Pipedrive SAML Integration
This document explains how to implement MonoSign with Pipedrive. It covers Single Sign-On. Before you continue, it is better to start with AWS’s Single Sign-On implementation page.
View Pipedrive SAML Metadata
In order to configure the SAML key on MonoSign for Pipedrive SAML, you need to have various information provided by Pipedrive.
First, navigate to Company Settings from right top menu.
Next, Click Single Sign On from the sidebar.
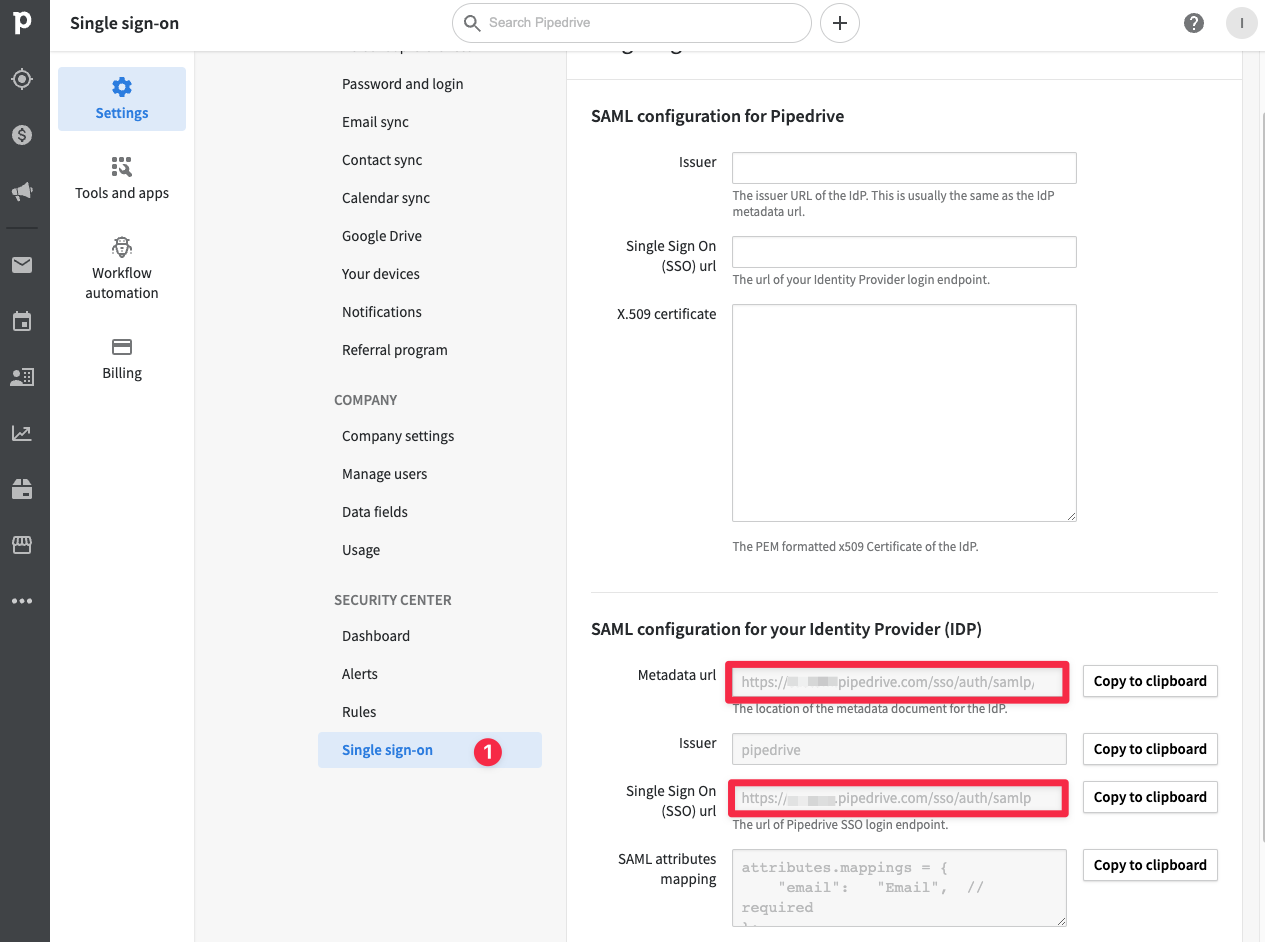
At the bottom of the page you will see SAML configurations which you will use in the MonoSign.
For now, we will stop here on the Pipedrive side and create a MonoSign Application and related SAML key by using the information provided by Pipedrive.
Creating an Application and Access Key on MonoSign
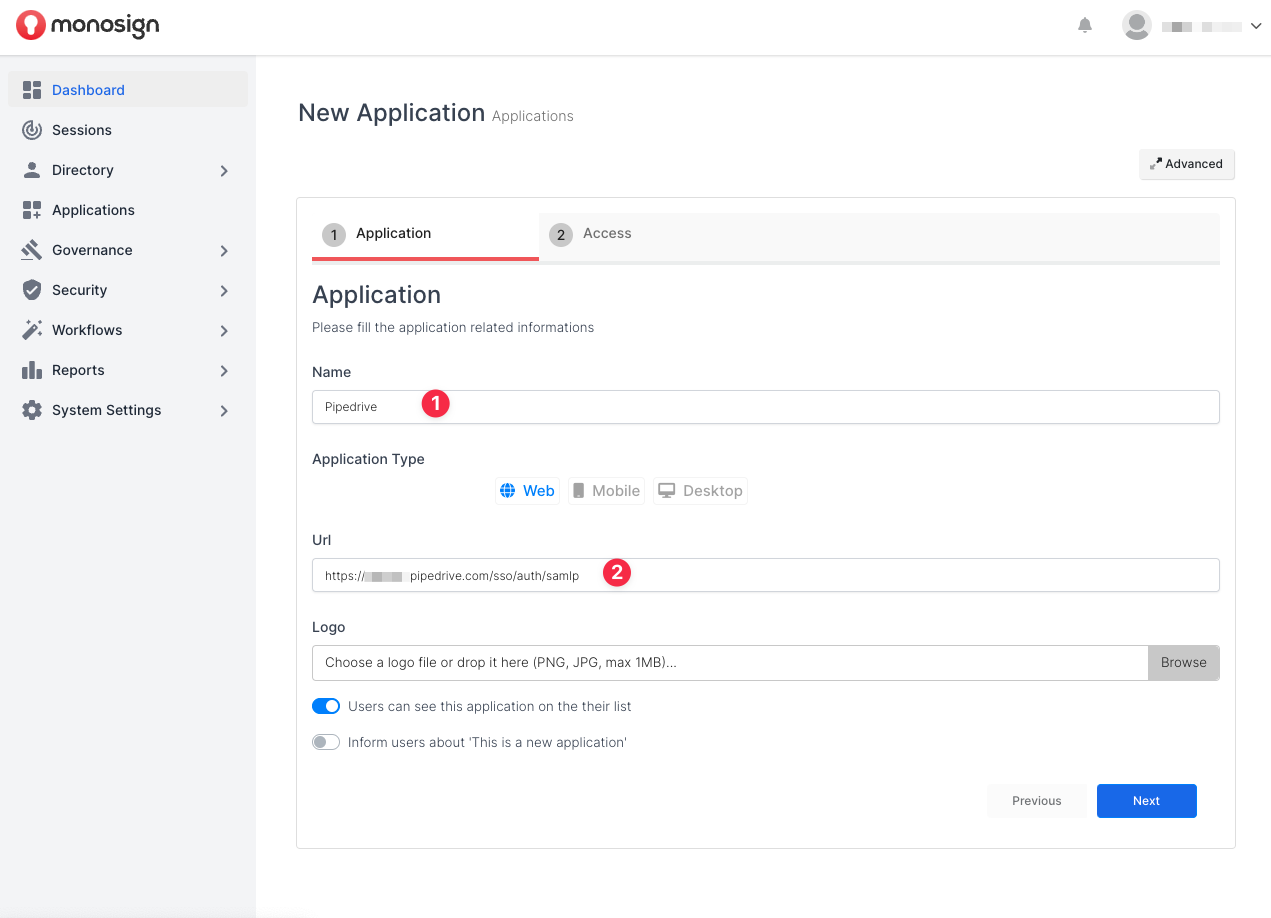
Create your application on MonoSign and make sure you typed Pipedrive SSO Sign-in URL to URL input.
Once you created the application and navigated to the detail page, click Keys and Add New Key to create a SAML access key.
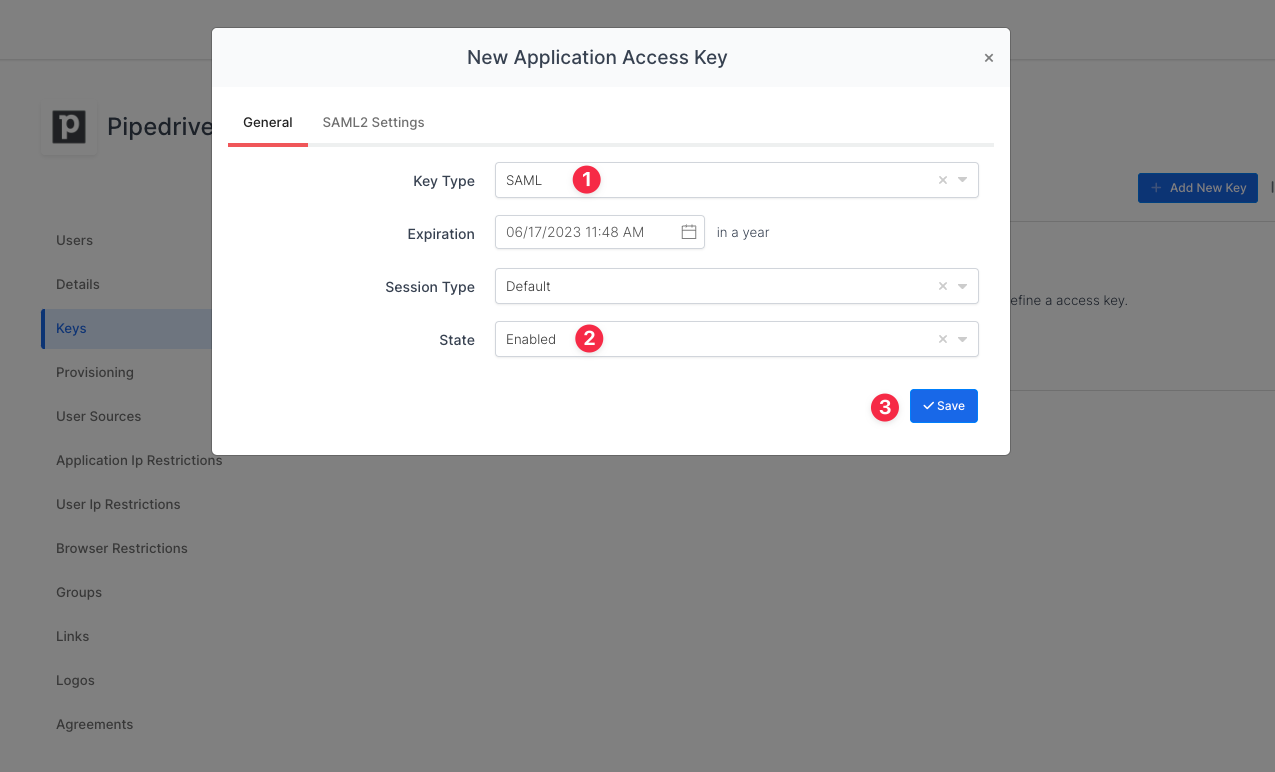
In the opened modal, choose SAML as Key Type and switch to SAML2 Settings.
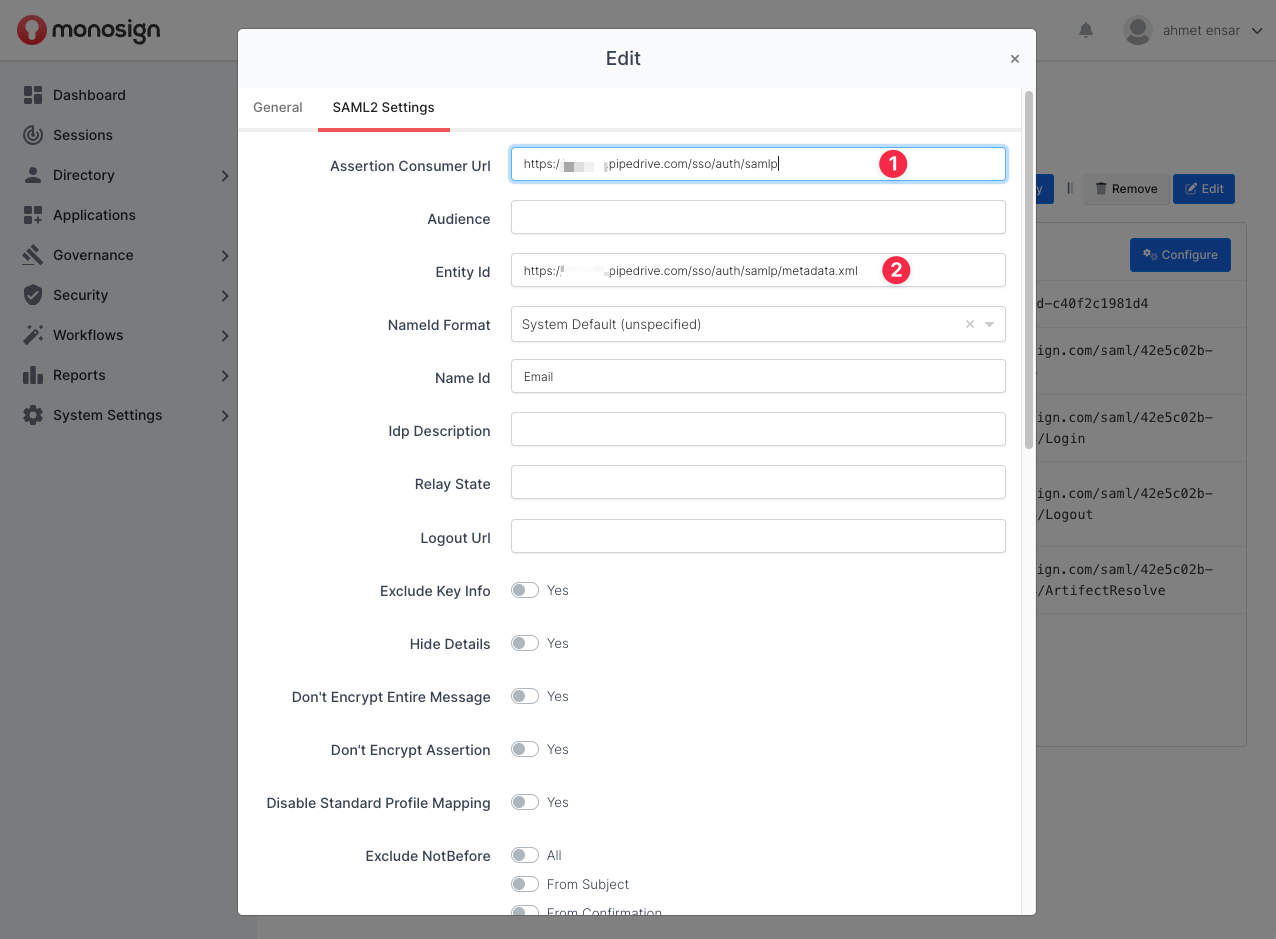
Fill in the necessary fields according to the information provided by AWS. Correspondings of the fields are as below.
Field | Value |
|---|---|
Assertion Consumer Url | Single Sign On (SSO) url from Pipedrive SAML configuration |
Entity Id | Metadata URL from Pipedrive SAML configuration |
Name Id |
Extra Attributes | |
|---|---|
{{Email}} |
Click Save and you are gonna see your configuration for your access key as follows;
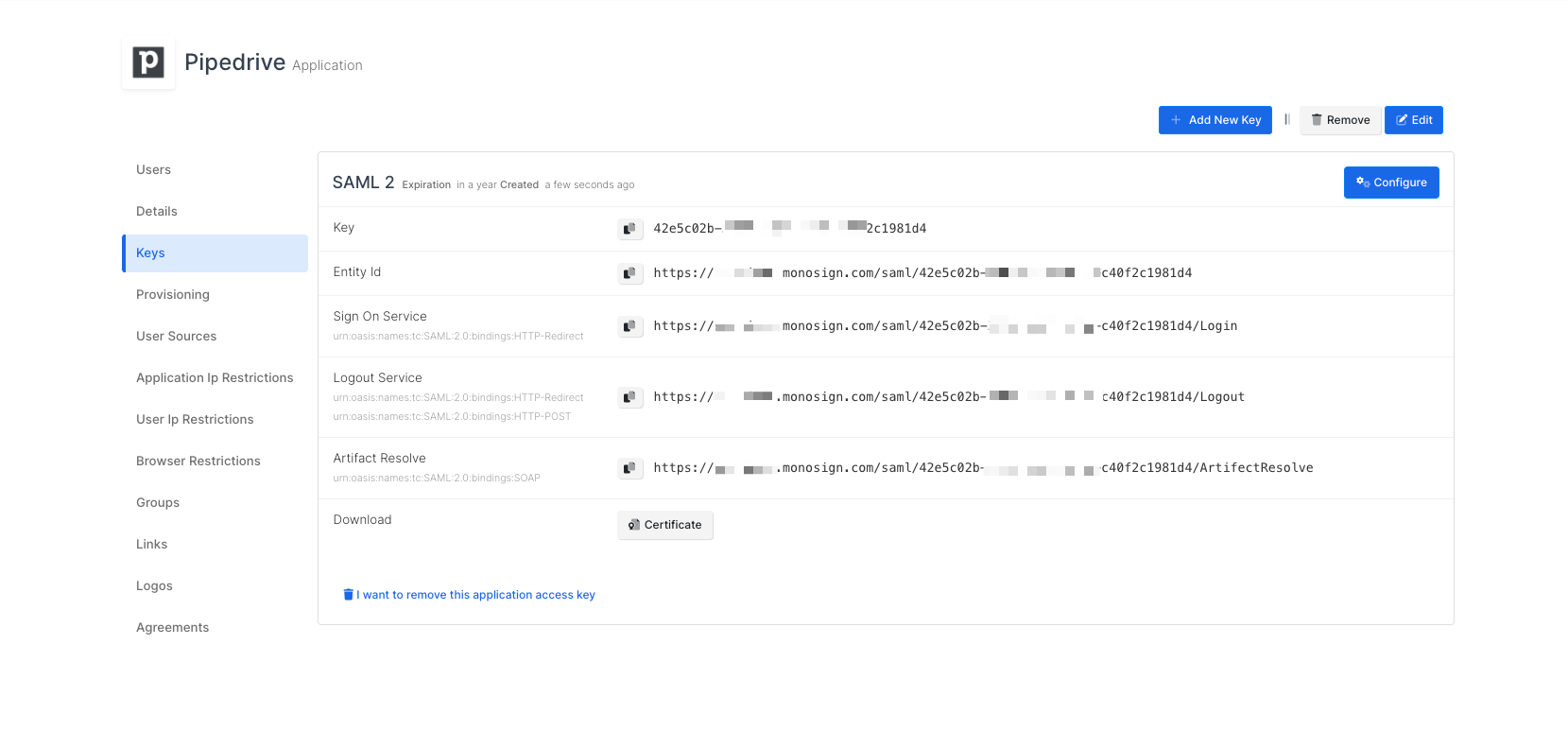
Configuration Single Sign-On for Pipedrive
We are gonna move on to where we left off on the Pipedrive Single Sign-on page which is mentioned in the first chapter.
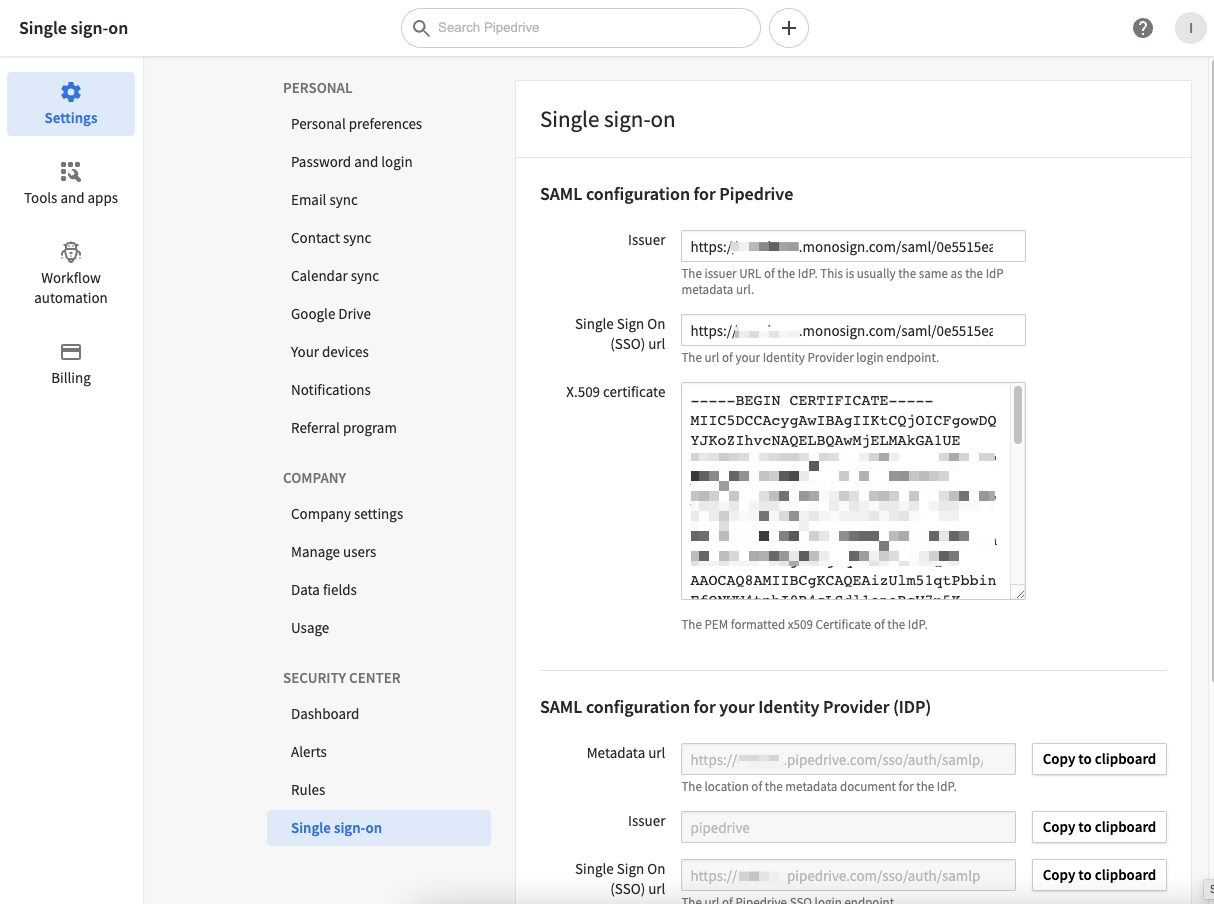
Fill in the necessary fields according to the access key created on MonoSign. Correspondings of the fields are as below.
Field | Value |
|---|---|
Issuer | Entity Id from the application SAML key |
Single Sign On (SSO) url | Sign On Service from the application SAML key |
X.509 certificate | The certificate issued to access key - can be downloadable from the key detail. |
You need to view your certificate in x509 format. in that case, we prefer using OpenSSL - “a robust, commercial-grade, full-featured toolkit for general-purpose cryptography and secure communication.”
Use the command below to view the certificate.
openssl x509 -in {path of your certificate} -text
The output contains various information about the certificate. However, you should check the text starts with “-----BEGIN CERTIFICATE-----”.
Once you have copied and pasted the values, click Save and test. If everything has been configured correctly, you should see a success message.
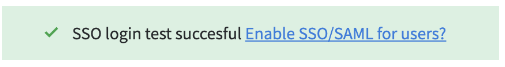
You can then enable SSO for your users by clicking the toggle at the bottom of the page.

If any error occurs while processing, feel free contact support.
