Splunk SAML Integration
This document explains how to implement Monosign with Splunk. It covers Single Sign-On. Before you continue, it is better to start with Splunk’s Single Sign-On guide.
This document will cover Splunk Enterprise and Cloud solution.
📑 Instructions
This documentation contains 4 main steps for integration.
Creating an Application on Monosign
Configuration Single Sign-On for Splunk
Assign a user to the Splunk app
Sign In Test
Optional Settings on Splunk
1- Creating an Application on Monosign
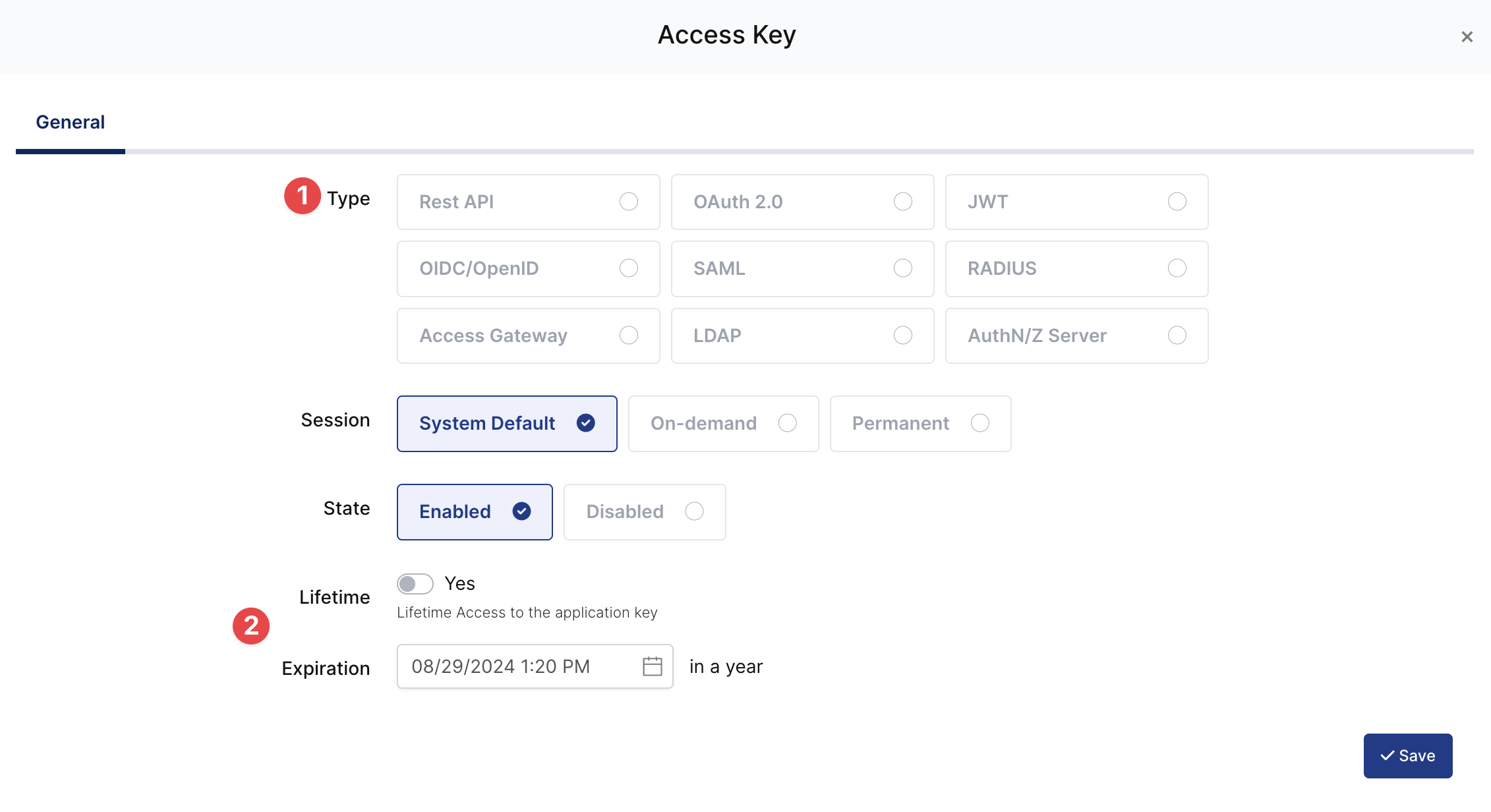
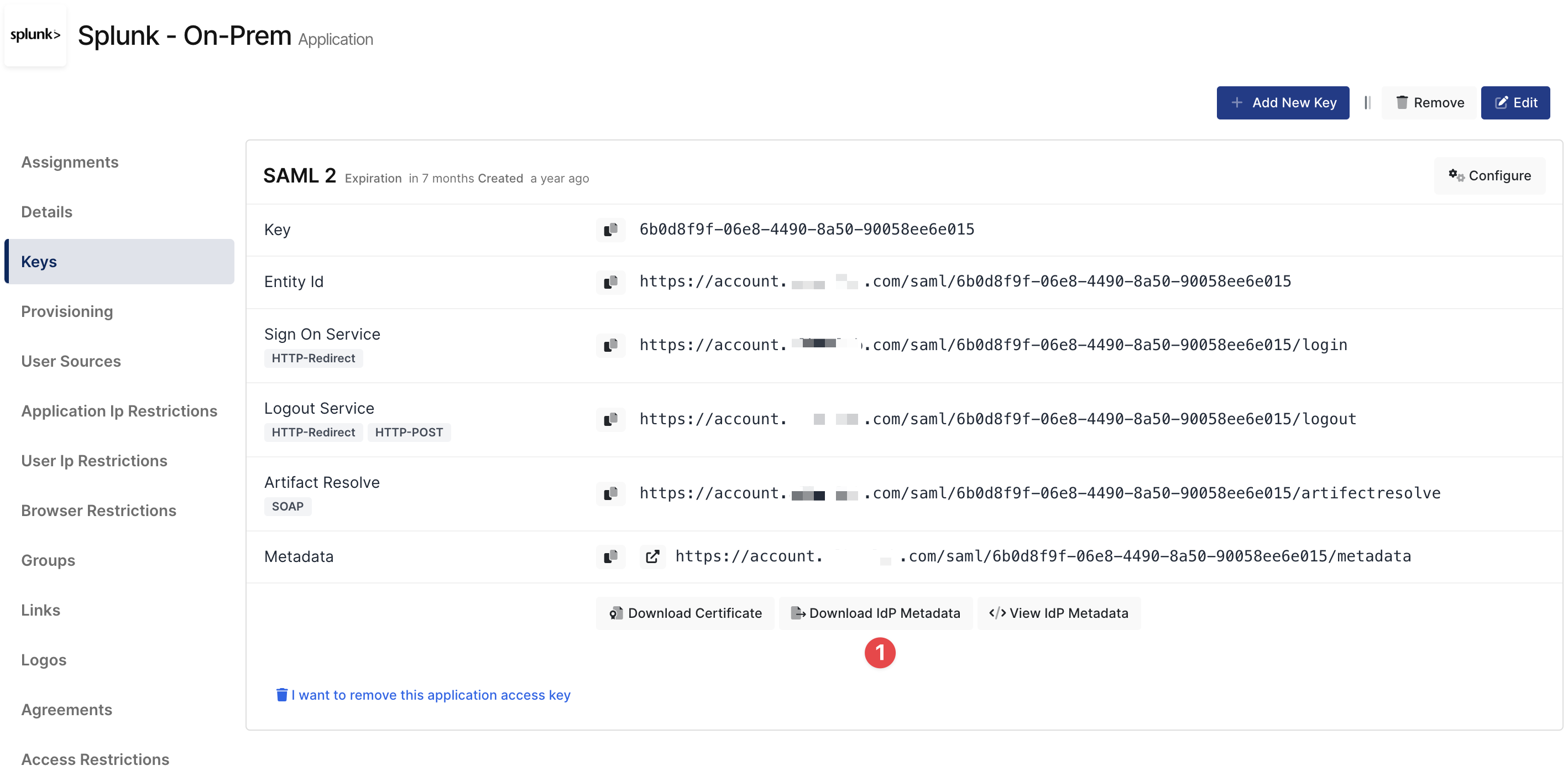
Create your application on Monosign and configure your access policy. Once you create, click “Keys” and add a new Access Key for SAML Key for access.
We will need this information while we configure the Splunk app.
Property | Value | Options |
|---|---|---|
Key Type | SAML | Rest API, OAuth 2.0, JWT, OIDC/OpenID, SAML, RADIUS, Access Gateway, LDAP, AuthN/Z Server |
Expiration | Lifetime | Lifetime or Specific Date/Time - By Default Lifetime is Enabled. |
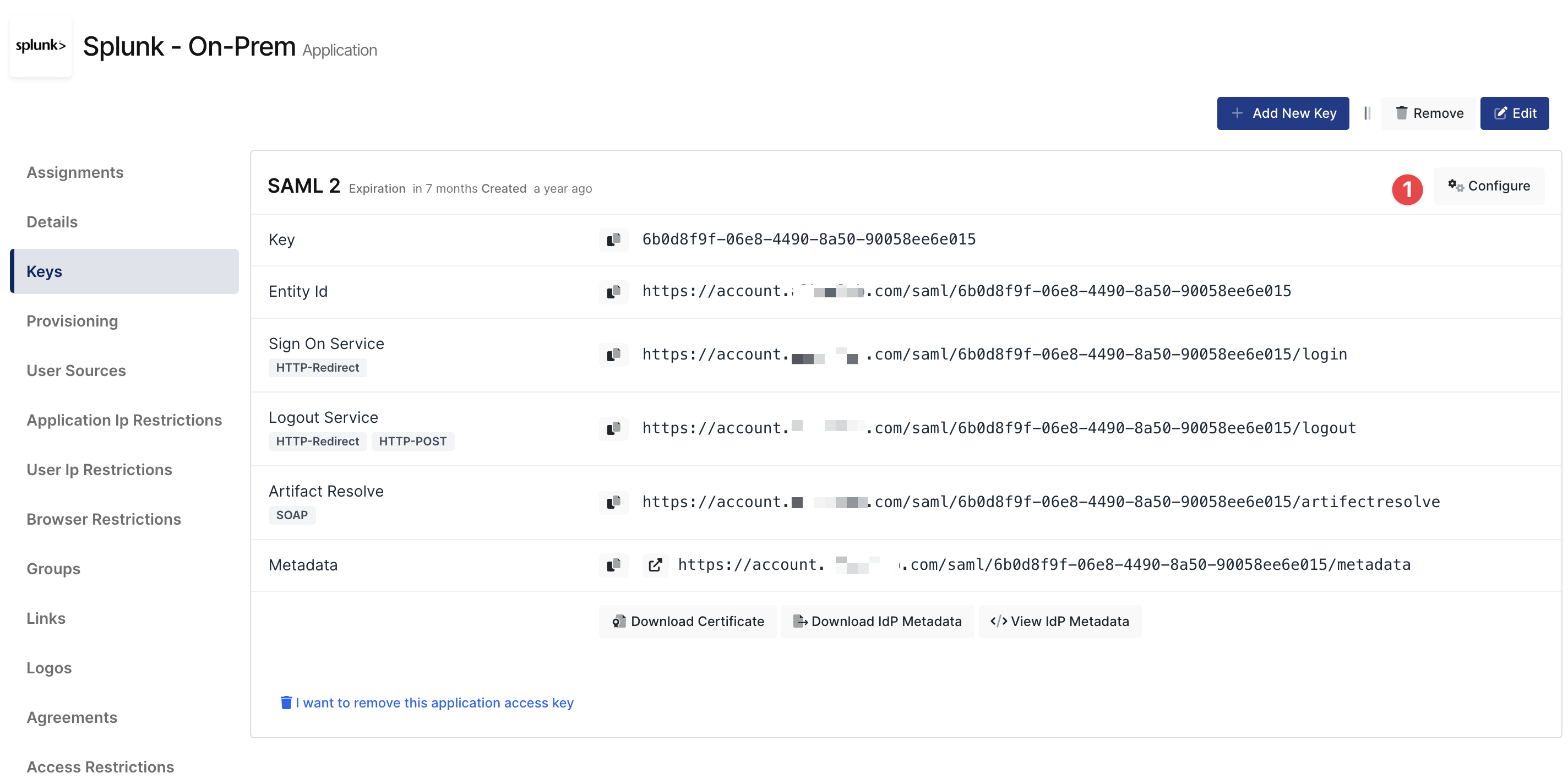
Configuration details for the Splunk application are provided as follows:
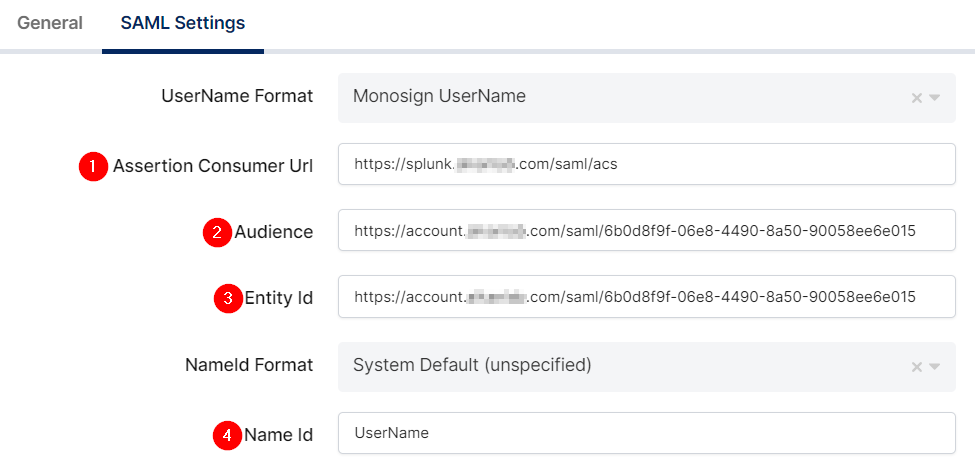
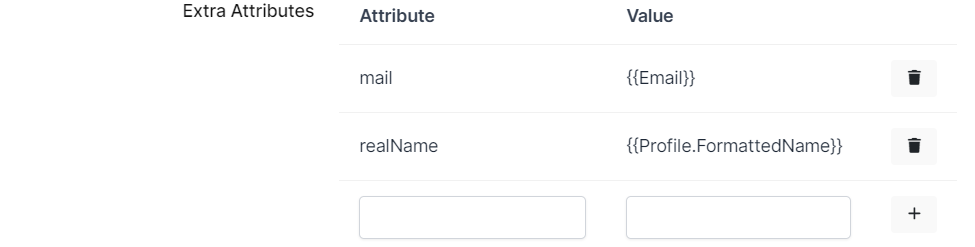
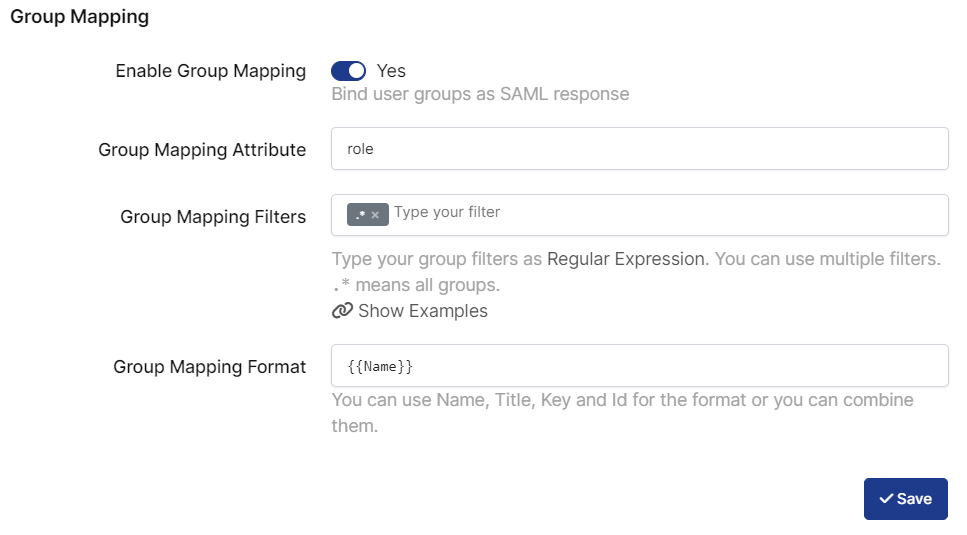
Change ACS(Assertion Consumer Url), Audience, Entity Id, NameId Format, Name Id and Group Mapping.
Property | Value |
|---|---|
Assertion Consumer Url |
|
Audience |
|
Entity Id |
|
NameId Format |
|
Name Id |
|
Extra Attributes |
|
Enable Group Mapping | True |
Group Mapping Attribute | role |
To ensure that the application has access to user groups, follow these steps:
If the application hasn't been configured yet, click the “Edit” option for the application.
In the application settings, navigate to the “Source, Provider, and Profile” tab.
Configure the “User Access Type“ and “User Group Access Type” as “Only Assigned Users.”
Configuring this setting will allow the application to access by user groups when users sign in.

Property | Description | Options |
|---|---|---|
User Access Type | Defines which Users will access to this application. | Only Assigned Users |
User Group Access Type | Defines application’s user group access | Only Assigned Users |
Profile Access Type | Defines Application’s user’s profile access | Restricted - Only restricted user profile attributes |
2- Configuration Single Sign-On for Splunk
As it highlighted at the beginning of document, please check out the Splunk’s SSO configuration page first.
Please add your SAML settings to the application. The following information is needed for your configuration. The following information is needed for your configuration file or environment file. Before configure Splunk go to application key and download IdP Metadata.
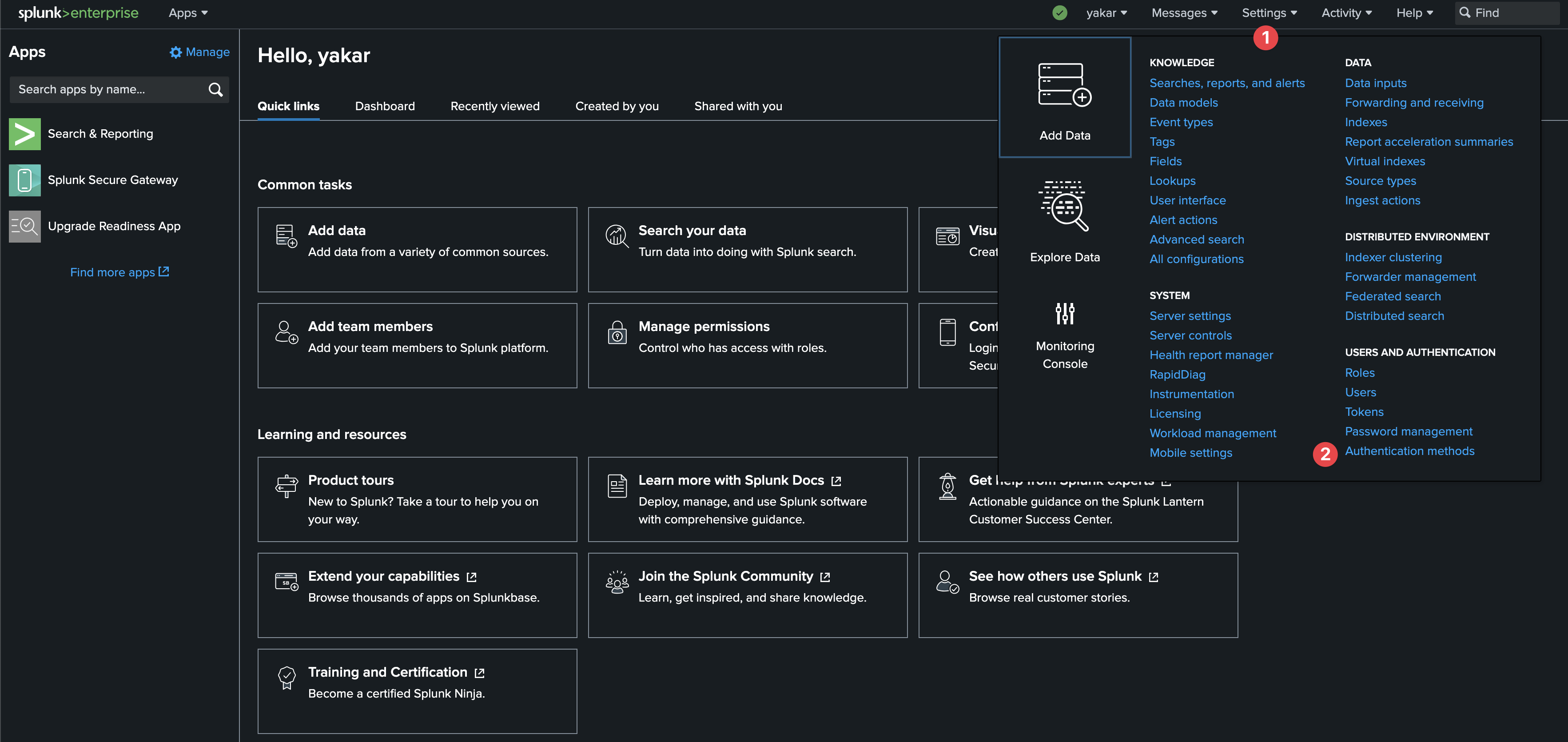
Open Splunk configure Authentication Method page under Settings.
Click SAML and SAML Settings
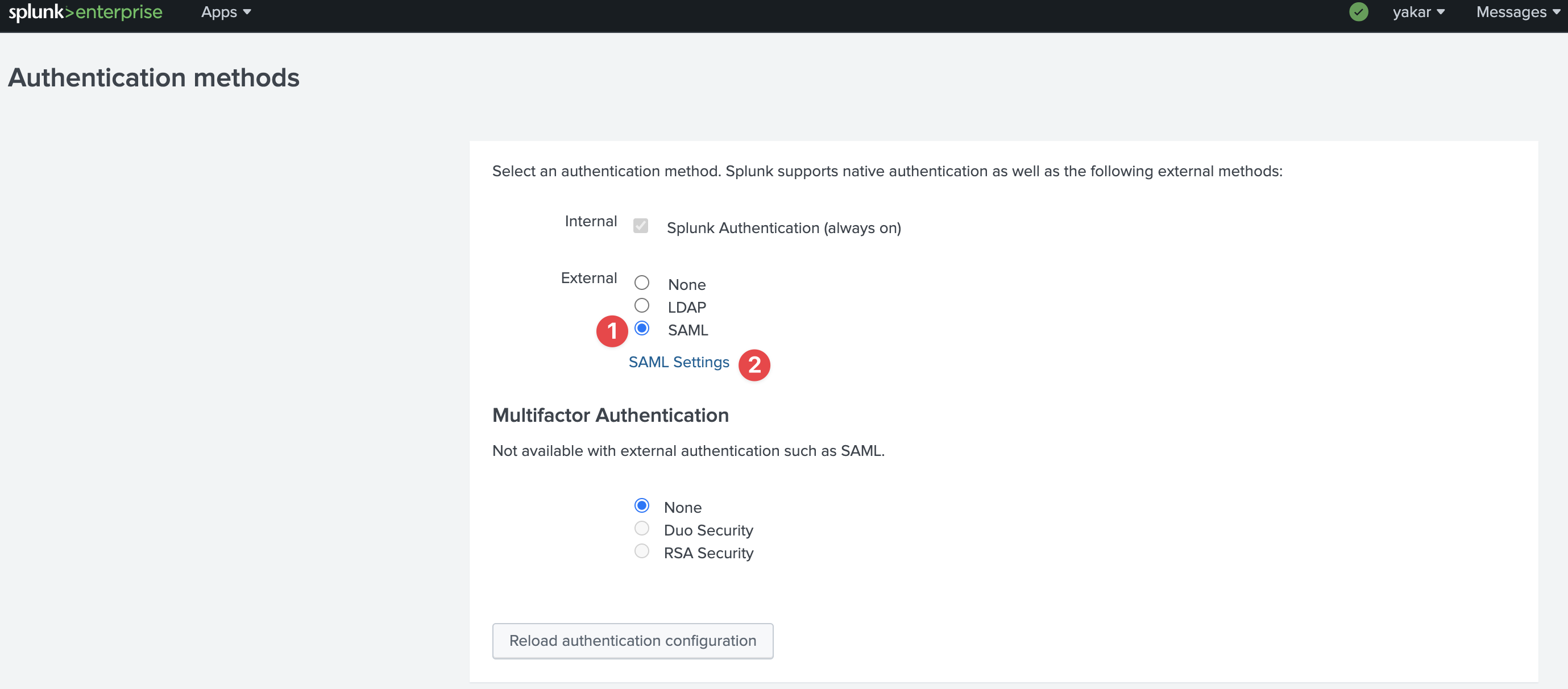
Click SAML Configuration
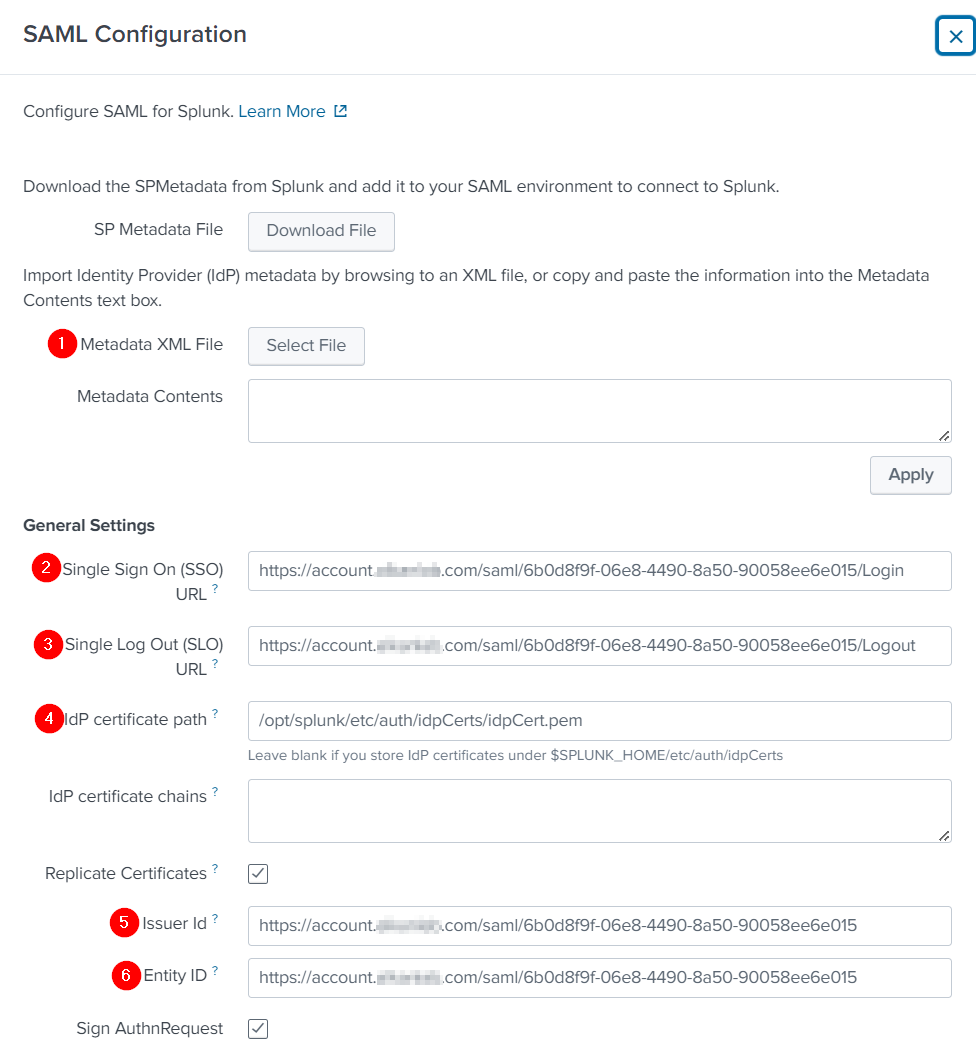
Click Select File and upload downloaded IdP Metadata file from Monosign.
Please verify below settings configured properly:
Property | Value |
|---|---|
Single Sign On (SSO) URL |
|
Single Log Out (SLO) URL |
|
IdP certificate path |
|
Issuer Id |
|
Entity Id |
|
Sign AuthnRequest |
|
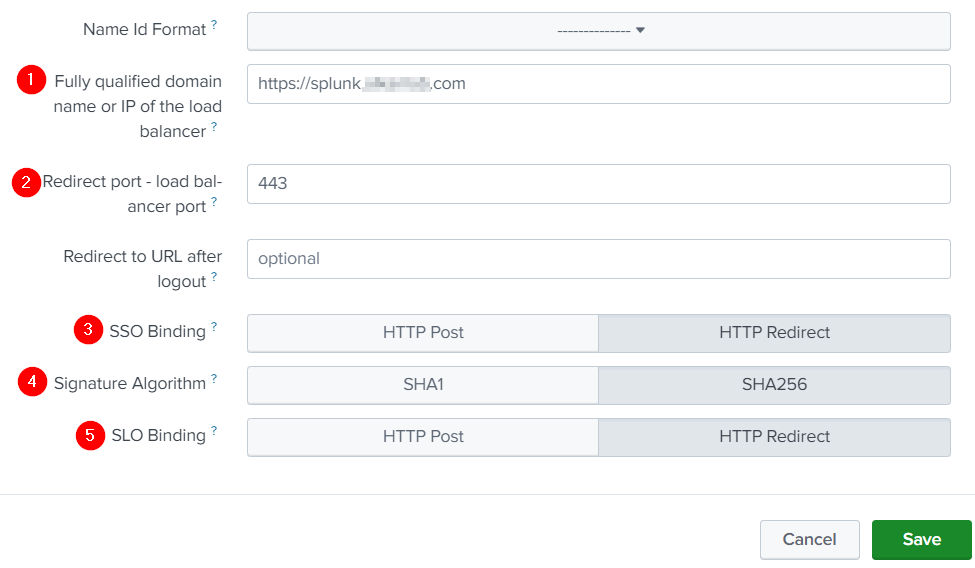
Fully qualified domain name or IP of the load balancer |
|
Redirect port-load balancer port |
|
SSO Binding |
|
Signature Algorithm |
|
SLO Binding |
|
Now, go back to Monosign and give access to your users and try login.
3- Assign a user to the Splunk app
Please follow below instructions on how to assign a user to the Splunkapplication. In this example john.smith will assign to the application access.
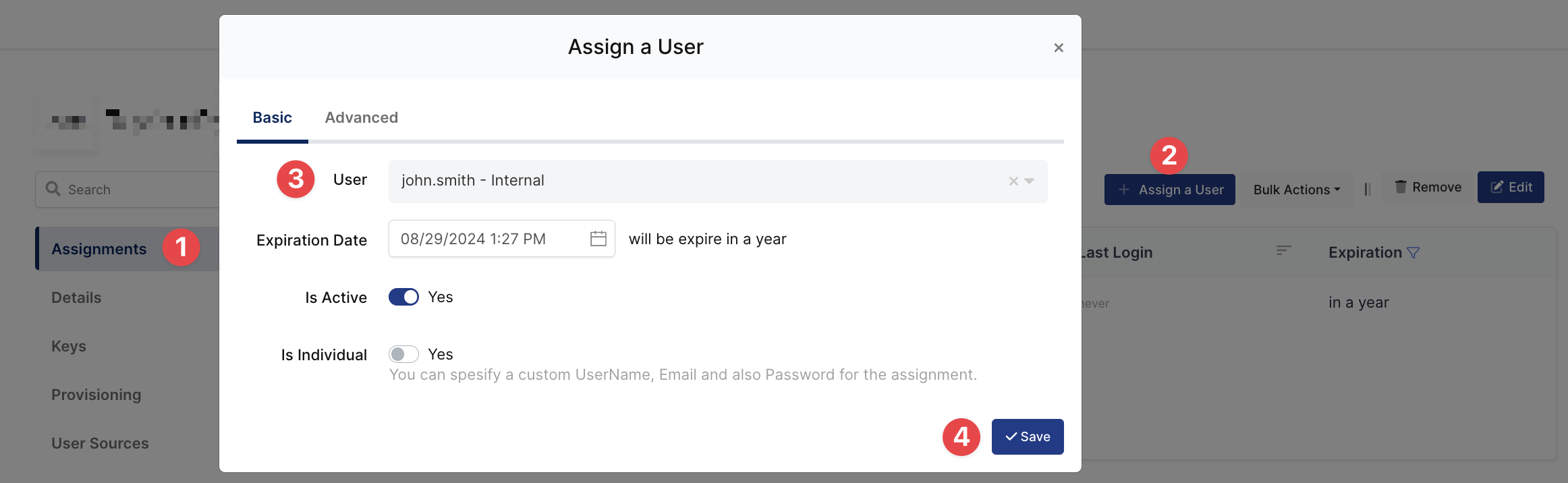
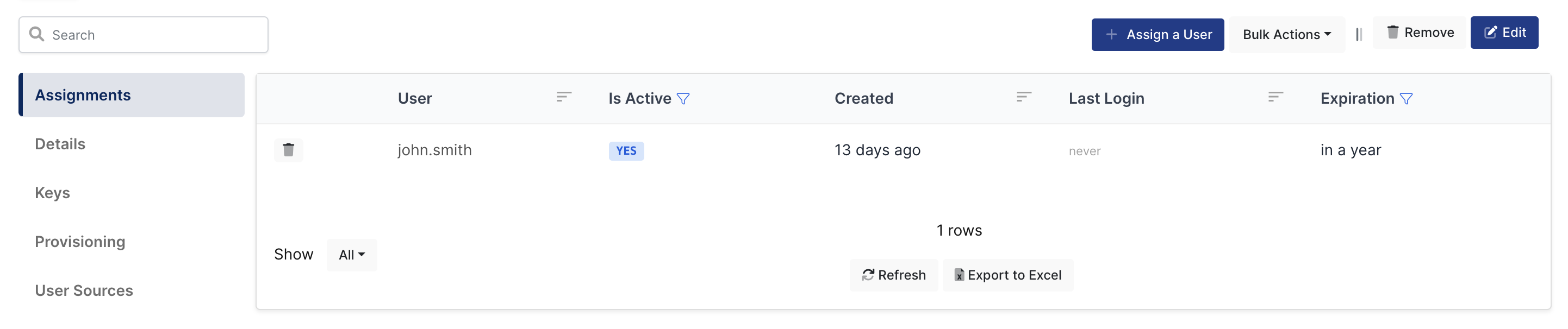
Splunk go to Settings → Authentication Method → SAML Settings → New Group
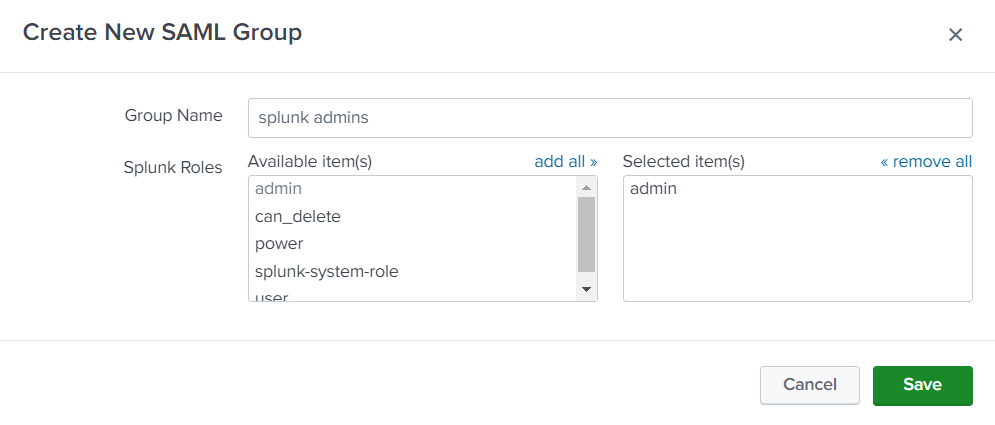
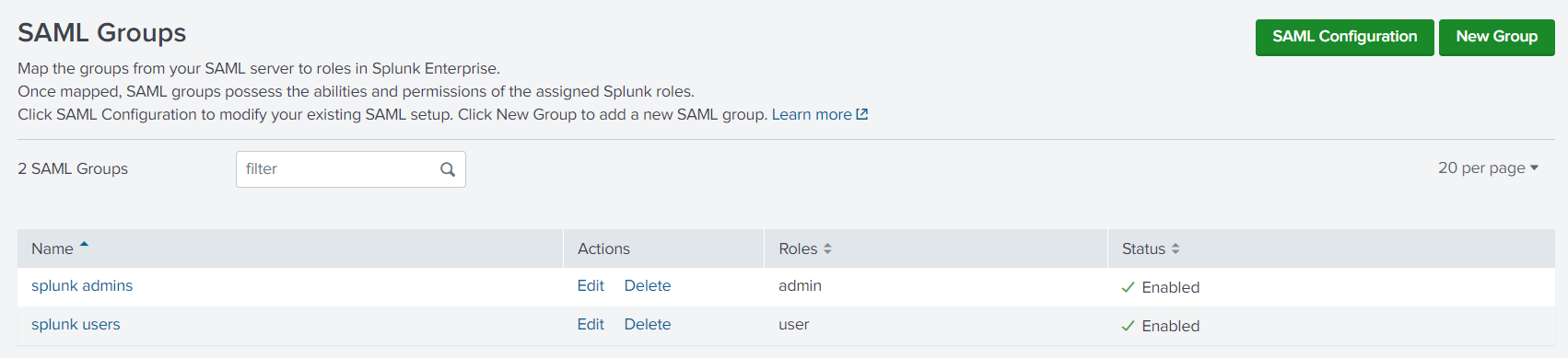
Type same group name on the Active Directory group which assigned user is member of than give permissions.
4- Sign In Test
Now try login. Navigate to the Splunk app. Click Monosign on the UI.
If everything is well configured, you will be redirected to Monosign’s login page. You can log in passwordless with your QR code or you can type your user name and password.
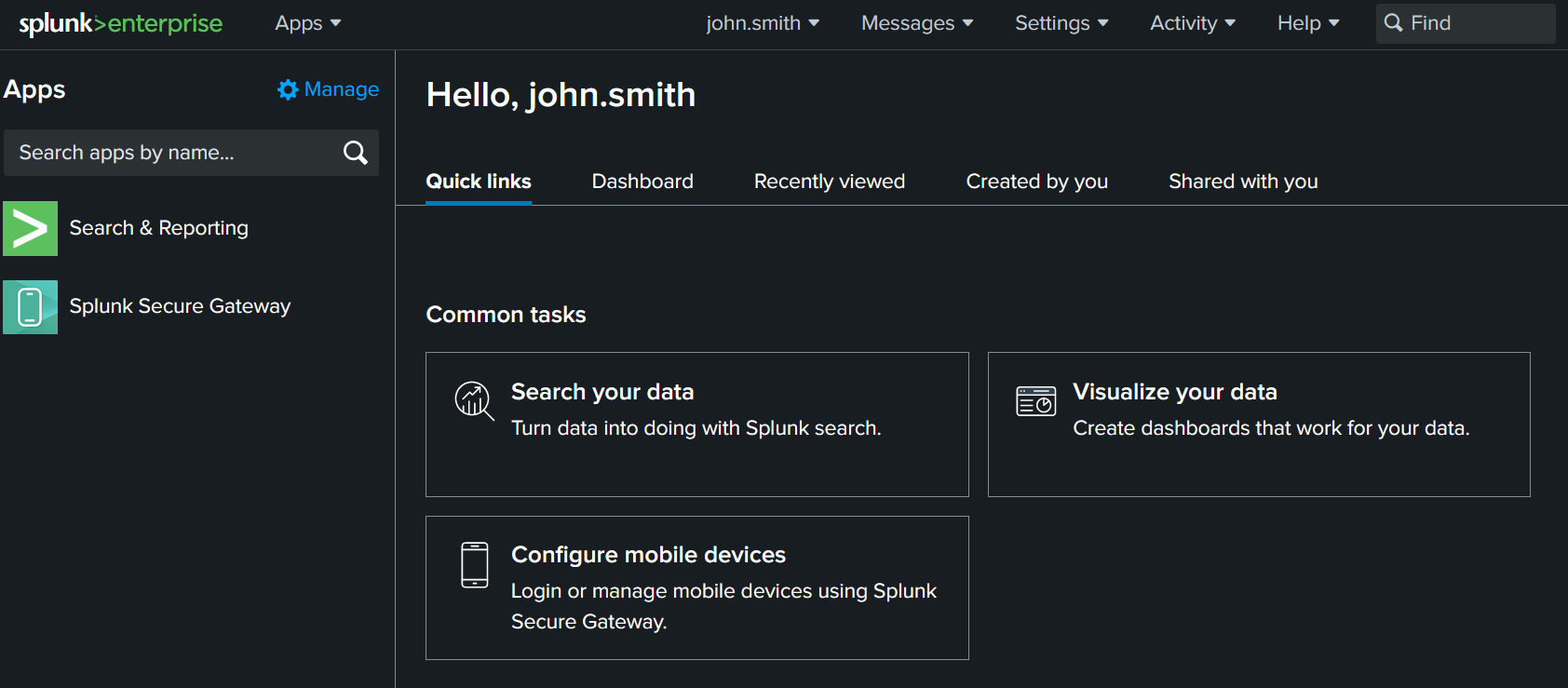
When you logged, you are gonna be redirected to the Splunk as which role assigned previous steps.
If something goes wrong while trying to login to Splunk Web console with SAML, below link can be used for the local authentication
For Enterprise
https://<SPLUNK_WEB_URL>/en-US/account/login?loginType=splunk
For Cloud
https://{name}.splunkcloud.com/en-US/account/login?loginType=splunk
Replace {name} with your account name
5- Optional Settings on Splunk
If the following error is encountered during the login process after Splunk SAML integration:
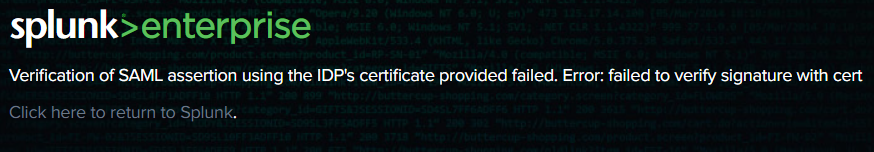
Login to Splunk server via ssh go to /opt/splunk/etc/system/local folder and edit authentcation.conf file. Change signedAssertion settings from true to false.
[authentication]
...
[roleMap_SAML]
...
[userToRoleMap_SAML]
...
[saml]
...
signedAssertion = false
...Than restart Splunk service
/opt/splunk/bin/splunk restart