Palo Alto SSL-VPN SAML Integration
This document explains how to implement Monosign with Palo Alto. It covers Single Sign-On. Before you continue, it is better to start with Palo Alto’s Single Sign-On implementation page.
Monofor has no responsibility to do Palo Alto configurations. If you need support please contact Palo Alto Support Services.
📑 Instructions
This documentation contains 4 main steps for integration.
Creating an Application on Monosign
Configuration Single Sign-On for Palo Alto
Assign a user to the Palo Alto application
Sign In Test
1- Creating an Application on Monosign
Create application on Monosign and configure your access policy. Once you create, click “Keys” and add a new Access Key for SAML Key for access.
This information will be necessary during the configuration of the SAML application.
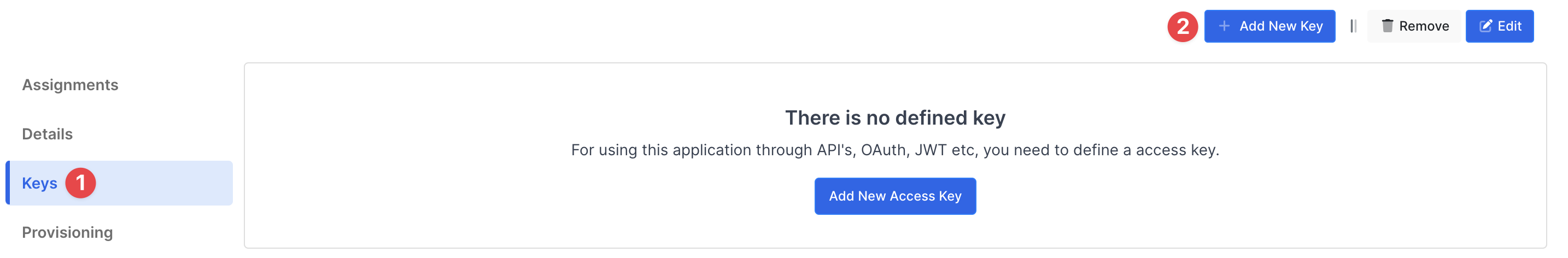
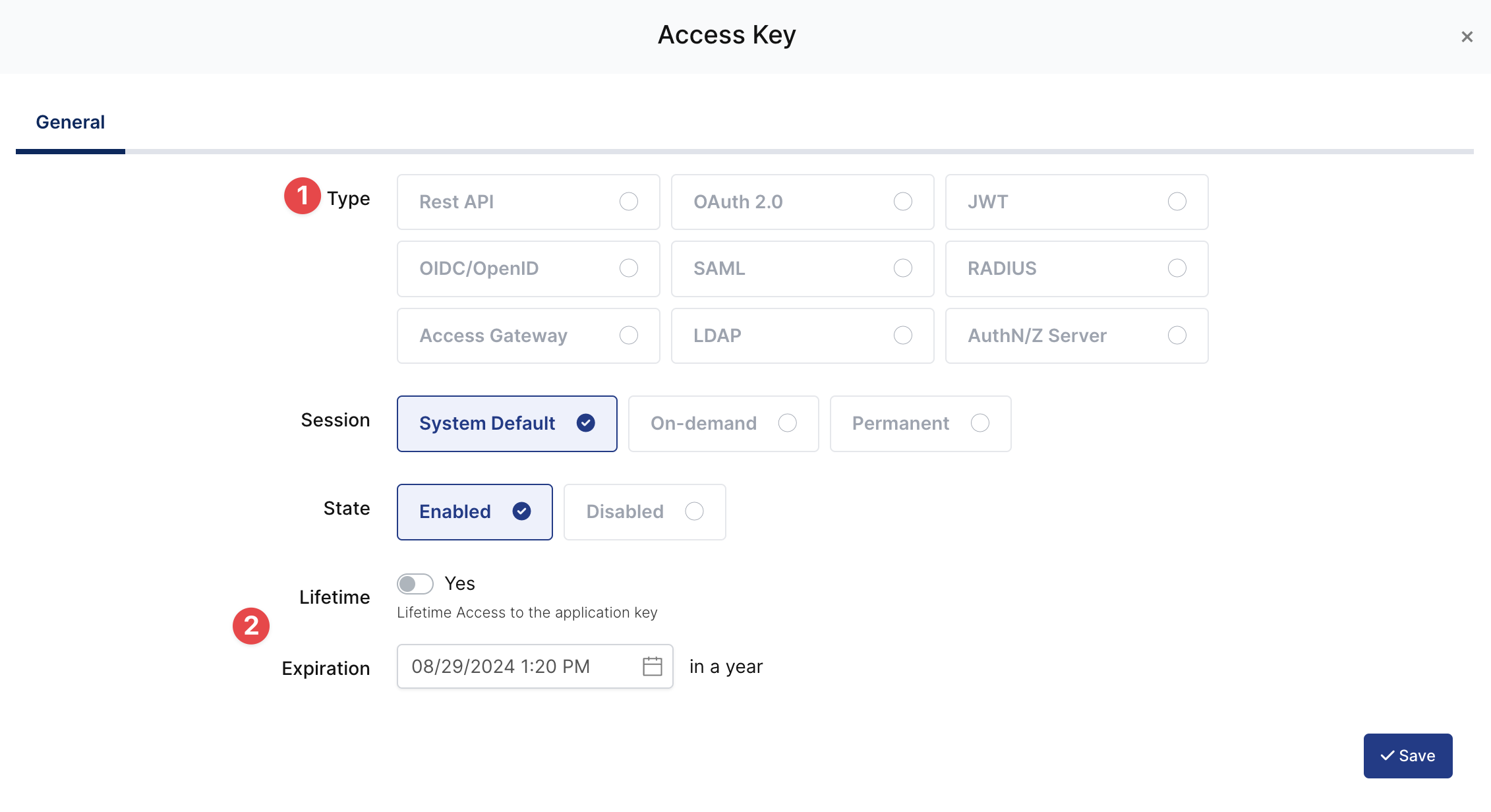
Property | Value | Options |
|---|---|---|
Key Type | SAML | Rest API, OAuth 2.0, JWT, OIDC/OpenID, SAML, RADIUS, Access Gateway, LDAP, AuthN/Z Server |
Expiration | Lifetime | Lifetime or Specific Date/Time - By Default Lifetime is Enabled. |
Configuration details for the Palo Alto application are provided as follows:
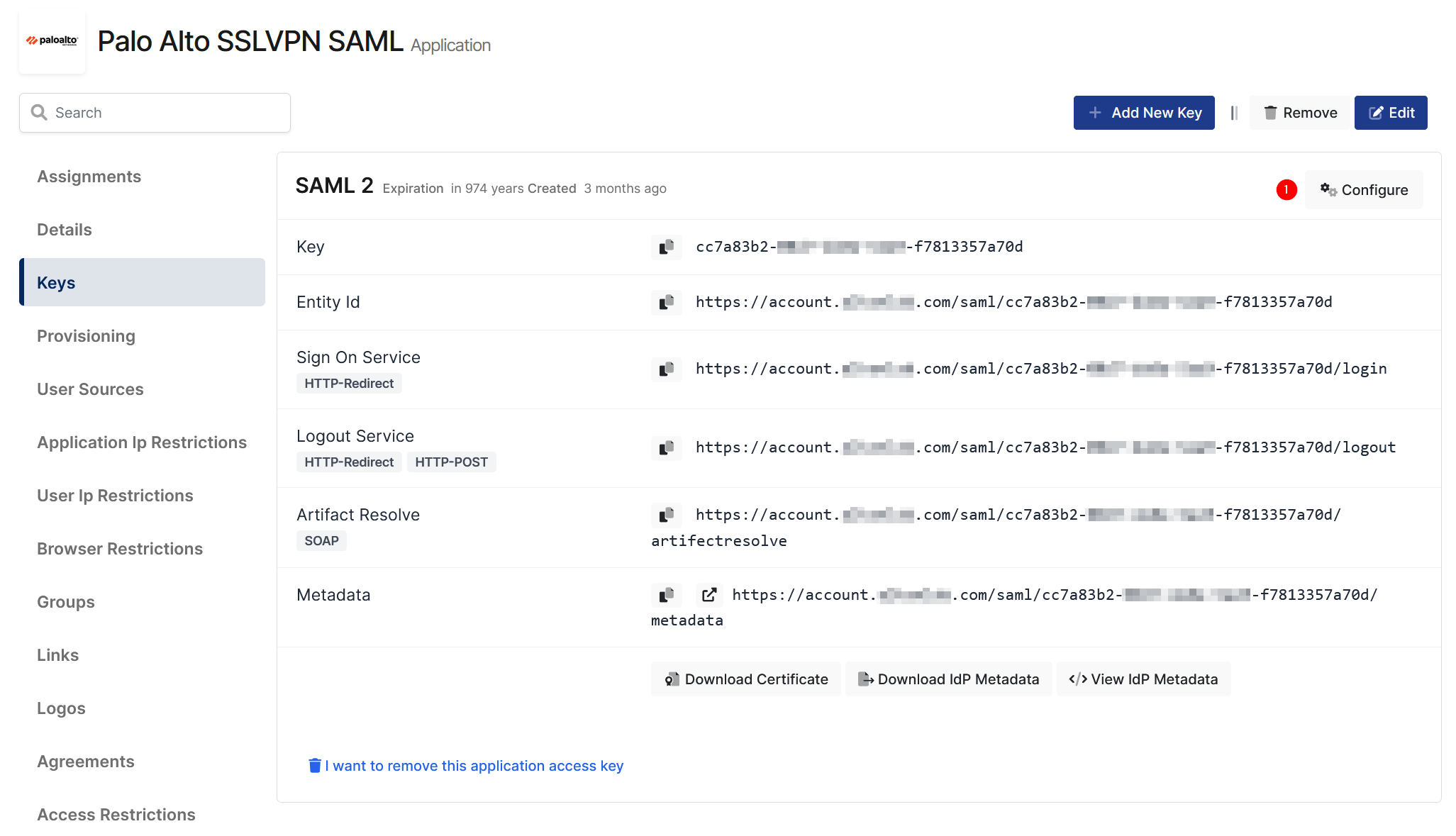
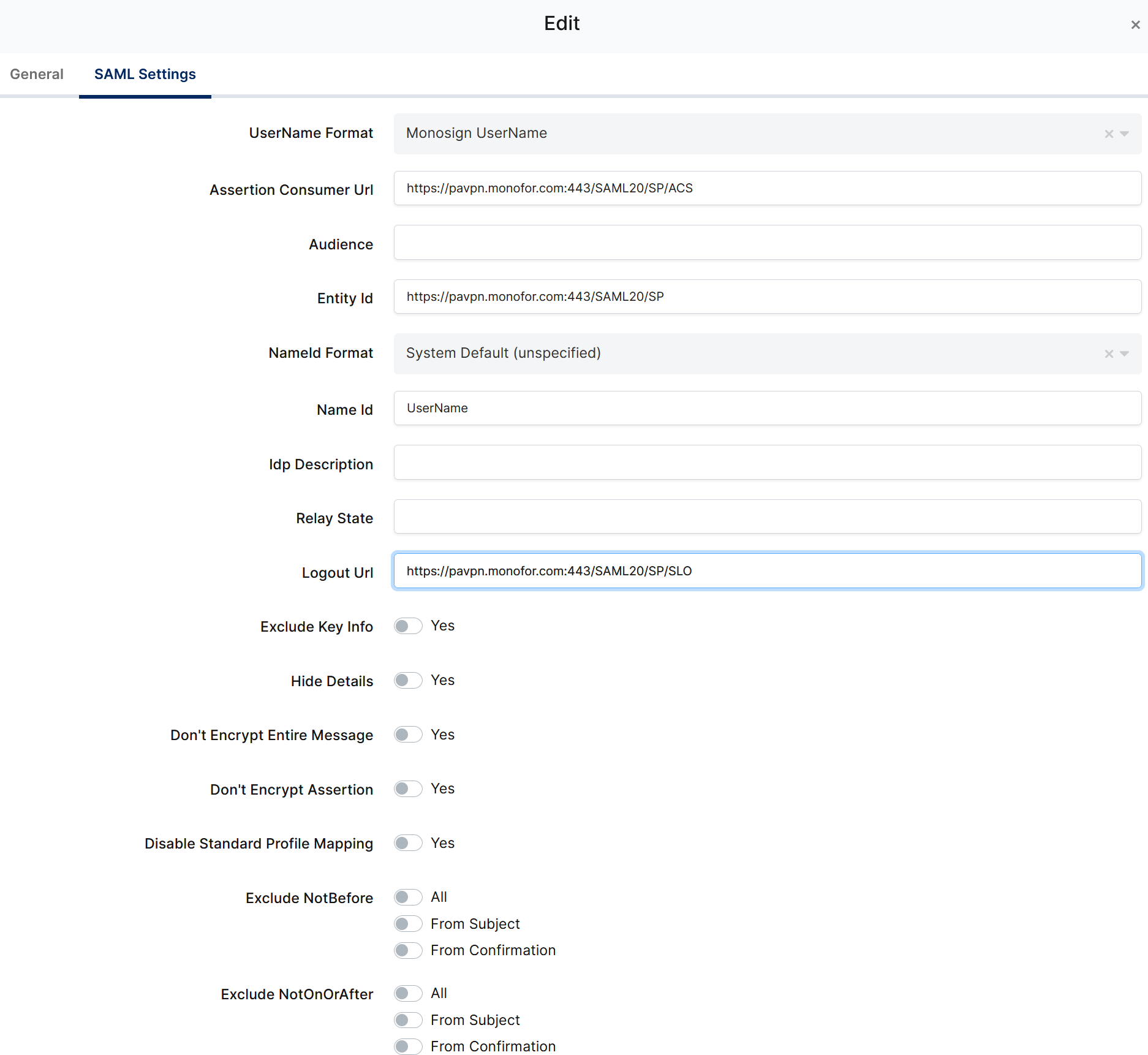
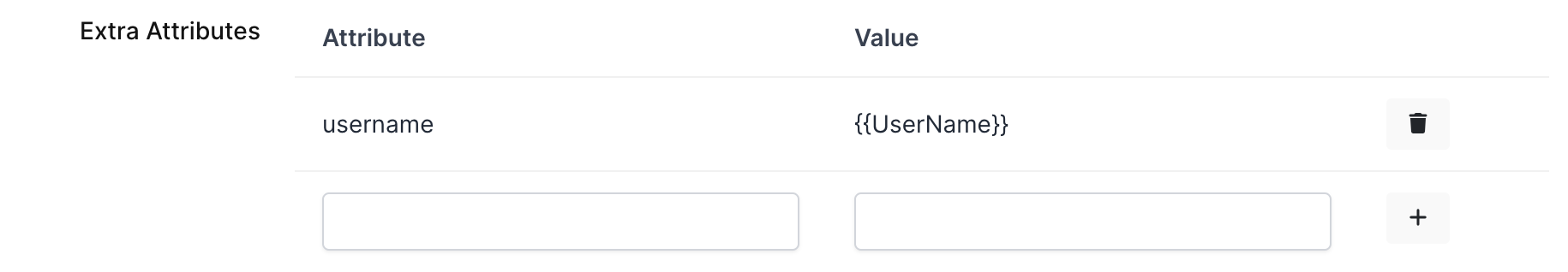
Change ACS(Assertion Consumer Url), Entity Id, Name Id, Logout Url and Extra Attributes.
Property | Value |
|---|---|
Assertion Consumer Url |
|
Entity Id |
|
Name Id |
|
Logout Url |
|
Extra Attributes |
|
Above information can be download from Palo Alto devices from SP metadata file.
To ensure that the application has access to user groups, follow these steps:
If the application hasn't been configured yet, click the “Edit” option for the application.
In the application settings, navigate to the “Source, Provider, and Profile” tab.
Configure the “User Access Type“ and “User Group Access Type” as “Only Assigned Users.”
Configuring this setting will allow the application to access by user groups when users sign in.

Property | Description | Options |
|---|---|---|
User Access Type | Defines which Users will access to this application. | Only Assigned Users |
User Group Access Type | Defines application’s user group access | Only Assigned Users |
Profile Access Type | Defines Application’s user’s profile access | Restricted - Only restricted user profile attributes |
2- Configuration Single Sign-On for
As it highlighted at the beginning of document, please check out the Palo Alto’s SAML configuration page first.
Please add your SAML settings to the application. The following information is needed for your configuration.
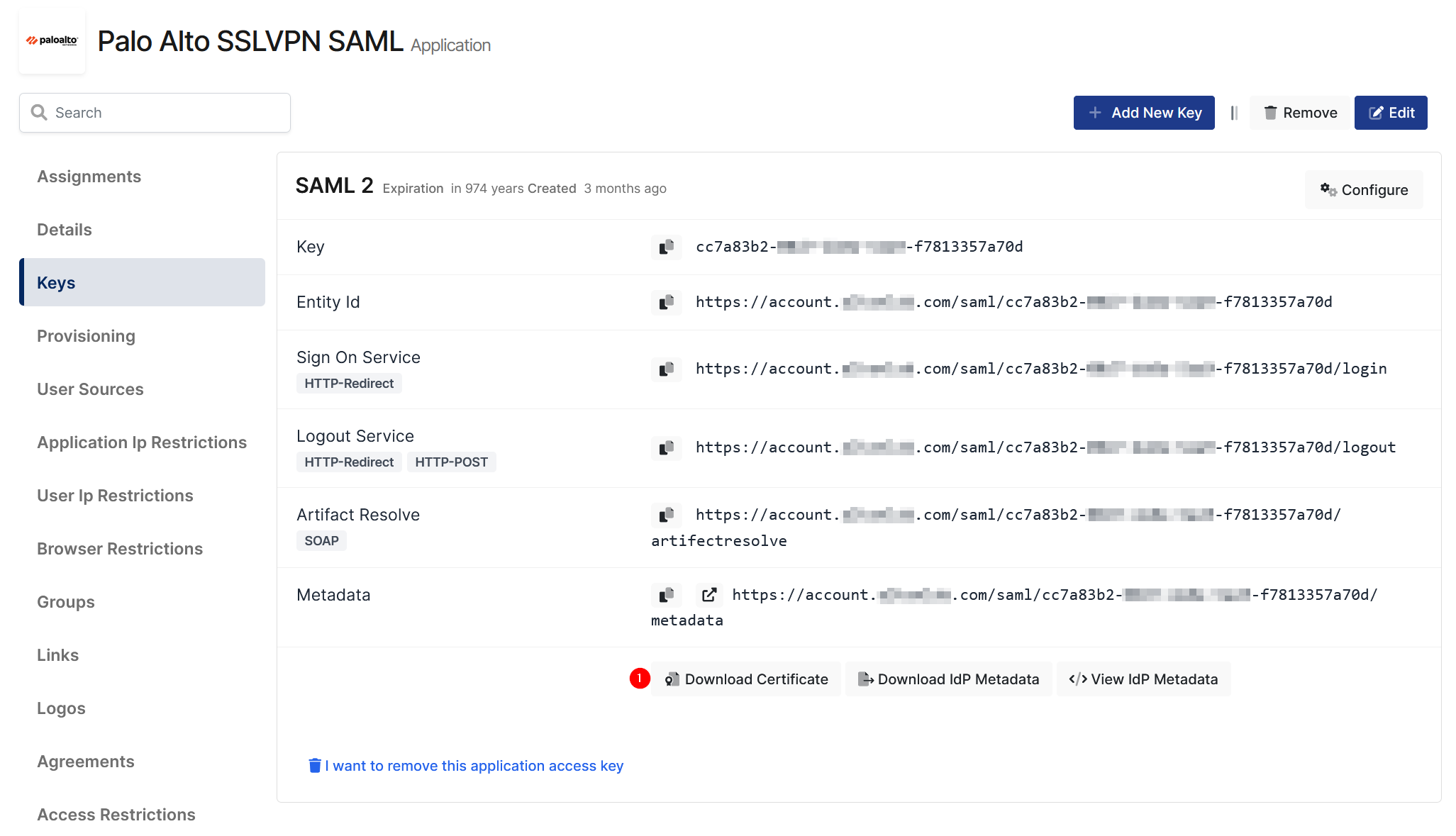
a. Upload IdP Certificate
Download IdP certificate as shown in the below picture from Monosign Application Key detail
Go to Device → Certificate Management → Certificates and click Import downloaded certificate to Palo Alto device.
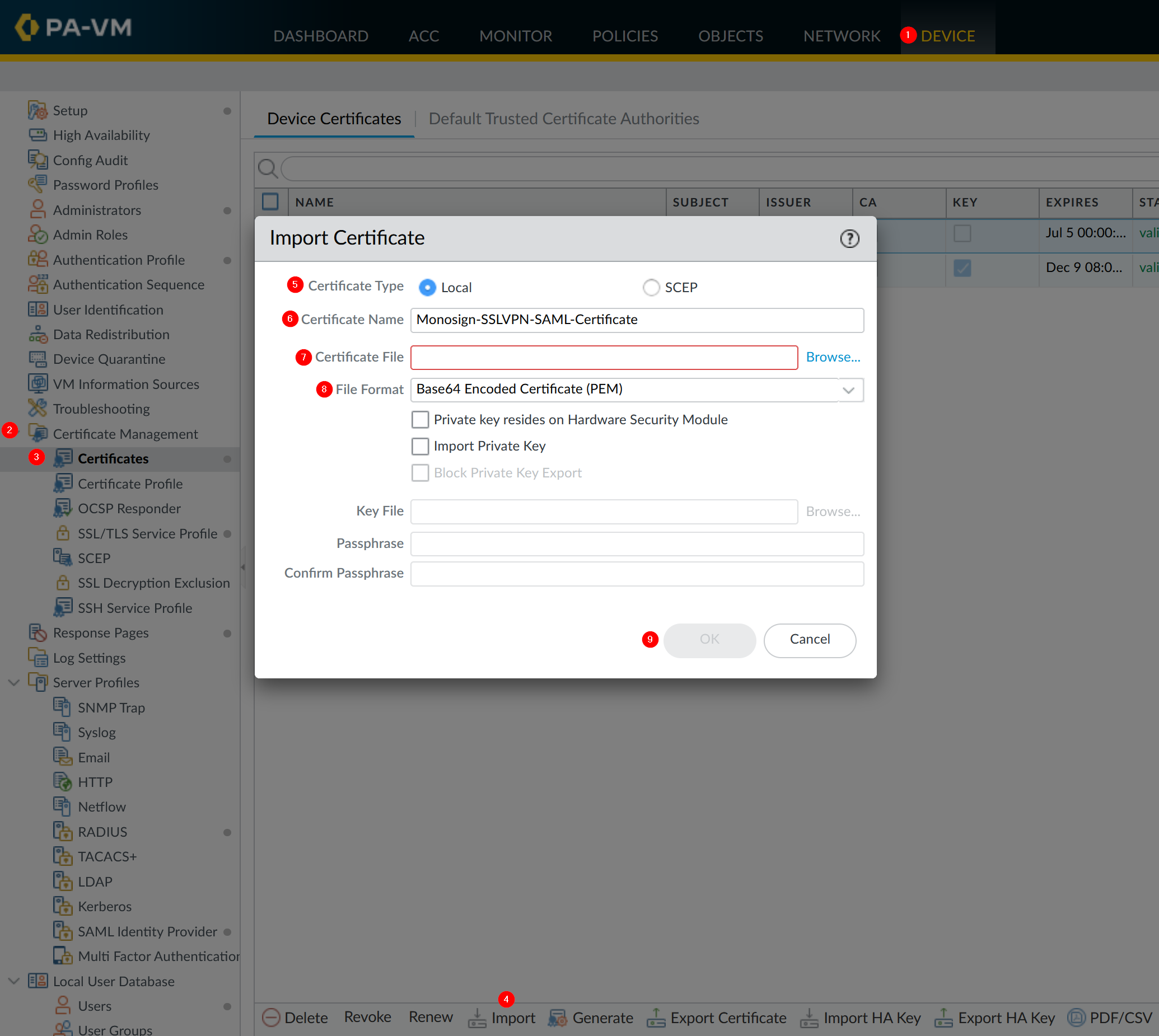
Property | Value |
|---|---|
Certificate Type |
|
Certificate Name |
|
Certificate File |
|
File Format |
|
b. Configure SAML Server Profile
Go to Device → Server Profiles → SAML Identity Provider and click Add.
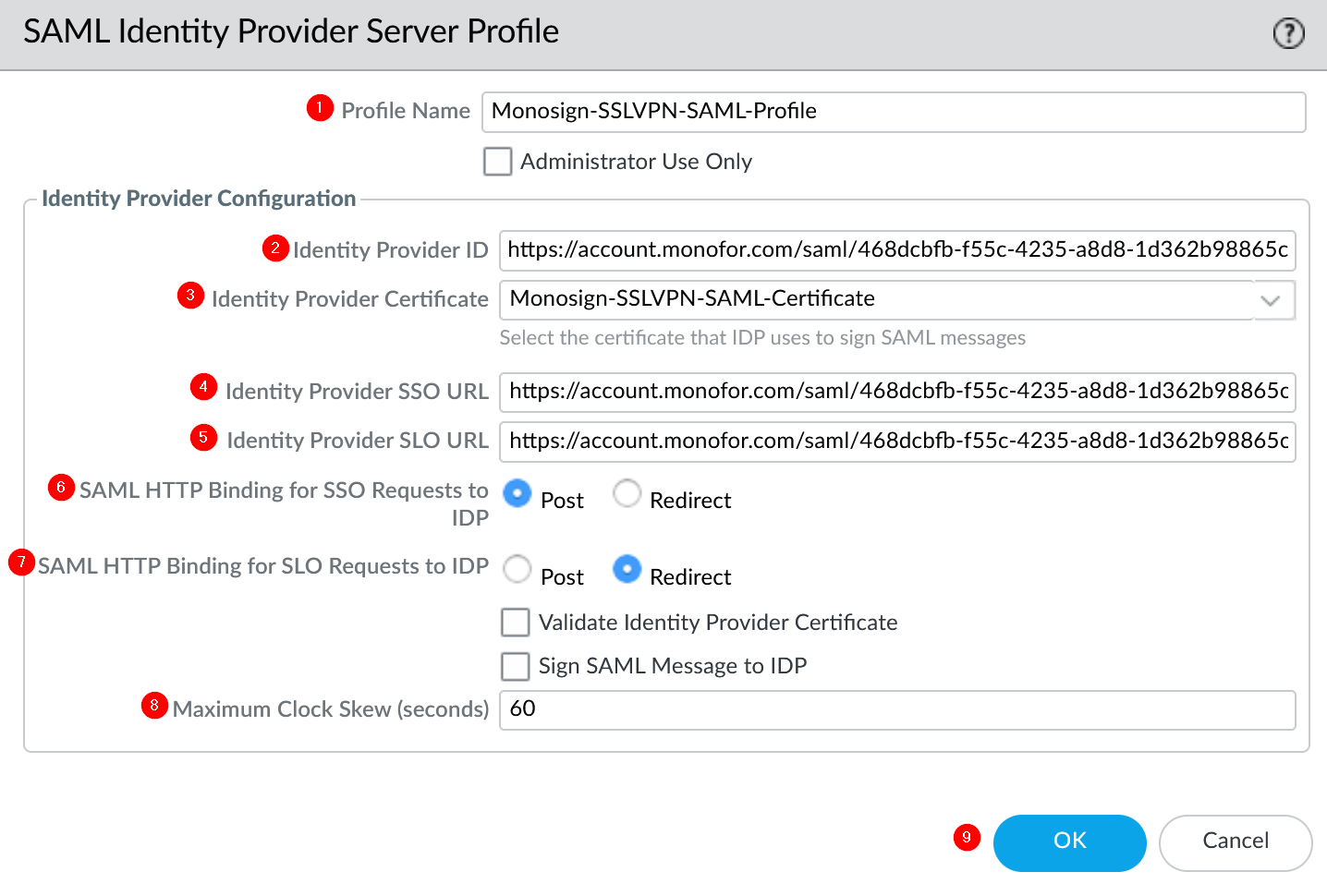
Property | Value |
|---|---|
Profile Name |
|
Identity Provider ID |
|
Identity Provider Certificate |
|
Identity Provider SSO URL |
|
Identity Provider SLO URL |
|
SAML HTTP Binding for SSO Requests to IDP |
|
SAML HTTP Binding for SLO Requests to IDP |
|
Maximum Clock Skew (seconds) |
|
c. Configure Authentication Profile
Go to Device → Authentication Profile and click Add.
Authentication Profile - Add
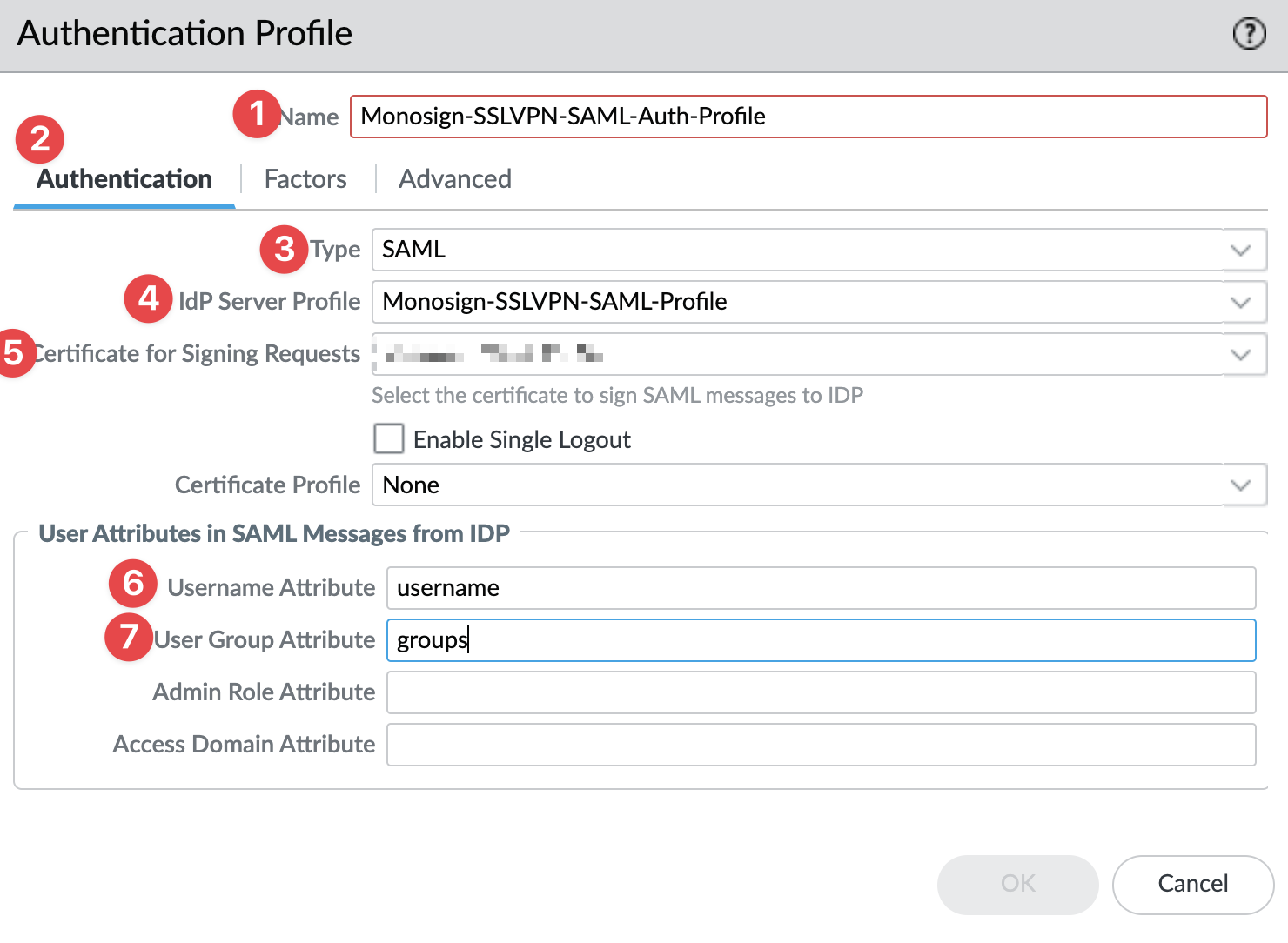
Authentication Profile - Authentication
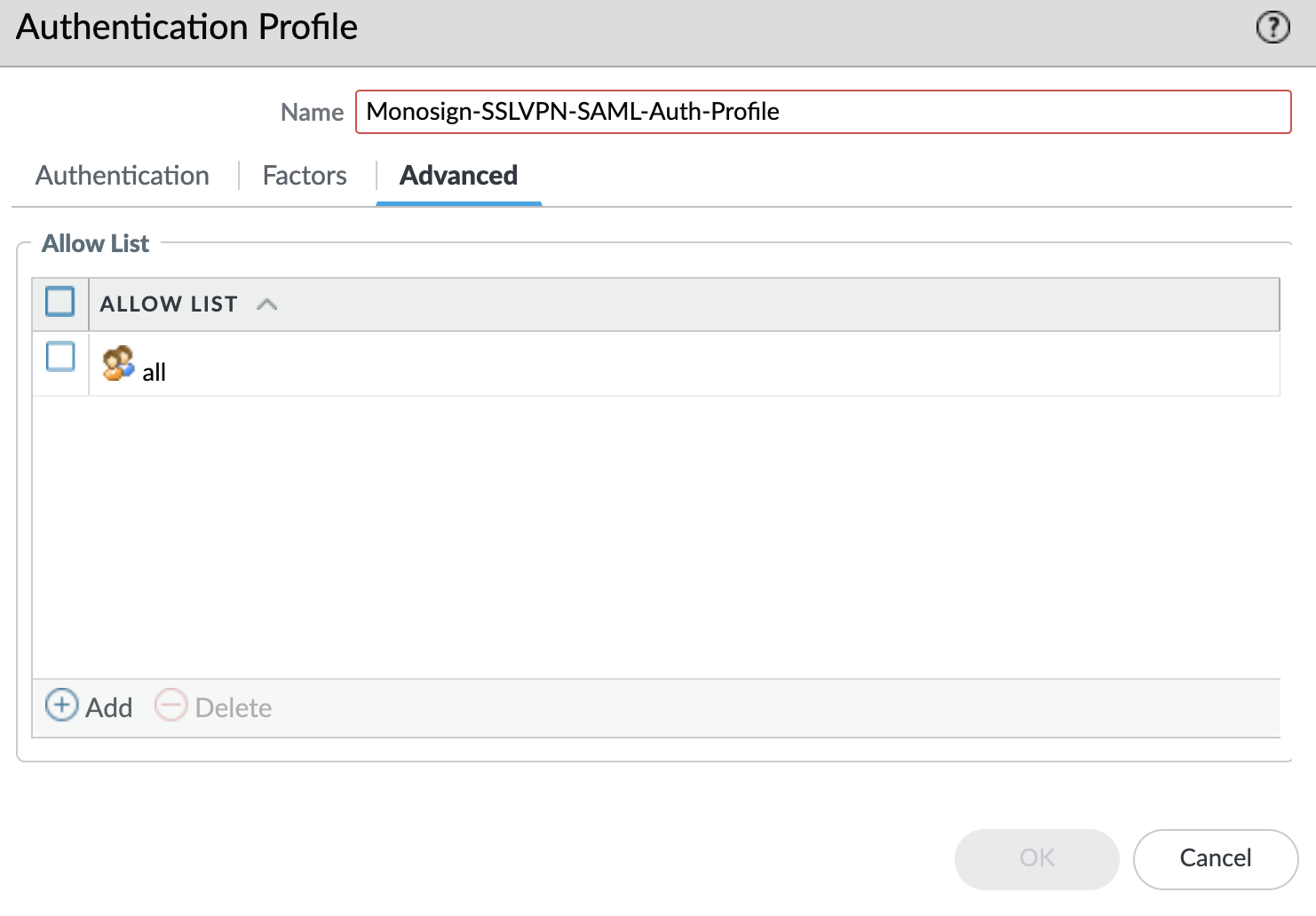
Authentication Profile - Advanced
Property | Value |
|---|---|
Name |
|
Type |
|
IdP Server Profile |
|
Certificate for Signing Requests |
|
Username Attribute |
|
User Group Attribute |
|
d. Configure GlobalProtect
Go to Network → GlobalProtect → Portals → Portal Config → Authentication → Client Authentication on the Palo Alto Network devices management UI.
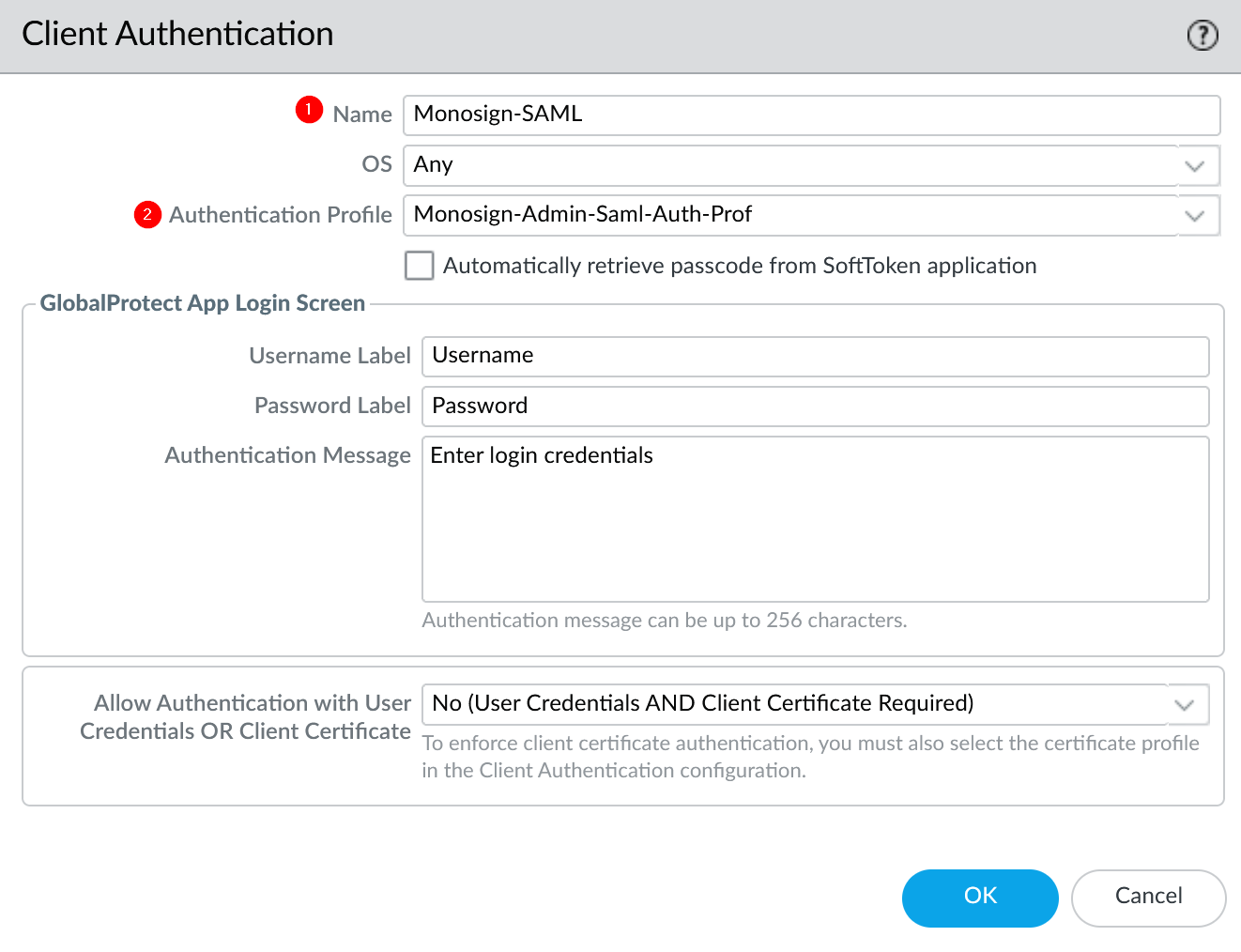
Property | Value |
|---|---|
Name |
|
Authentication Profile |
|
Go to Network → GlobalProtect → Gateways → Gateway Config → Authentication → Client Authentication on the Palo Alto Network devices management UI.

Commit changes to apply on Palo Alto Devices.
Now, go back to Monosign and give access to your users and try login.
3- Assign a user to the Palo Alto SSL-VPN application
Please follow below instructions on how to assign a user to the application. In this example john.smith will assign to the application access.
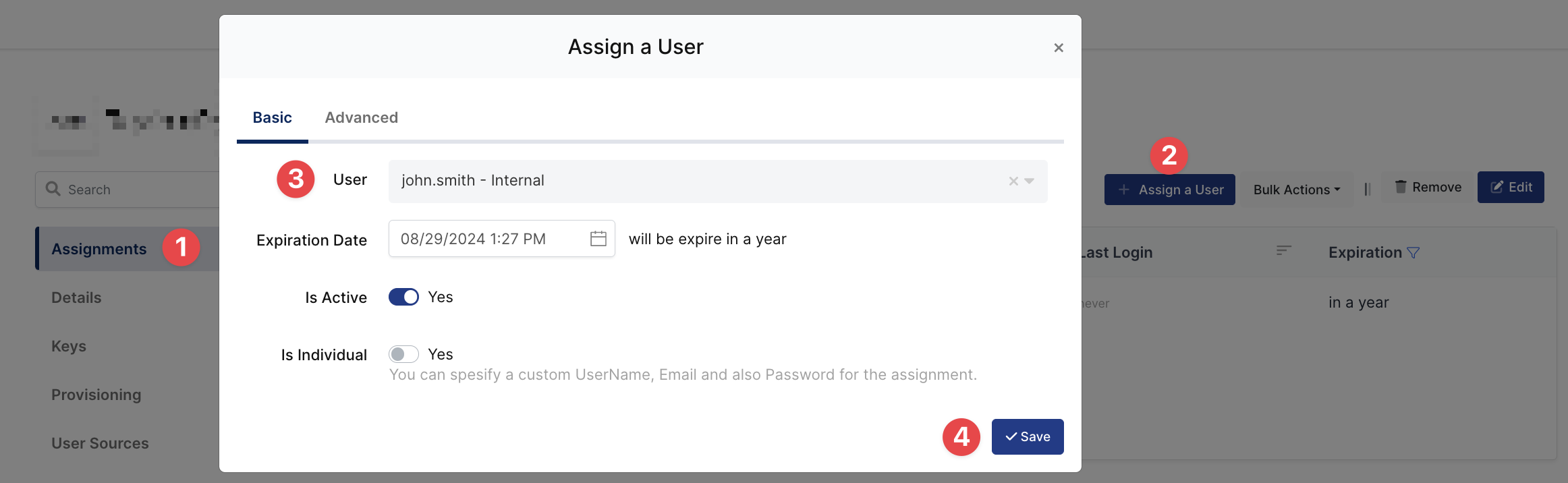
4- Sign In Test
a. Portal Login
Now try login to GlobalProtect Portal. Navigate to the Palo Alto Portal login page. If everything is well configured, the page will be redirected to Monosign’s login page. It can be log in passwordless with QR code or type username and password.
b. Client Login
Now try login to GlobalProtect Client. Navigate to the Palo Alto Portal login page. If everything is well configured, the page will be redirected to Monosign’s login page. It can be log in passwordless with QR code or type username and password.