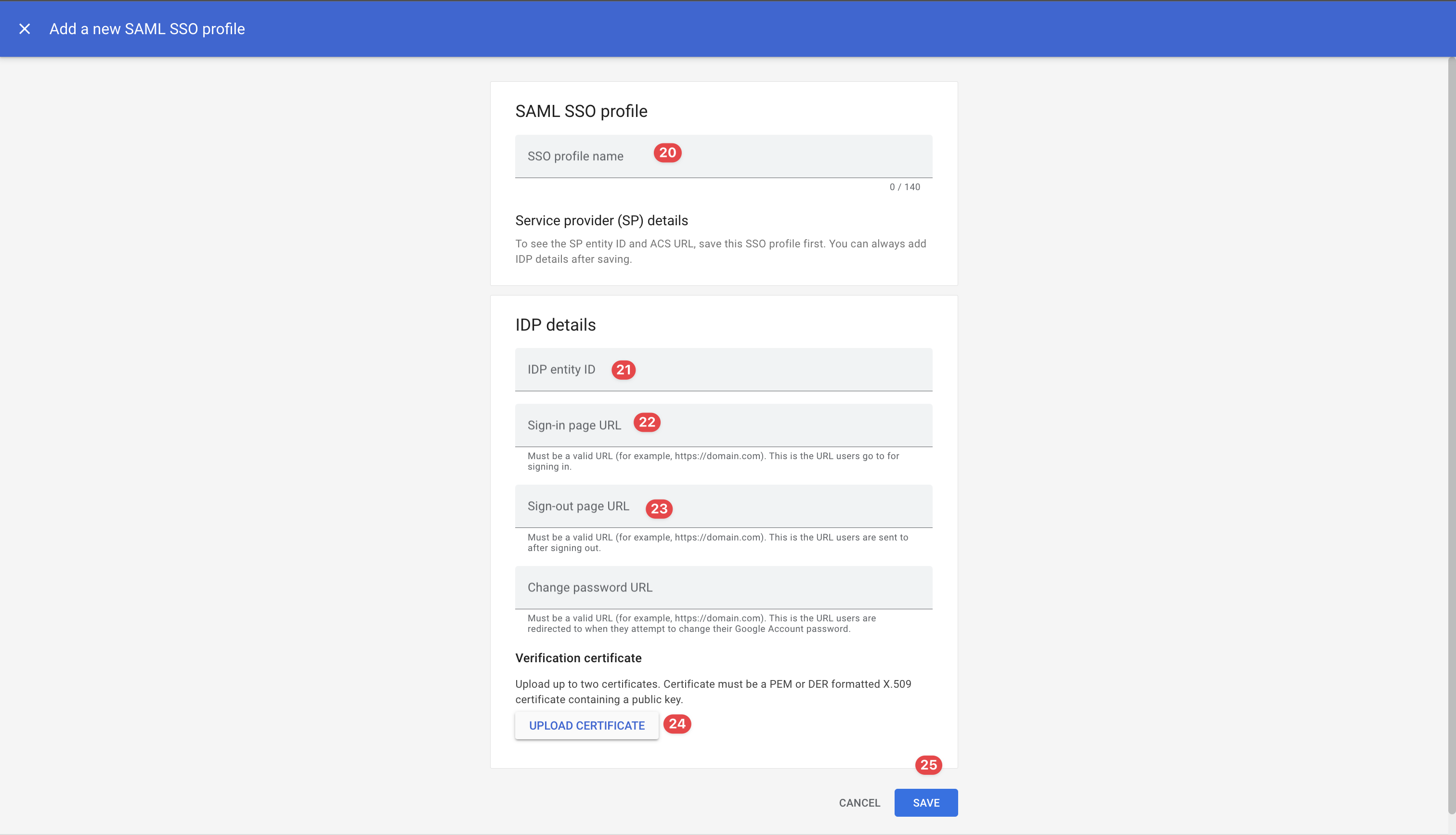
Add a New SAML SSO Profile
On the page, you will see the inputs about SAML SSO configurations. Please fill in the inputs with the information from MonoSign as shown.
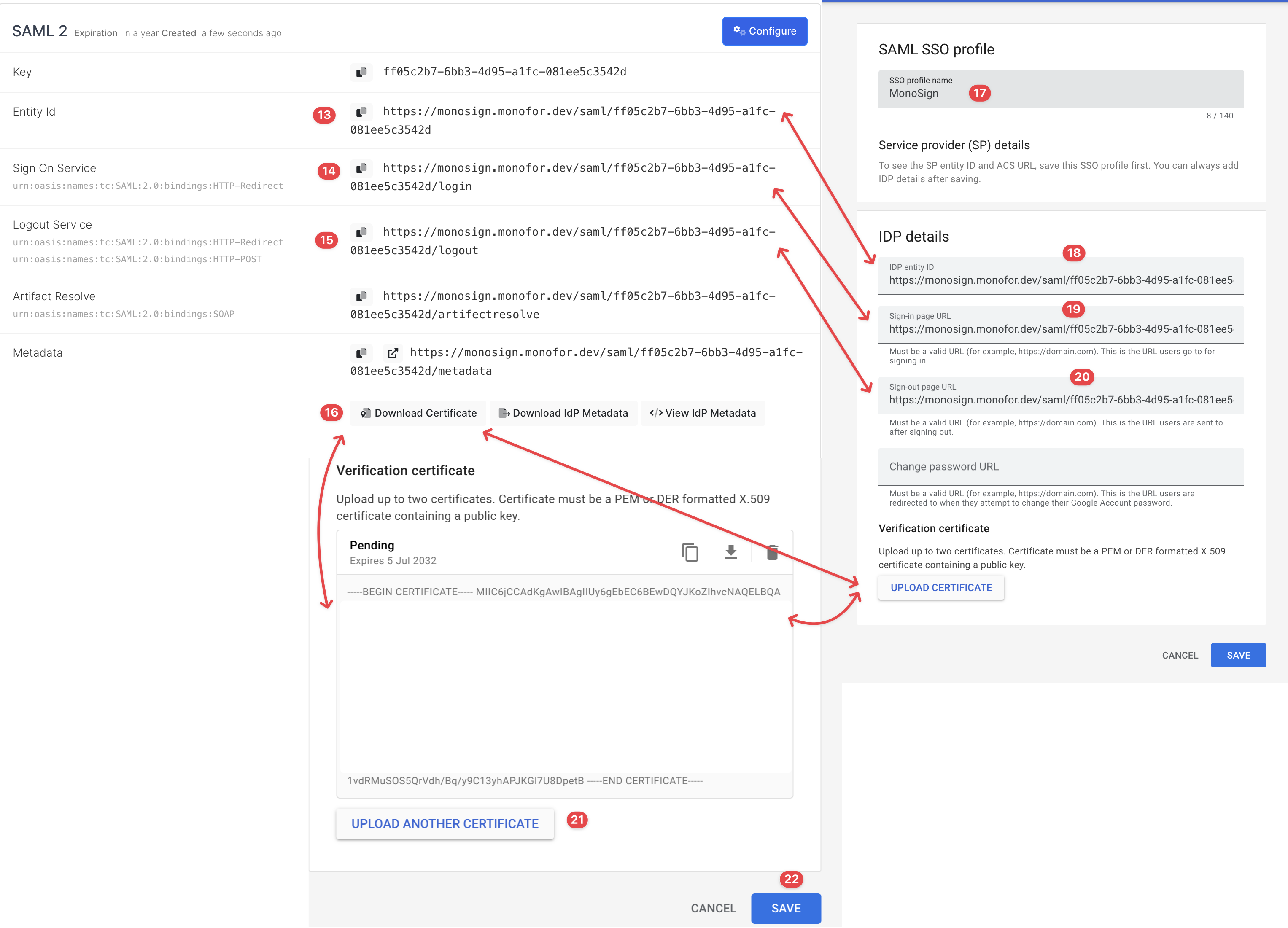
SAML Application Access Key Configuration on Google Workspace
Certificate input corresponds to the x509 format of the issued certificate for your SAML key on MonoSign.
Once the configurations completed correctly, please click the “Save“ button to save MonoSign SAML SSO profile.
If your organization wants all your users using SSO will use one IdP, please click the “pen“ button to open “Third-party SSO profile for your organization“ page.
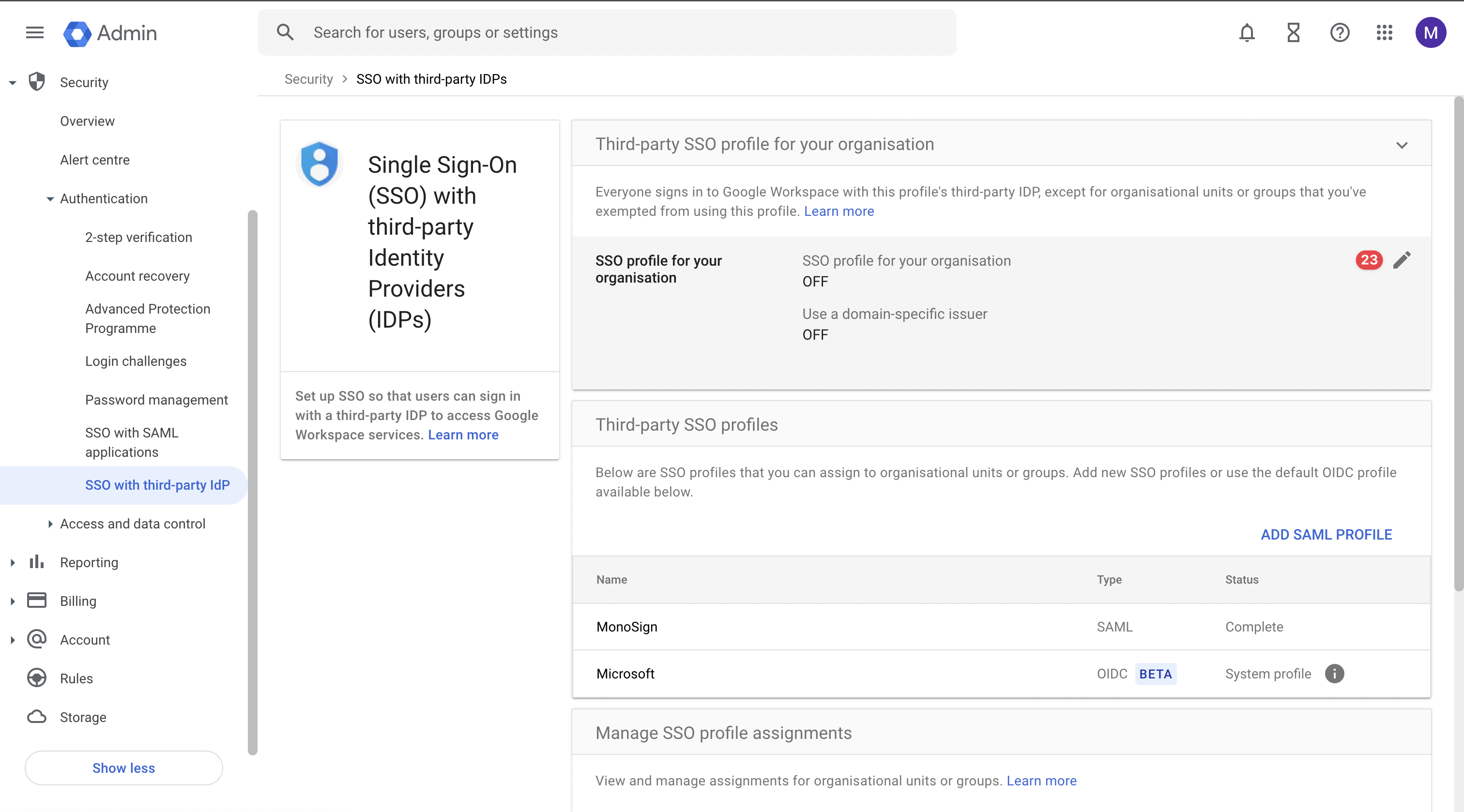
Third-Party SSO Profile for Your Organization
Please use the option and configure the “Third-party SSO profile for your organization“ as shown.
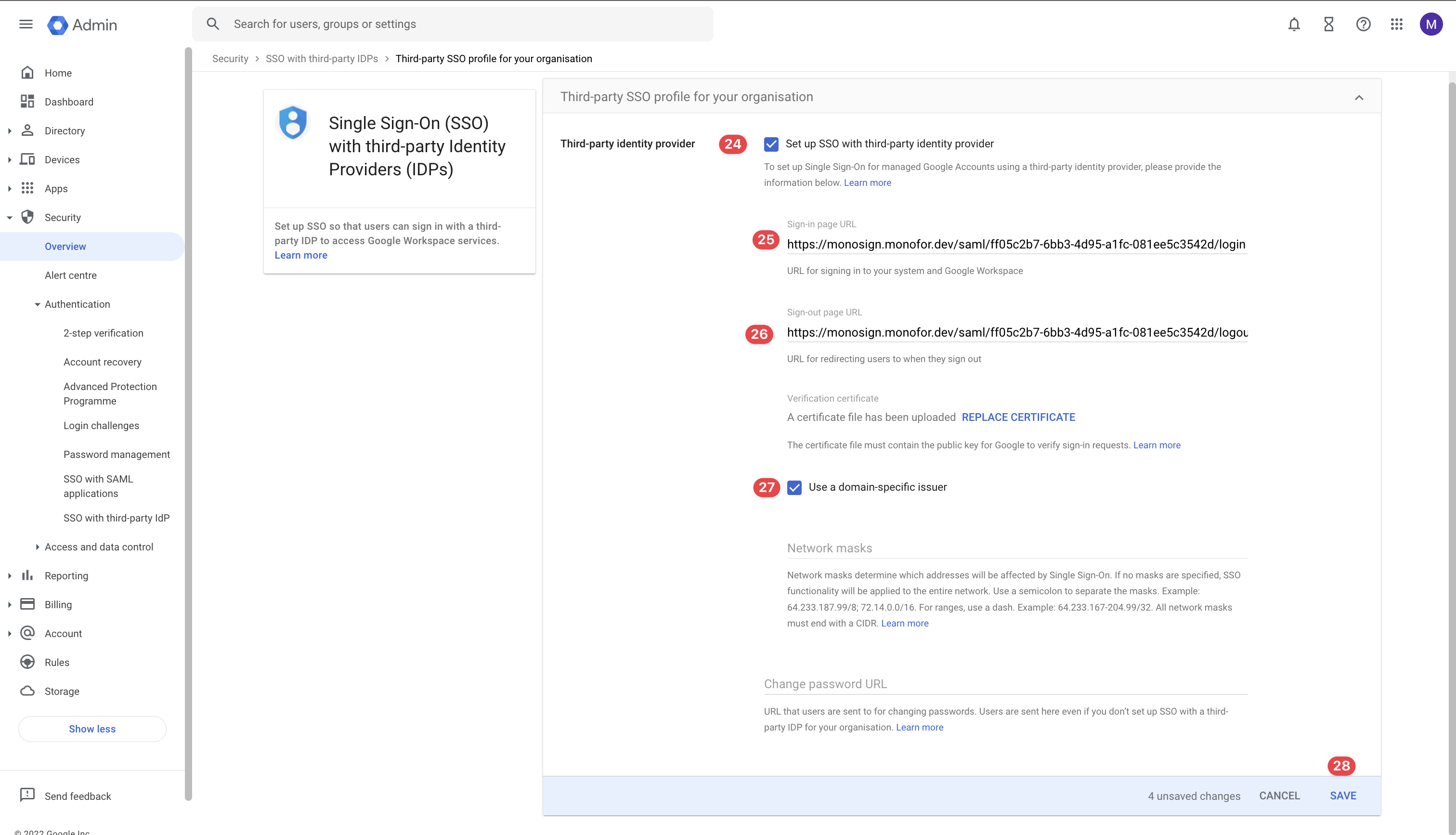
Third-Party SSO Profile for Your Organization Configuration
Once the inputs filled correctly and configurations completed please click the “Save“ button and navigate to SSO with third-party IDPs page.
The next step is “Manage SSO Profile Assignment“.
On the SSO with third-party IDPs page, you will see “Manage SSO profile assignments“ section to view and manage assignments for organizational units or groups. Please click the “Manage“ button as shown.
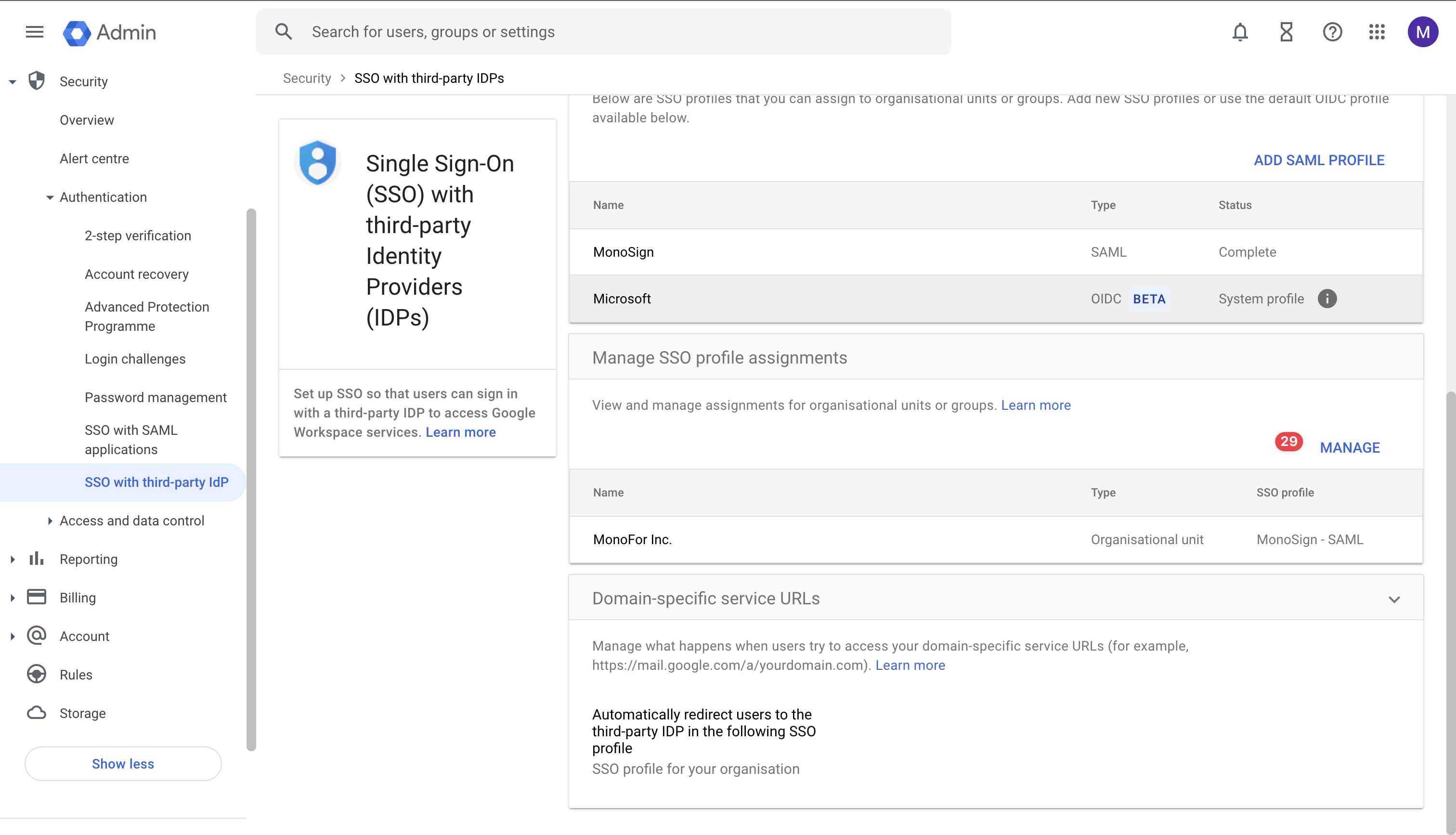
Manage SSO Profile Assignments
On the page, please click “Another SSO Profile“ button and choose the MonoSign-SAML profile as we created in the previous step. When all the other configurations completed as shown, please click the “Save“ button.
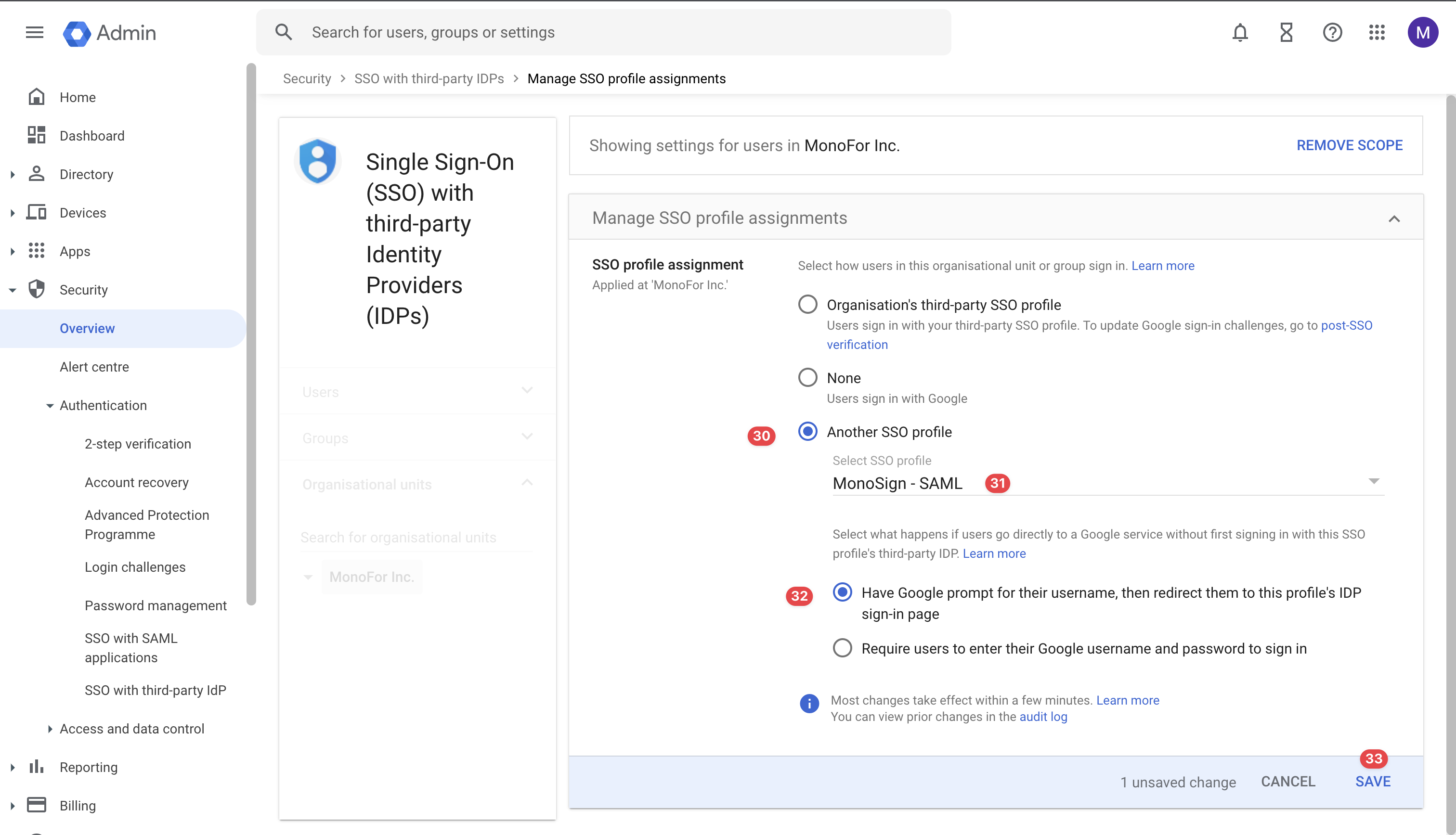
Manage SSO Profile Assignments Configuration
We are almost done on the Google Workspace configuration side. Let’s move to the last section.
The last section is “Manage domain-specific service URLS“ section. In this section, you can control what happens when users sign in using service URLs. Please click the “pen“ button to open “Manage domain-specific service URLS“ page.
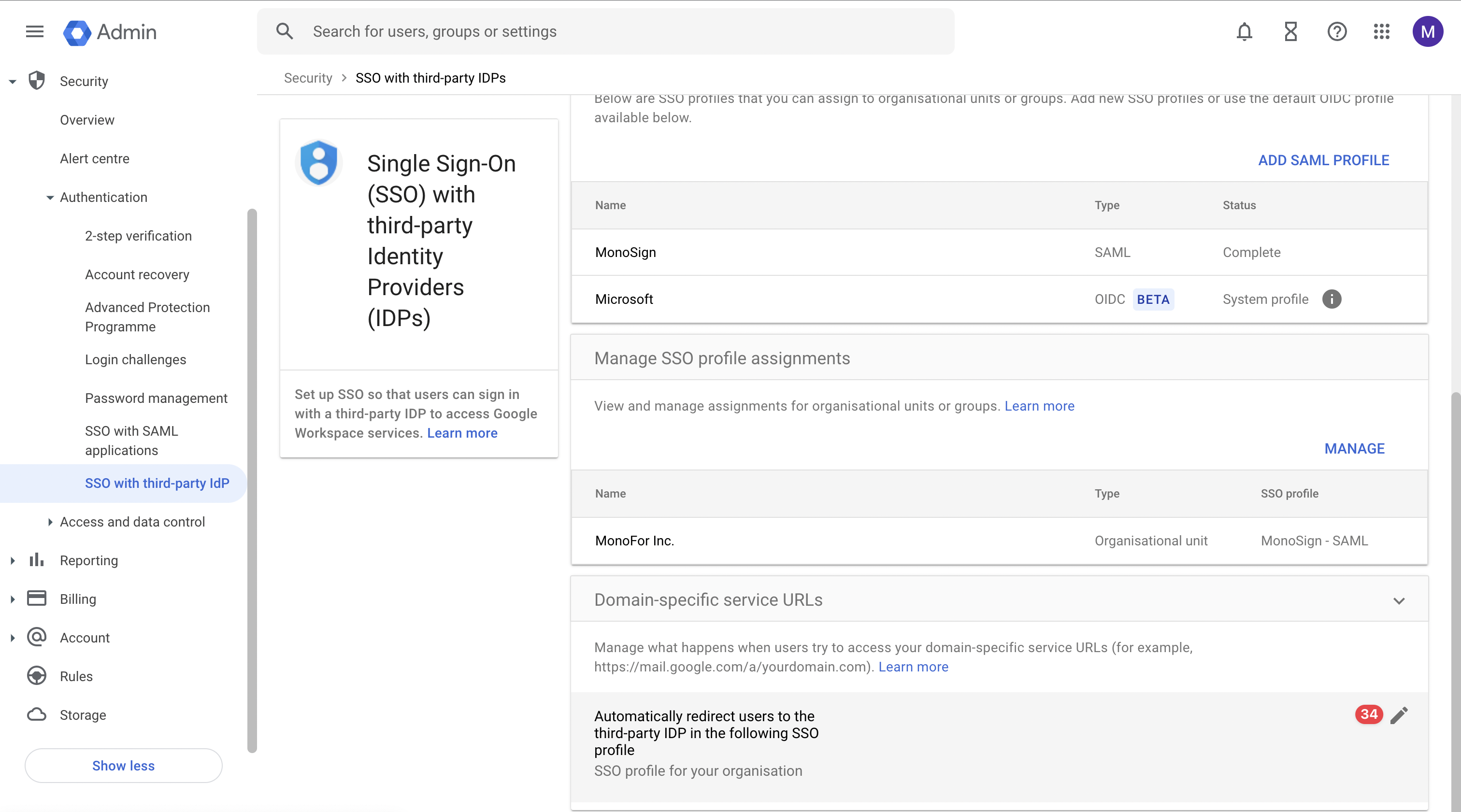
Manage Domain-Specific Service URLs
On the page, please click “Automatically redirect users to the third-party IdP in the following SSO profile“ button and choose the MonoSign SSO profile. When configuration is completed as shown, please click the “Save“ button.
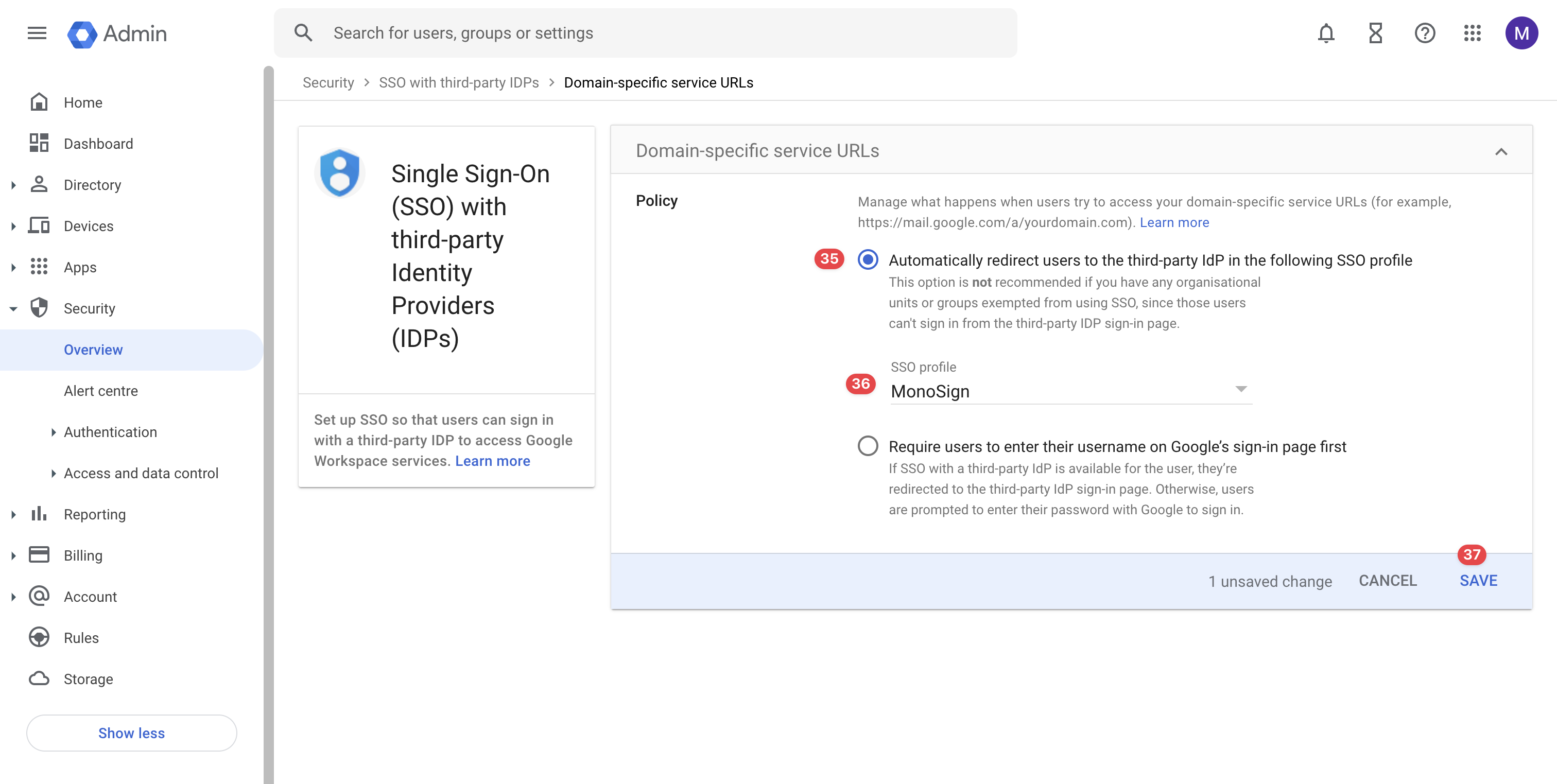
Manage Domain-Specific Service URLs Configuration
Configurations are completed on Google Workspace “SSO with third-party IDPs” Configuration page.
You need some information from Google Workspace MonoSign SAML Profile to configure SAML2 Settings on MonoSign Access Key Configuration Modal.
To get informations from Google Workspace, please click “MonoSign” SAML Profile as shown.
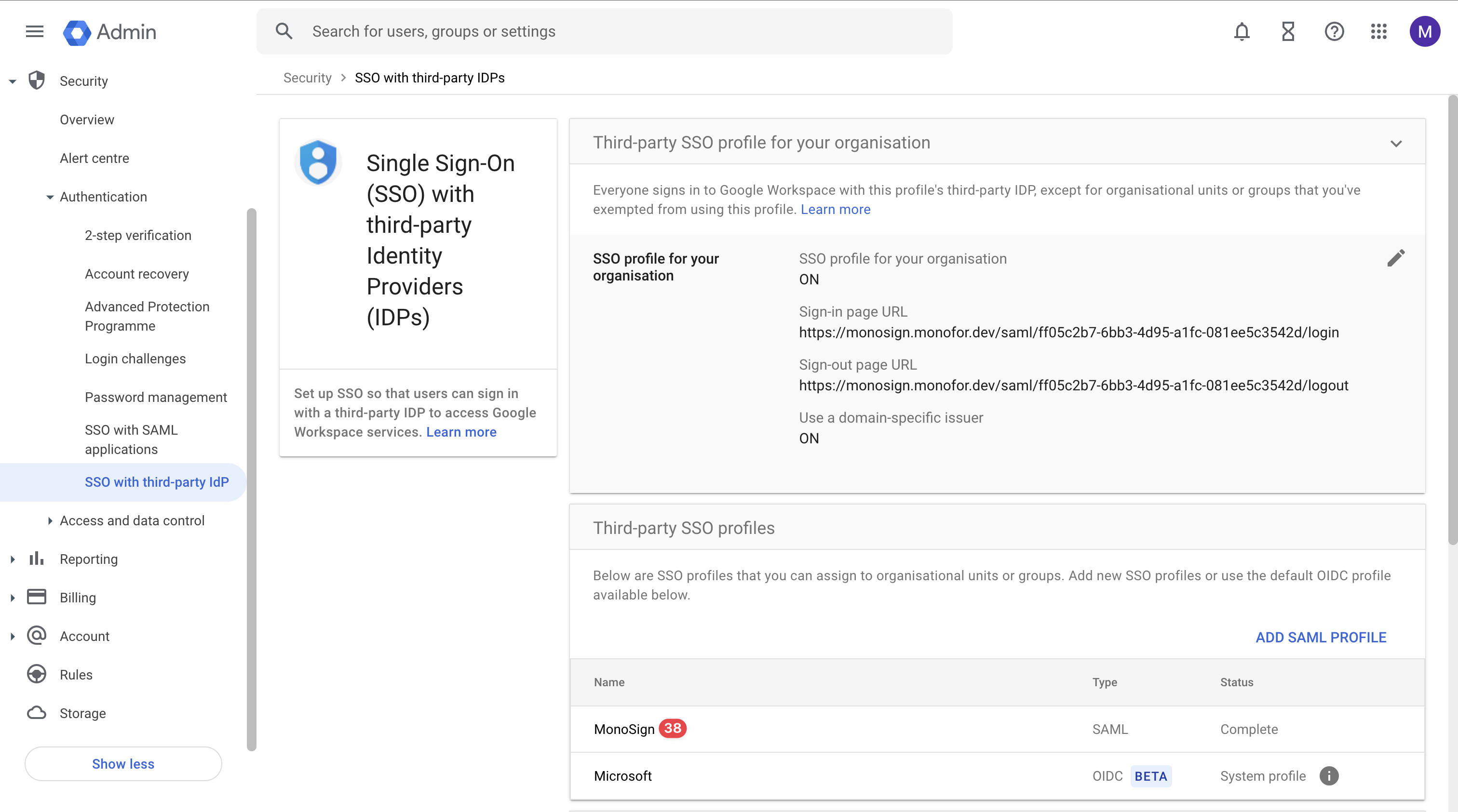
View MonoSign SAML Profile
Please copy Entity ID and ACS URL to complete the configuration on MonoSign SAML Settings modal.
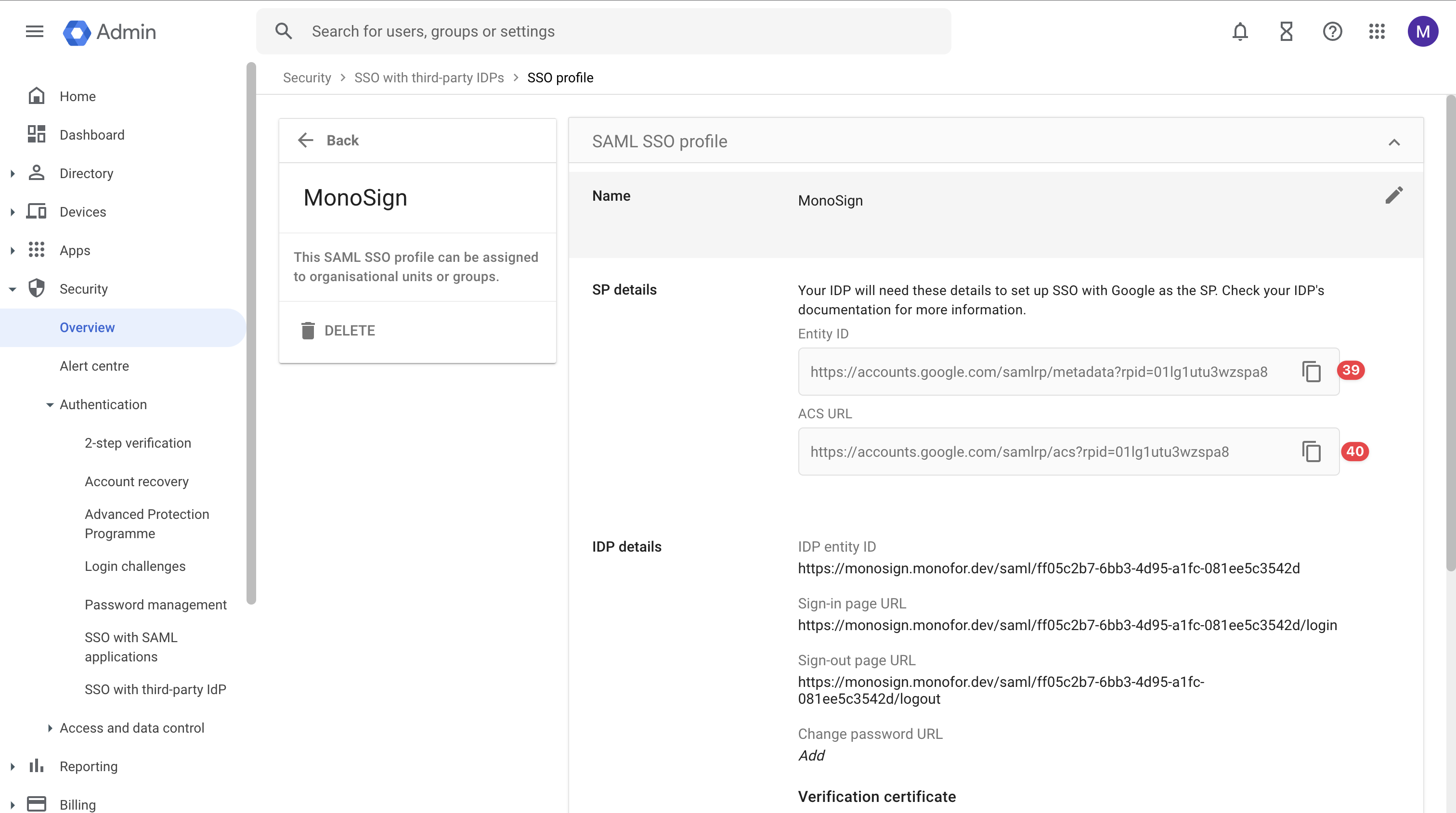
Information for SAML SSO Settings for MonoSign
Please fill in the inputs with the informations that copied from Google Workspace as shown.
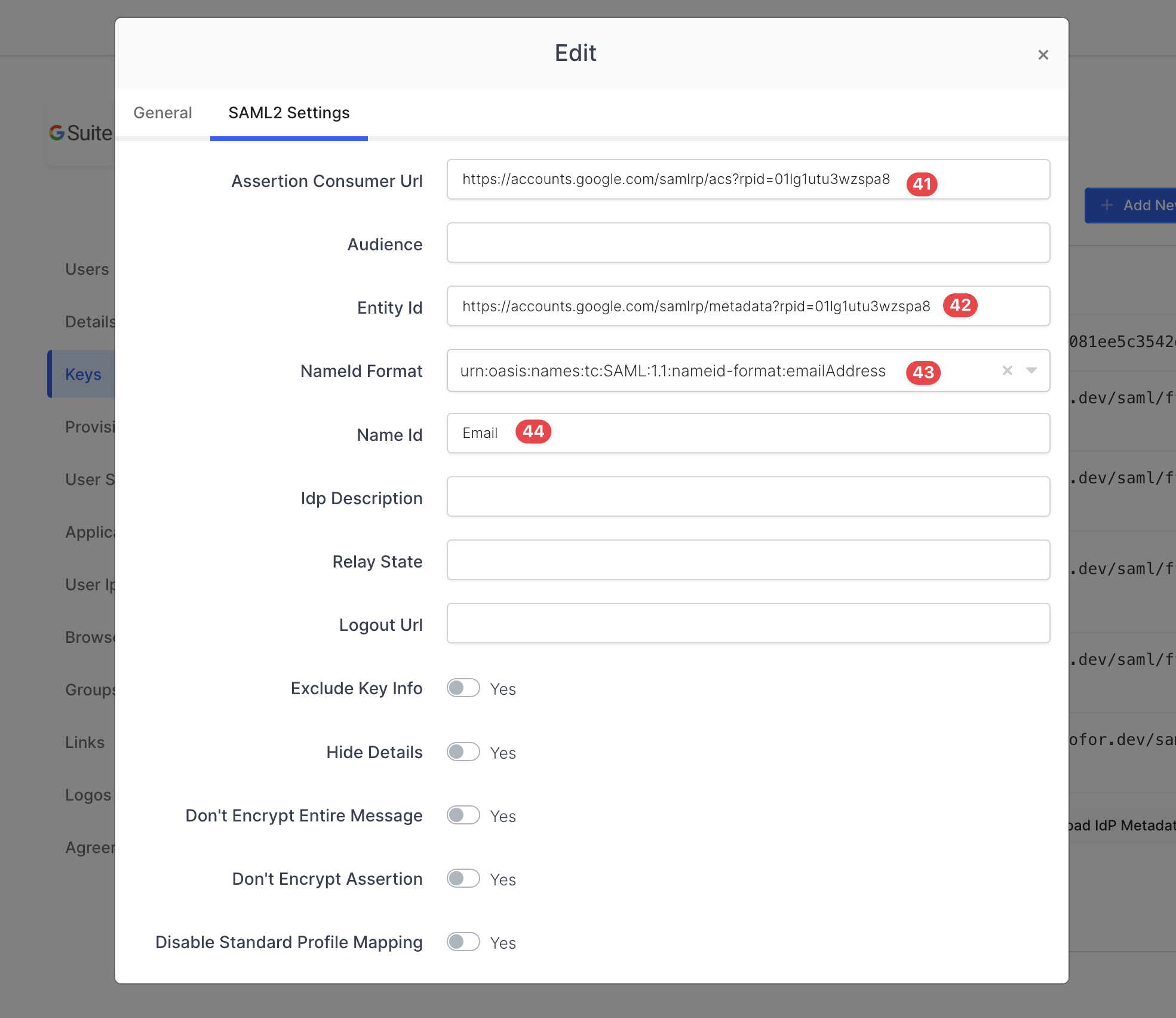
SAML2 Access Key Settings 1
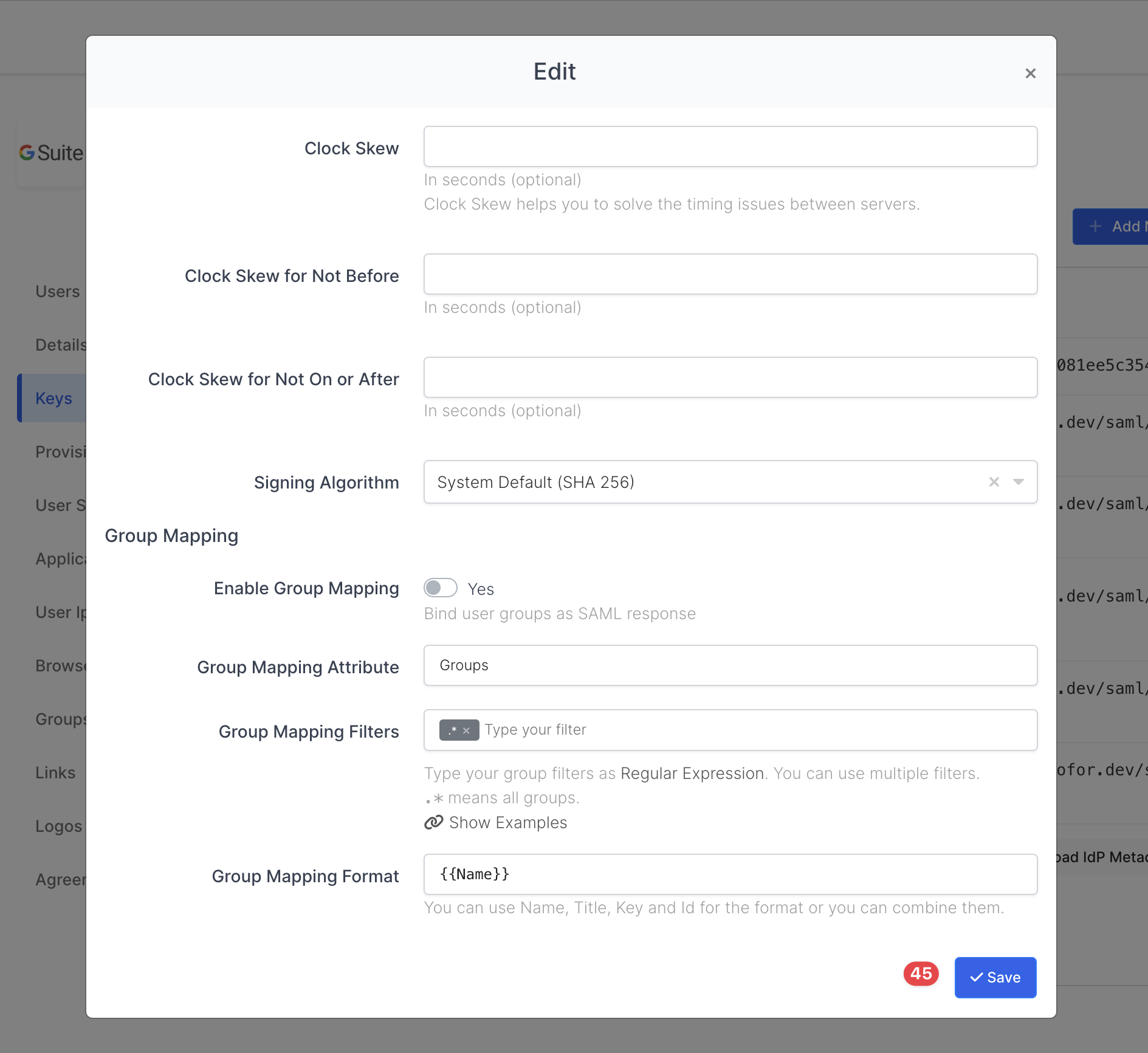
SAML2 Access Key Settings 2
It’s so important that you fill in the inputs correctly. Otherwise SAML authentication will not be performed.
SAML2 Settings | Value |
|---|---|
Assertion Consumer Url | |
Entity Id | https://accounts.google.com/samlrp/metadata?rpid=01lg1utu3wzspa8 |
NameId Format | urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
Name Id |
When all the inputs are filled, please click the “Save“ button.
Configurations are completed on MonoSign Google Workspace Application Key page and Google Workspace SSO with third-party IdP page.
Now you can test if SSO SAML Login works with MonoSign.
Please create a user named “gsuiteuser“on MonoSign and Google Workspace with the same mail address. Assign the user on “Google Workspace” application created on MonoSign.
Please open “https://accounts.google.com/“ address on your browser and type username email address as shown.
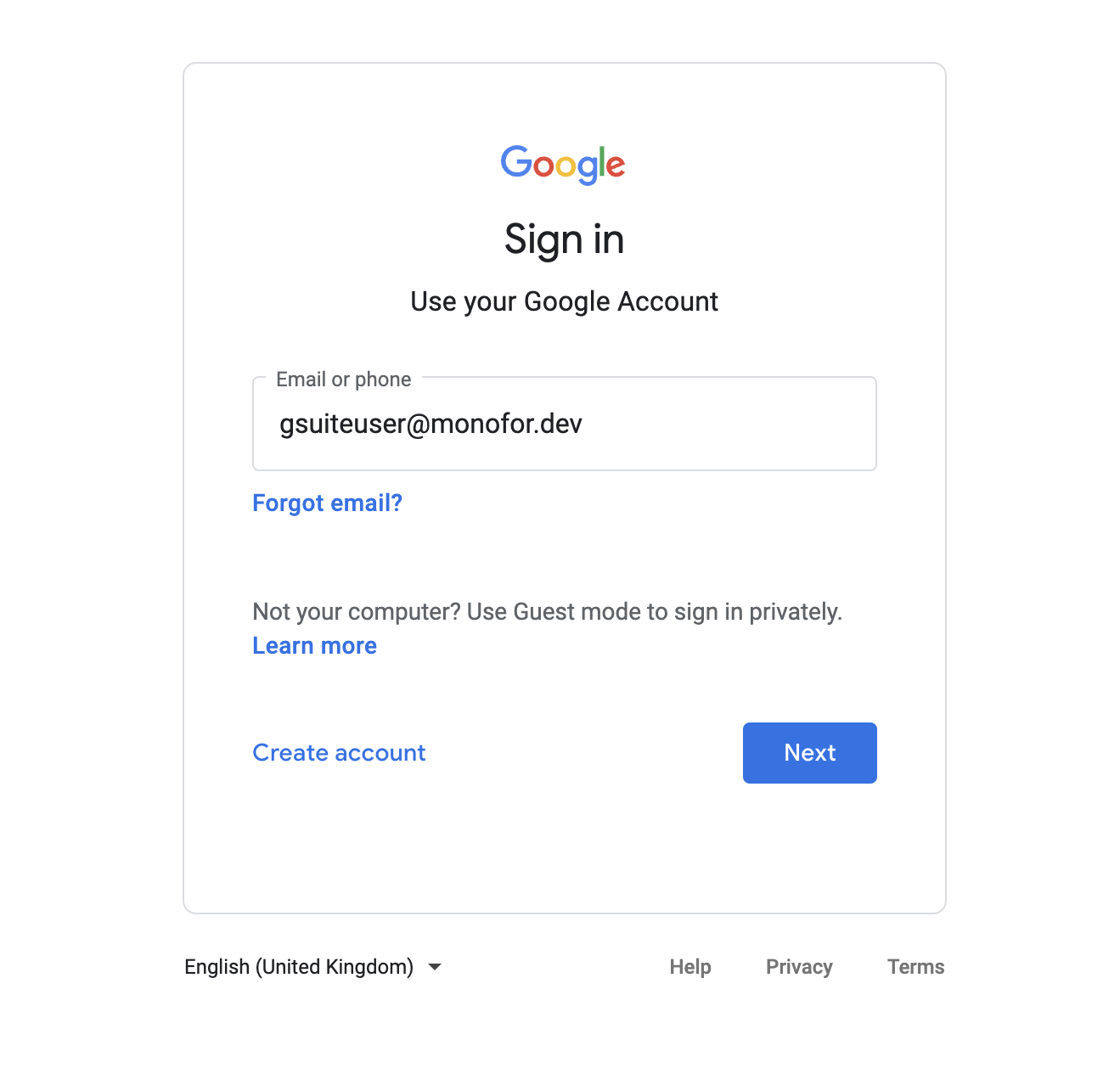
Login to Google Workspace Account
When “Next“ button clicked, you will navigate to MonoSign login page.
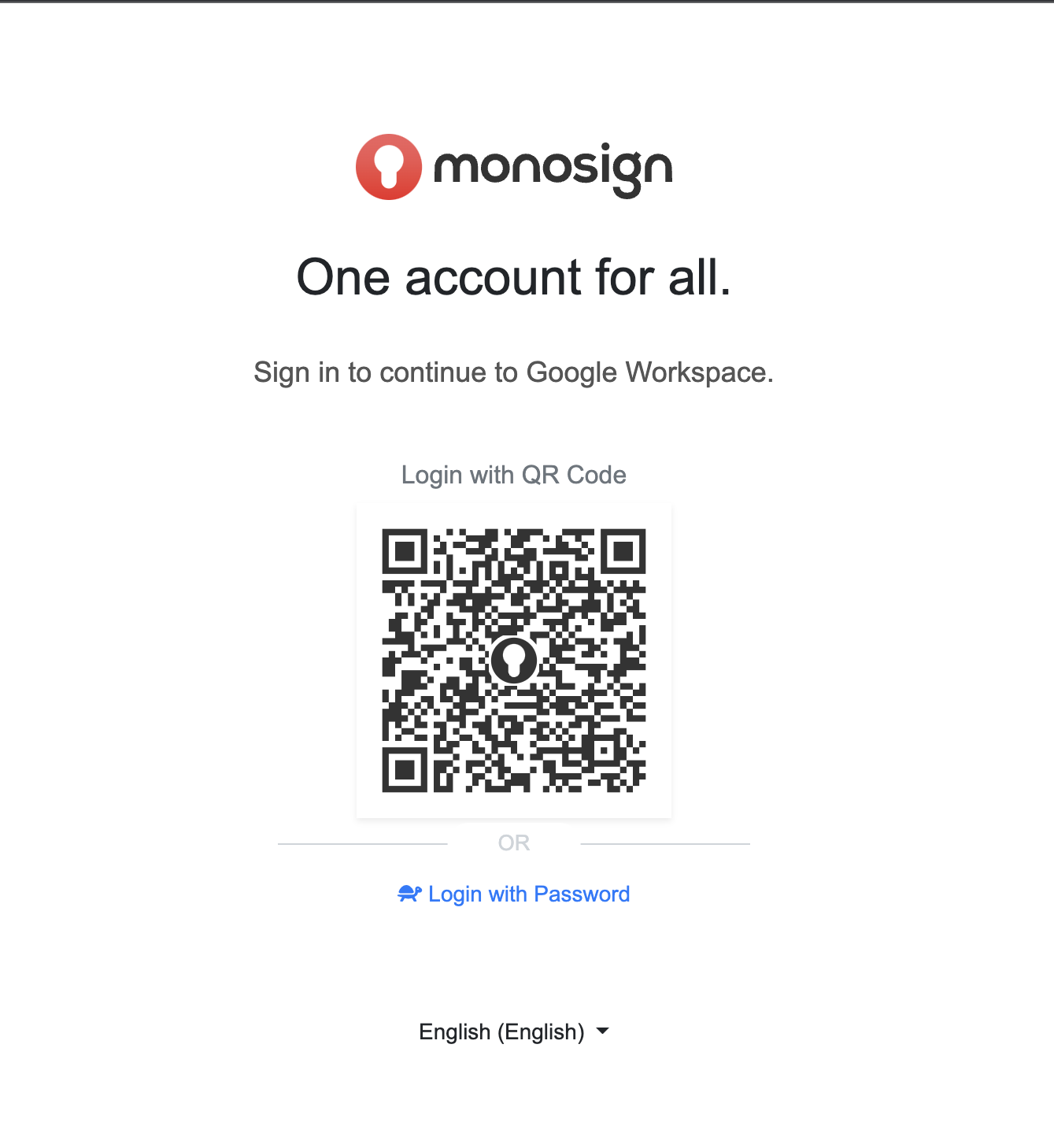
Login Google Workspace with MonoSign
Now you can login with your MonoSign username and password. You will navigate to your Google Workspace account as shown.
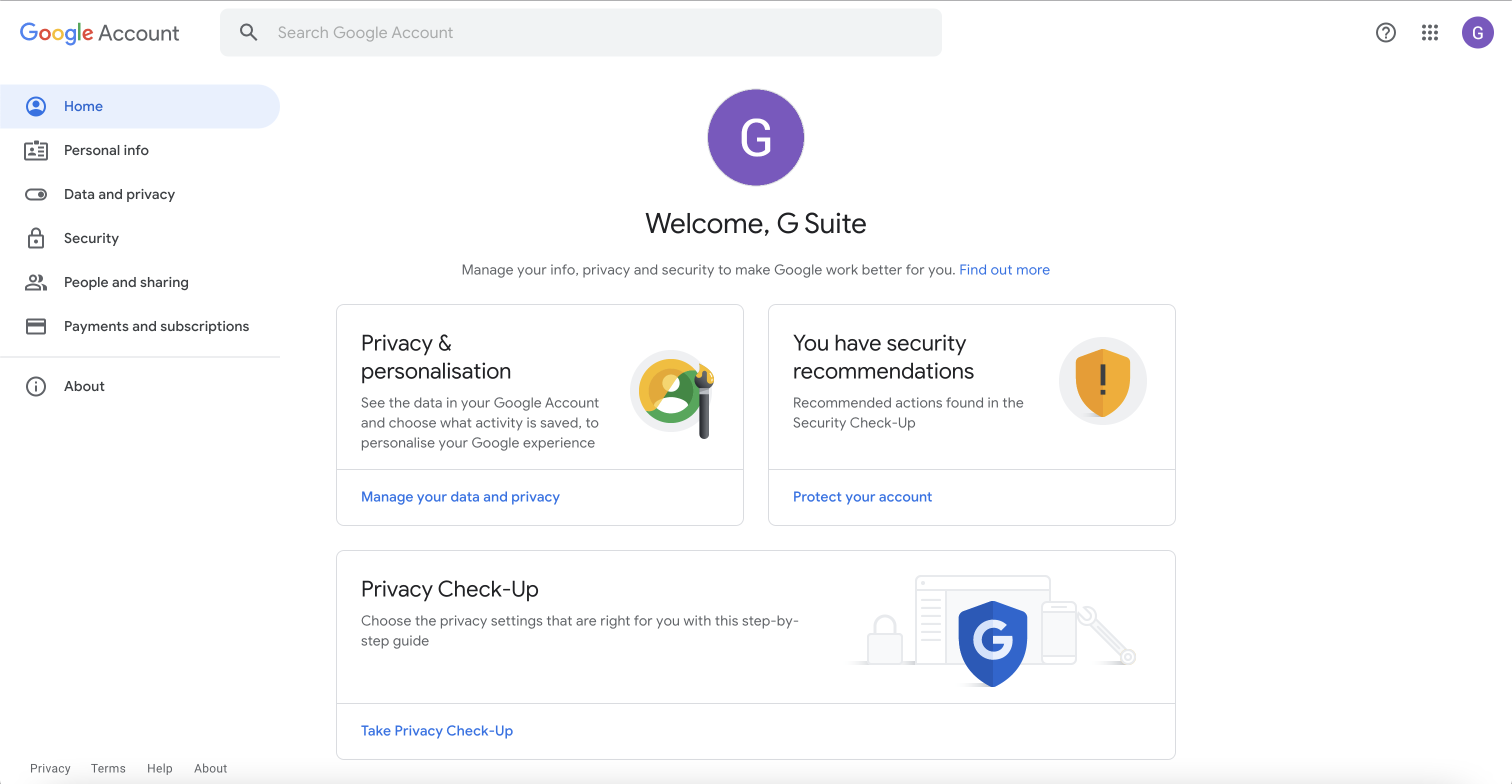
Logged In Google Workspace Account with MonoSign
If you logged in to your Google Workspace account with MonoSign, it means everything seems perfect and done well.
