Windows Credential Provider
This document explains how to implement Monosign with Microsoft Windows MFA.
Monofor has no responsibility to do Microsoft Windows OS configurations. If you need support please contact Microsoft Support Services.
📑 Instructions
This documentation contains 6 main steps for integration.
Creating an Application on Monosign
Configuration for Microsoft Windows
Assign a user to the Microsoft Windows application
Sign In Test
Troubleshooting
Uninstall
1- Creating an Application on Monosign
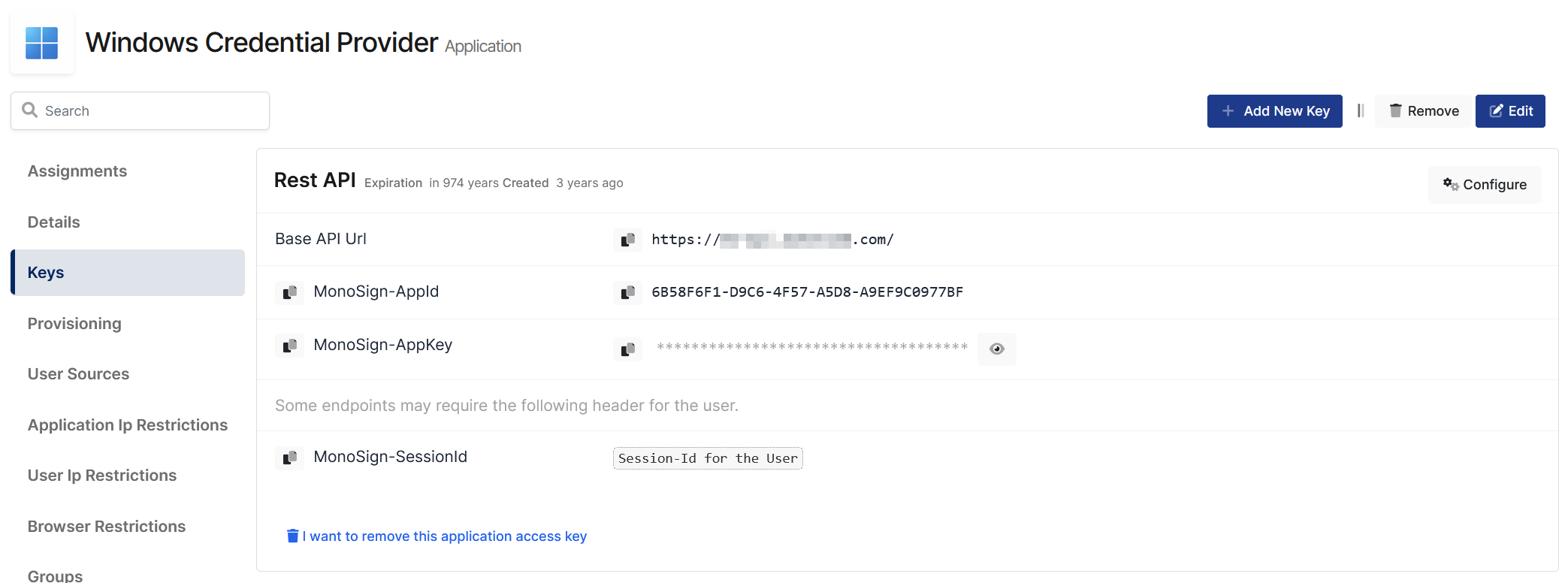
Create application on Monosign and configure your access policy. Once you create, click “Keys” and add a new Access Key for Rest API Key for access.
This information will be necessary during the configuration of the Microsoft Windows application.
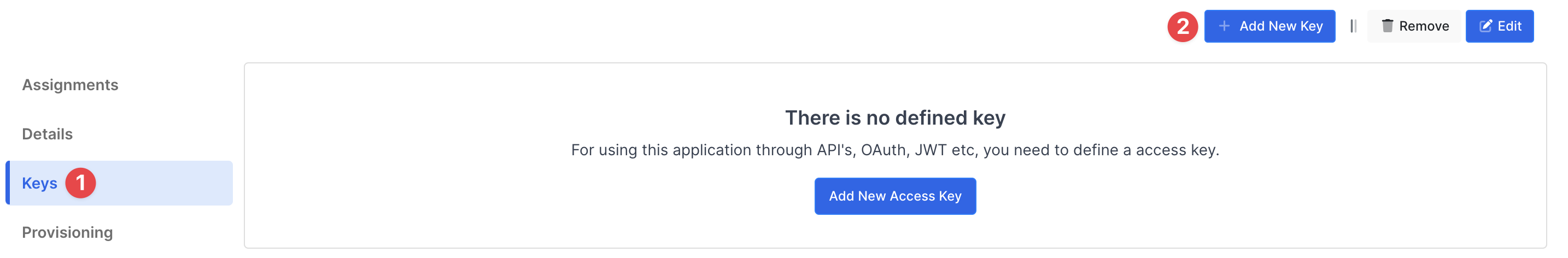
Property | Value | Options |
|---|---|---|
Key Type | Rest API | Rest API, OAuth 2.0, JWT, OIDC/OpenID, SAML, RADIUS, Access Gateway, LDAP, AuthN/Z Server |
Expiration | Lifetime | Lifetime or Specific Date/Time - By Default Lifetime is Enabled. |
Configuration details for the Microsoft Windows application are provided as follows:
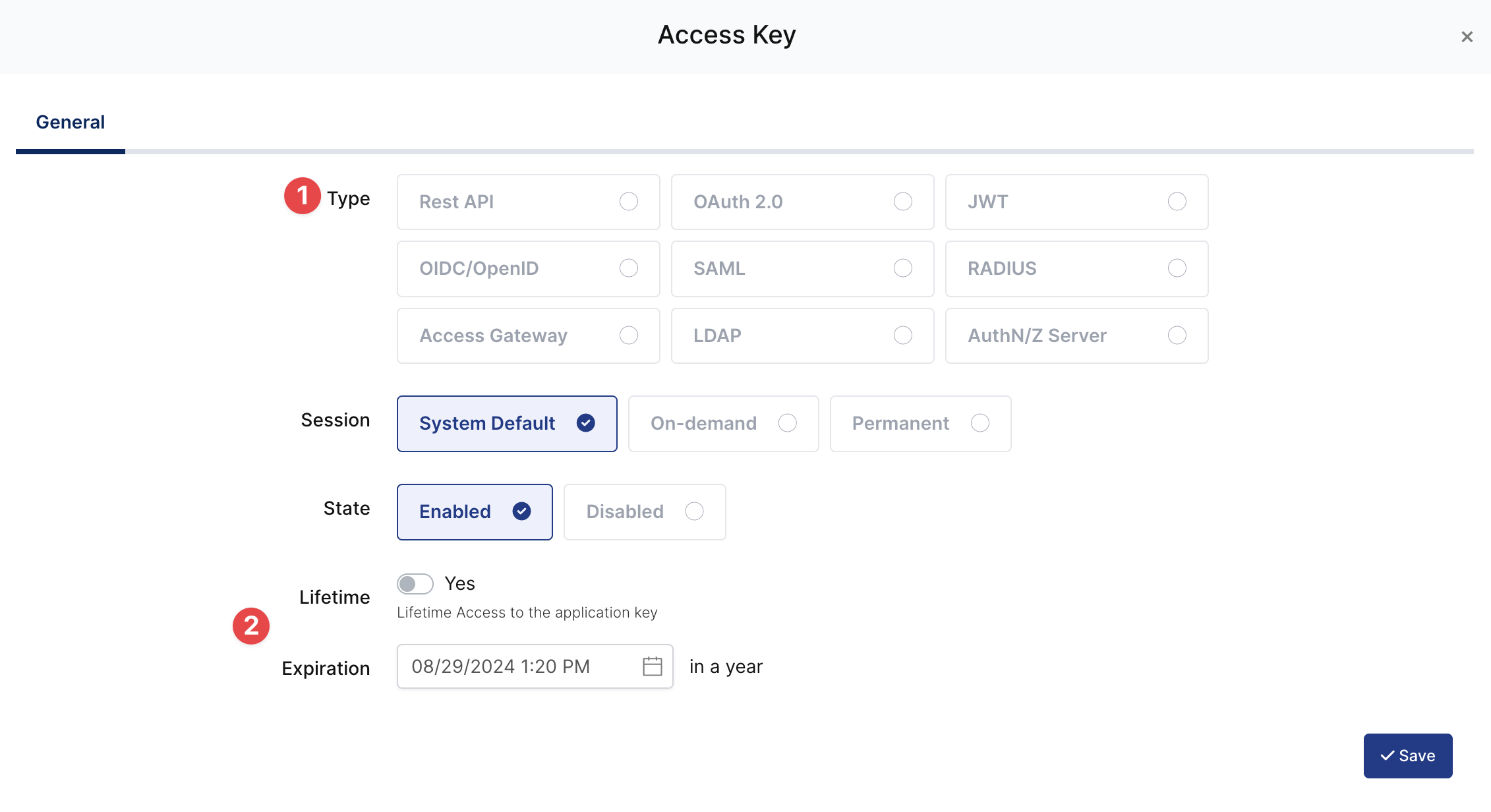
To ensure that the application has access to user groups, follow these steps:
If the application hasn't been configured yet, click the “Edit” option for the application.
In the application settings, navigate to the “Source, Provider, and Profile” tab.
Configure the “User Access Type“ and “User Group Access Type” as “Only Assigned Users.”
Configuring this setting will allow the application to access by user groups when users sign in.

Property | Description | Options |
|---|---|---|
User Access Type | Defines which Users will access to this application. | Only Assigned Users |
User Group Access Type | Defines application’s user group access | Only Assigned Users |
Profile Access Type | Defines Application’s user’s profile access | Restricted - Only restricted user profile attributes |
2- Configuration for Microsoft Windows
Microsoft Windows MFA is working with Credential Provider. To enable this feature you need to change some registry configurations on your windows machine.
You can download latest version here Monosign Credential Provider
Unzip downloaded file. This zip file contains below files.
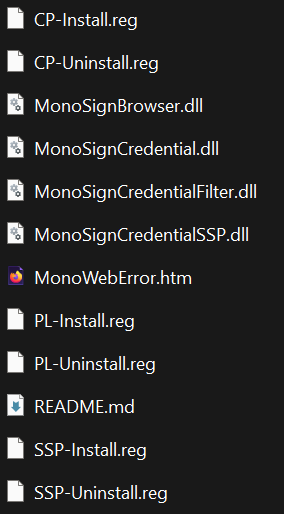
Credential Provider File
Microsoft Windows MFA will work after CP-Install.reg file applied to windows machine. Before applying to registry file it needs to be updated with application key details which has already created on in 1st Step.
You need to change below values in the CP-Install.reg files than save.
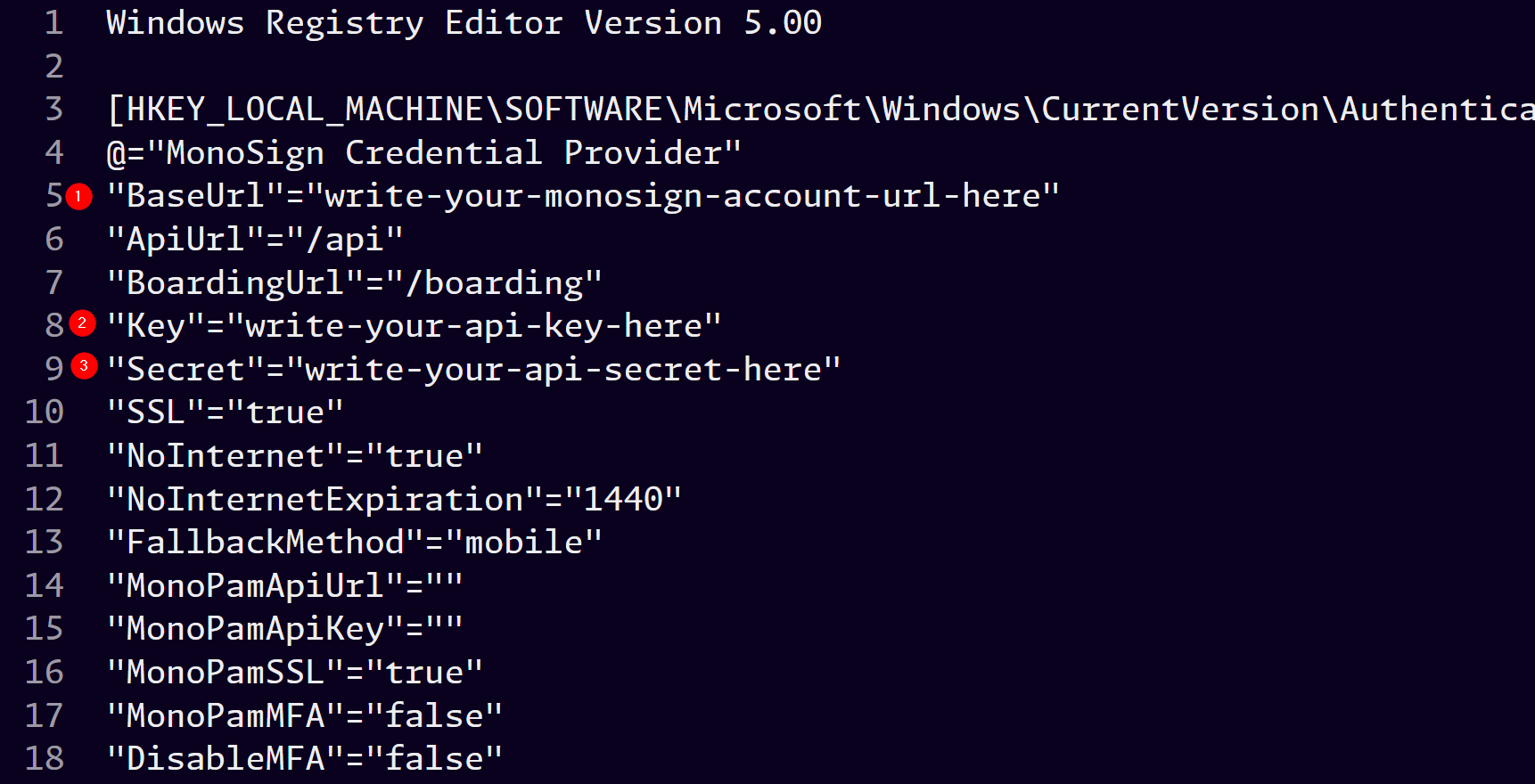
Explanation of the values.
Key | Type | Value | Description |
|---|---|---|---|
BaseUrl |
| Account Address Url |
|
Key |
|
|
|
Secret |
|
|
|
DisableMFA |
|
| This option should only be set |
NoInternet |
|
| If internet is not connected, disable MFA |
NoInternetExpiration |
|
| User can use without MFA if internet is not connected in … minutes |
Please add your Rest API settings to the application. The following information is needed for your configuration.
Change below values in CP-Install.reg file.
Property | Value |
|---|---|
BaseURL |
|
Key |
|
Secret |
|
After editing the file it should look like in the below
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{8D59B60C-7177-4A69-BDB2-D451B08D7751}]
@="MonoSign Credential Provider"
"BaseUrl"="account.monofor.com"
"ApiUrl"="/api"
"BoardingUrl"="/boarding"
"Key"="1e11a3b1-3d41-4634-804d-bee91538a912"
"Secret"="baefdcc1-13b2-430e-a8c3-6ac60bc4ef61"
"SSL"="true"
"NoInternet"="true"
"NoInternetExpiration"="1440"
"FallbackMethod"="mobile"
"MonoPamApiUrl"=""
"MonoPamApiKey"=""
"MonoPamSSL"="true"
"MonoPamMFA"="false"
"DisableMFA"="false"BaseURL format must be FQDN. Please don’t add prepend https:// or http:// to BaseURL.
Copy this files to under C:\Windows\System32
MonoSignBrowser.dll
MonoSignCredential.dll
MonoSignCredentialFilter.dll
MonoSignCredentialSSP.dllPlease apply this registry file to enable Microsoft Windows MFA.
Additional Options
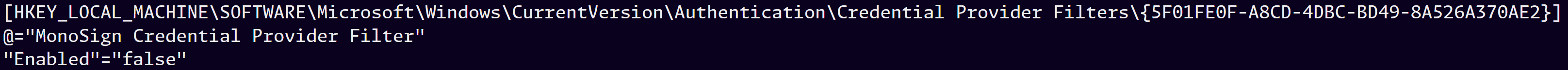
If “Enabled” value is set to “true” under this registry, all credential options will be filtered and only MonoSign and Windows Live options will be available for users, otherwise all sign-in options will be listed without any filtering. The default value for this option is “false“.
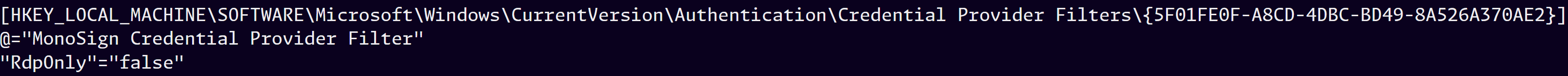
If “RdpOnly” value is set to “true”, MonoSign Credential Provider will be enabled if only the session is an RDP login, otherwise it will be enabled both local (interactive) logins and RDP logins. The default value for this option is “false”.
Now, go back to Monosign and give access to your users and try login.
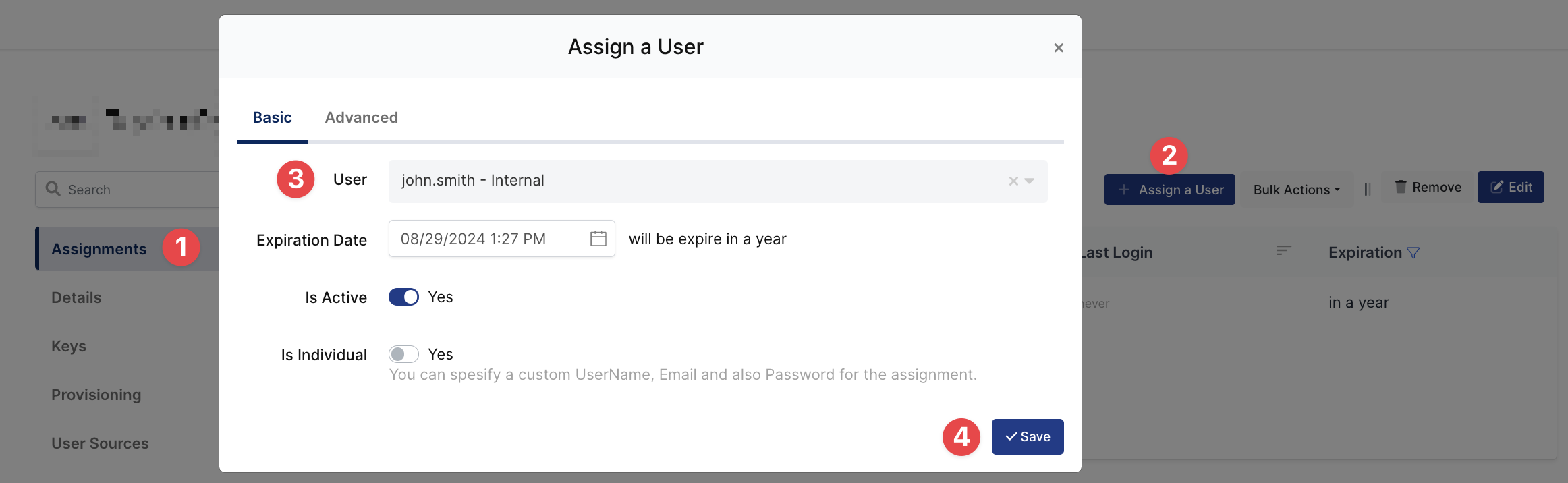
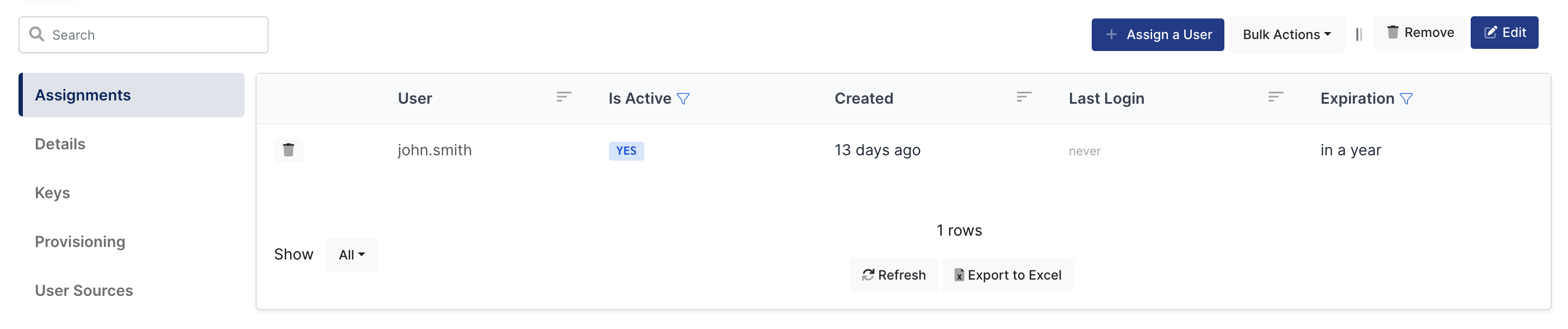
3- Assign a user to the Microsoft Windows application
Please follow below instructions on how to assign a user to the Microsoft Windows application. In this example john.smith will assign to the application access.
4- Sign In Test
Now try login Windows machine via console or RDP. Click Monosign on the UI.
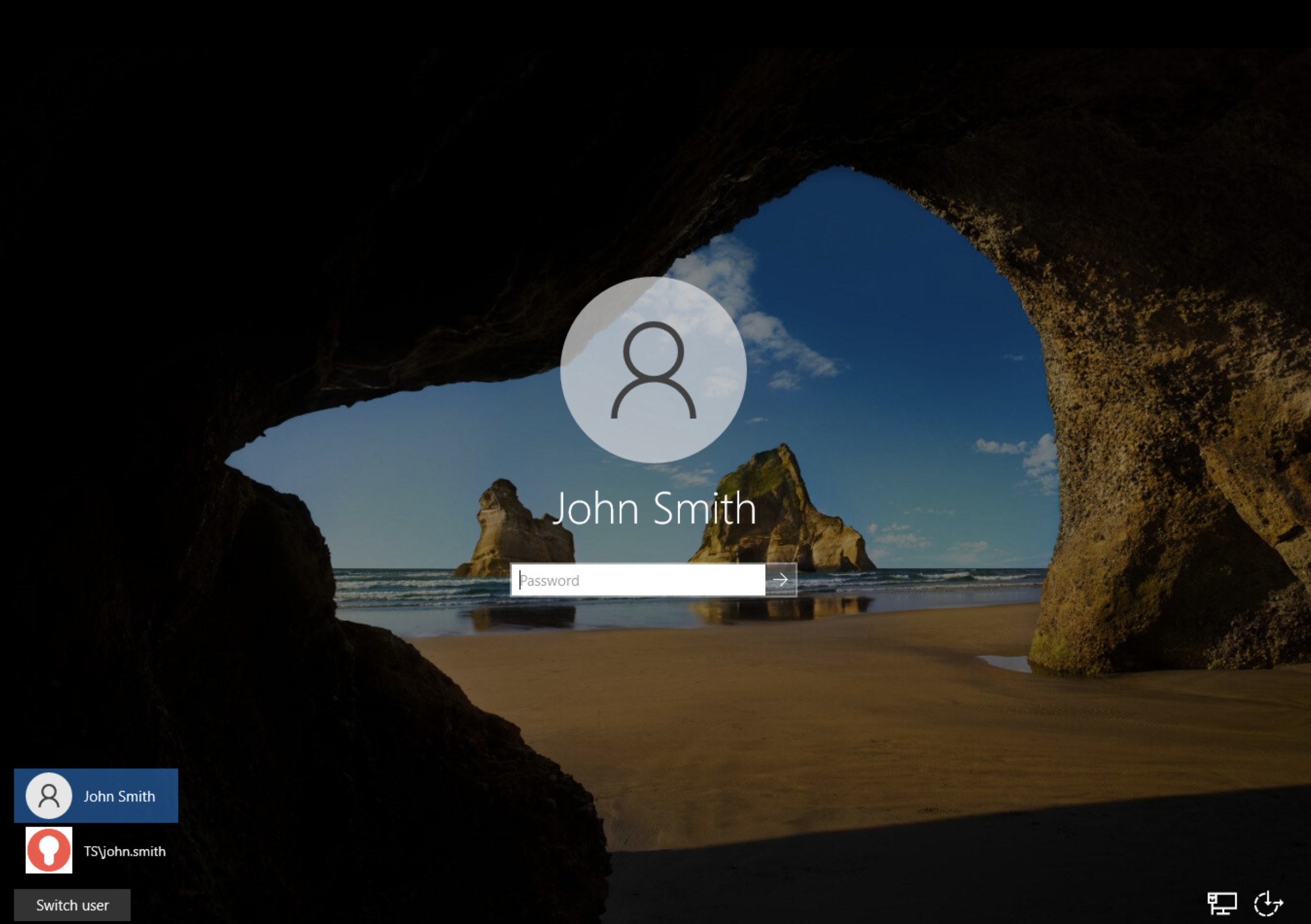
As shown in the above image there are two user will login. One of is normal windows login and another one which profile picture is Monosign is used for Monosign MFA login. Click this user or Switch User button to login windows machine.
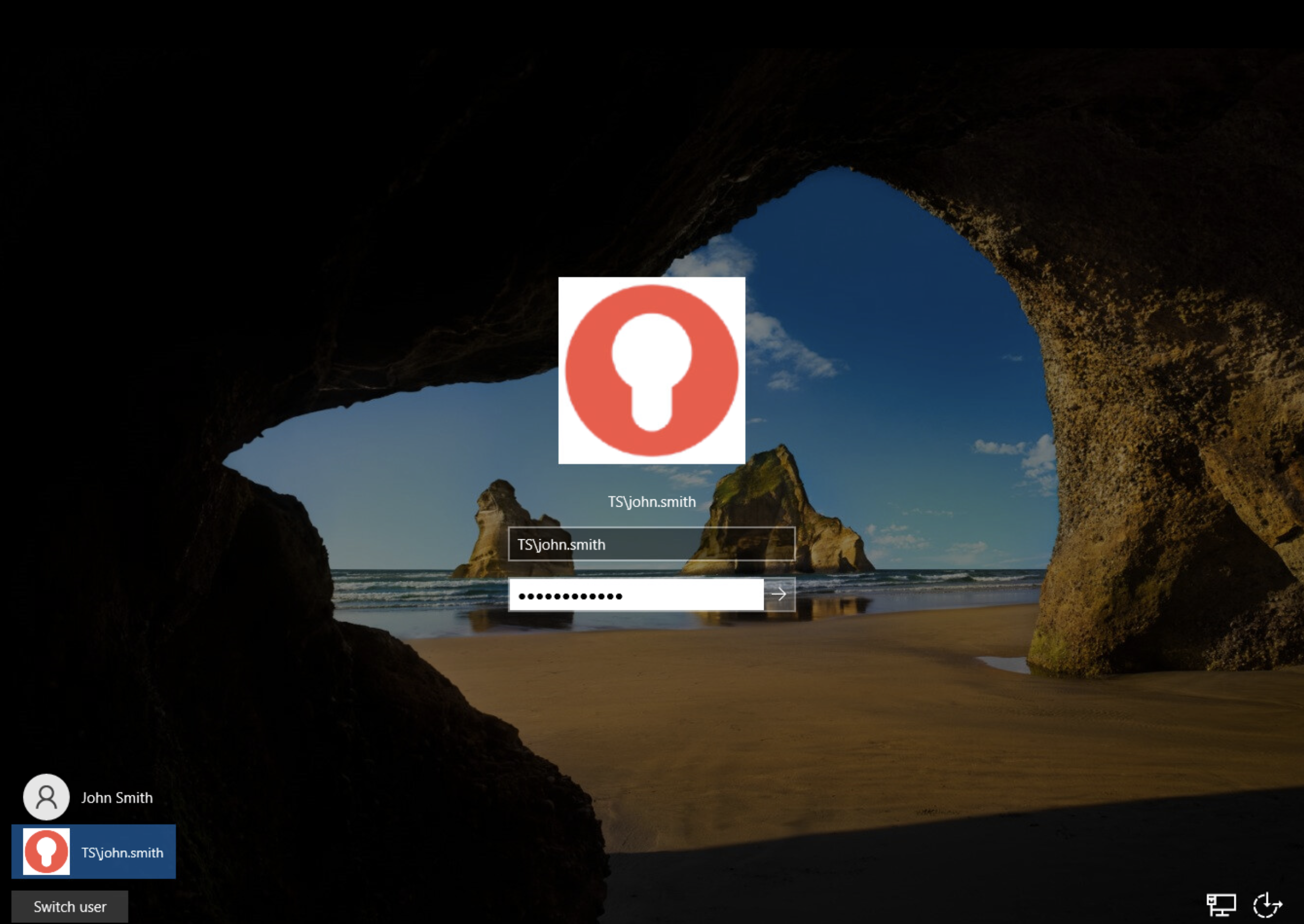
Type Username and password then MFA window will pop-up.
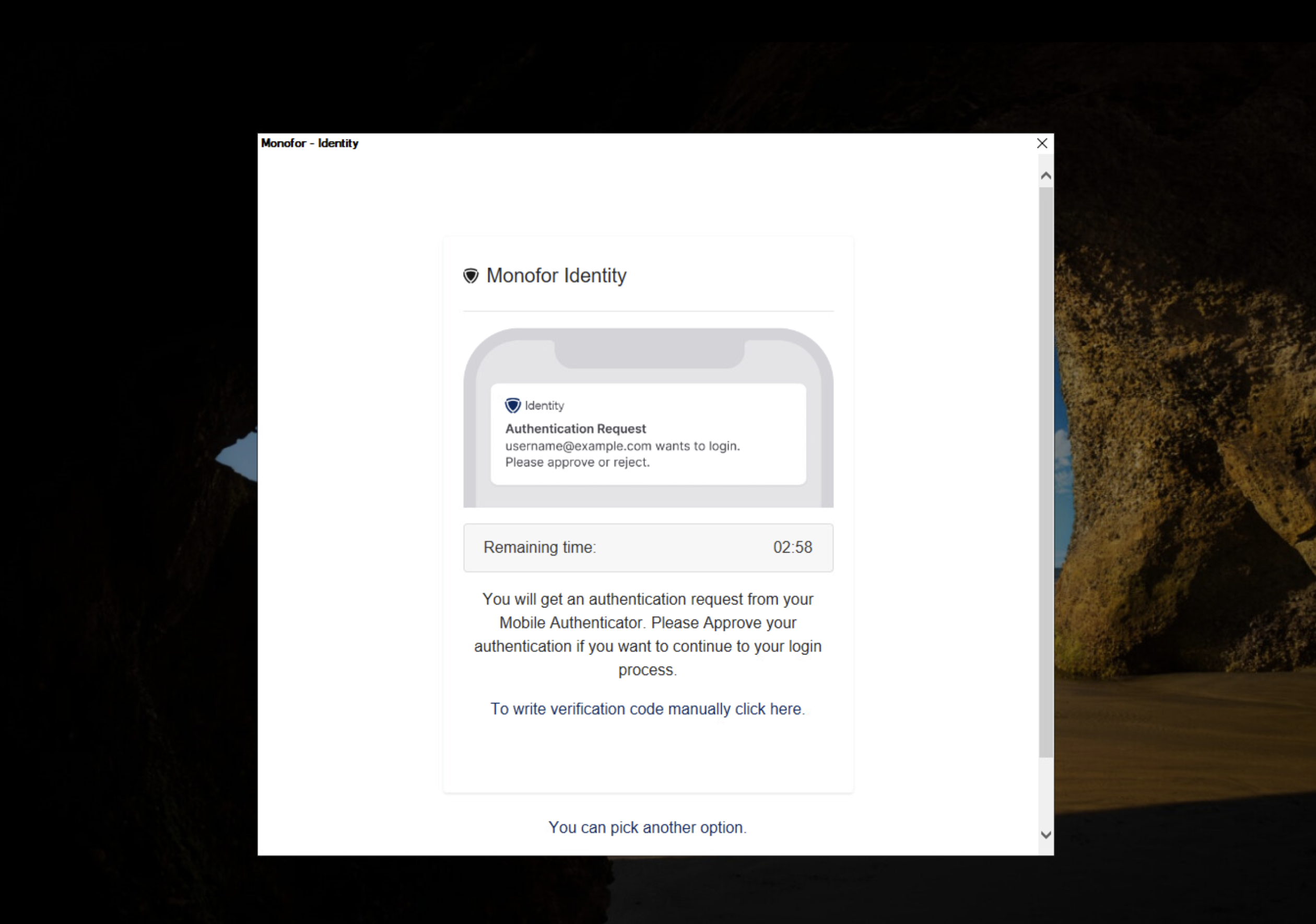
Now approve notification from Monofor Identity on your mobile phone.
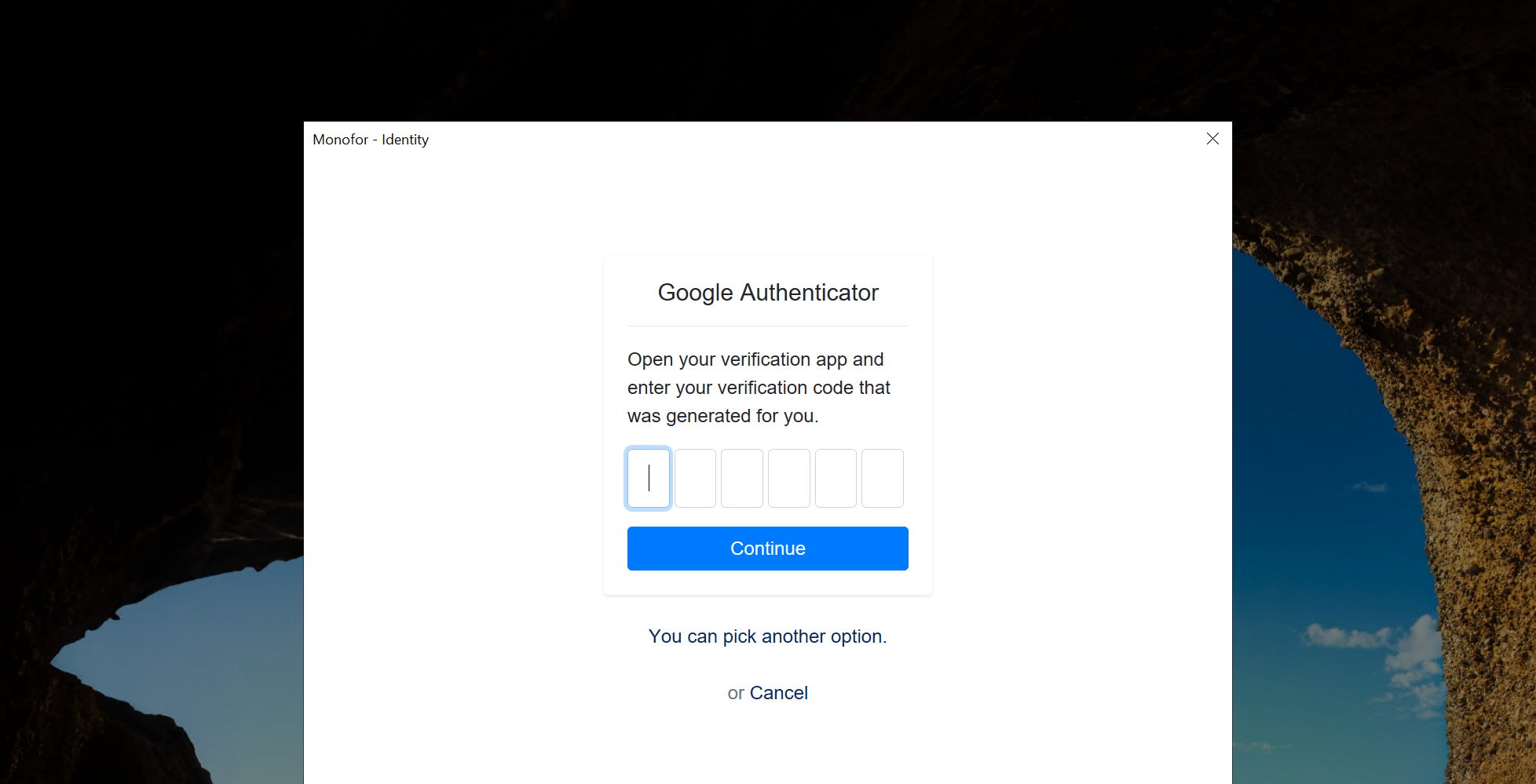
If user enabled another MFA provider this pop-up shows specific MFA operations
For Example: User enabled Google Authenticator then user must provide 6 digit code from Google Authenticator.
5- Troubleshooting
Monosign Credential Provider changed registry settings. There two location under the Registry when applied CP-Install.reg file. check Registry Editor below two locations. Check this two locations and verify all changes applied correctly.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{8D59B60C-7177-4A69-BDB2-D451B08D7751}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Provider Filters\{5F01FE0F-A8CD-4DBC-BD49-8A526A370AE2}Monosign Credential Provider logs all login request. If somethings happen while login to Windows Machine all logs can be find under the C:\Windows\Temp folder.
Collect below logs and send them to Monofor Support Team.
MONOSIGN-CREDENTIAL-PROVIDER.log
MONOSIGN-CREDENTIAL-PROVIDER-FILTER.log
MONOSIGN-CREDENTIAL-PROVIDER-WEB.logFor temporary disable it can be uninstall Monosign Credential Provider on Windows machine.
6- Uninstall
Uninstall Monosign Credential Provider needs to run CP-Uninstall.reg file on target Windows machine locally or remotely.
