Active Directory
This document explains how to implement Monosync with a Active Directory server.
📘 Instructions
This documentation contains 2 main steps for integration.
Service User Permissions
Active Directory Requirement
1. Service User Permissions
Monosync need a service user to communicate with Active Directory. This user must be following permissions on specific OU in the Active Directory.
Example user name : monosync_svc
UserName | Permissions | Description |
|---|---|---|
monosync_svc | Create, Delete, and manage user accounts | Managing user accounts operations |
Modify the membership of a group | Modifying user accounts membership of the groups | |
Create, Delete, and manage groups | Managing user groups operations |
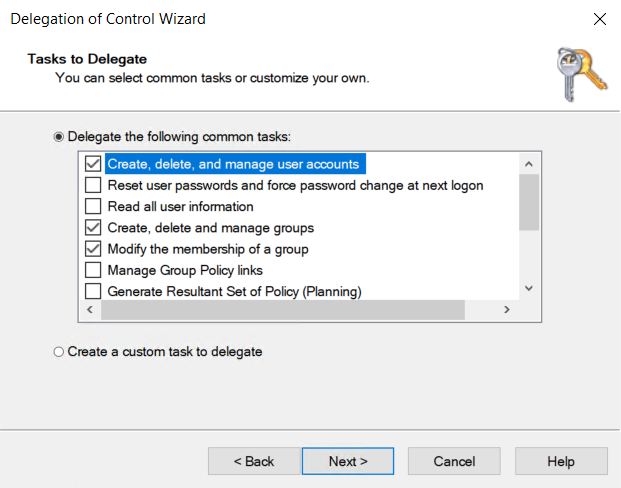
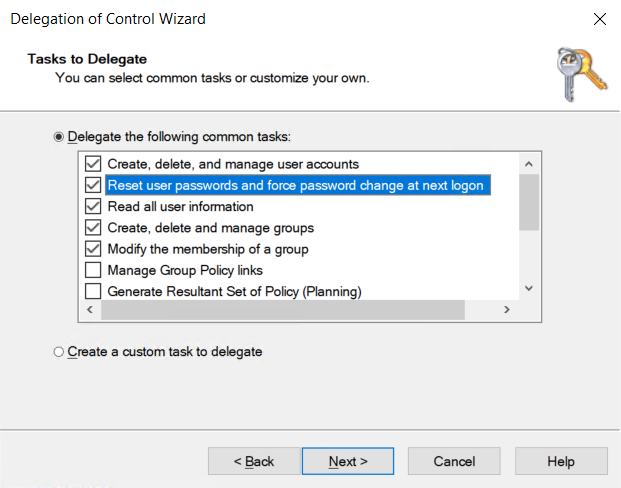
Please be aware of that this service user delegate the permissions only specific permissions. Don’t delegate the permission on root domain.
2. Active Directory
Monosync is using secure connection(LDAPS - TCP/636) to communicate with Active directory. If Active Directory LDAPS is not enabled you can follow below requirements to enable it.
To enable LDAPS, you must install a certificate that meets the following requirements:
The LDAPS certificate is located in the Local Computer's Personal certificate store (programmatically known as the computer's MY certificate store).
A private key that matches the certificate is present in the Local Computer's store and is correctly associated with the certificate. The private key must not have strong private key protection enabled.
The Enhanced Key Usage extension includes the Server Authentication (1.3.6.1.5.5.7.3.1) object identifier (also known as OID).
The Active Directory fully qualified domain name of the domain controller (for example, dc.monofor.com) must appear in one of the following places:
The Common Name (CN) in the Subject field.
DNS entry in the Subject Alternative Name extension.
The certificate was issued by a CA that the domain controller and the LDAPS clients trust. Trust is established by configuring the clients and the server to trust the root CA to which the issuing CA chains.
Use the Schannel cryptographic service provider (CSP) to generate the key.
Than restart the Active Directory Server(s).
After a certificate is installed, follow these steps to verify that LDAPS is enabled:
Start the Active Directory Administration Tool (Ldp.exe).
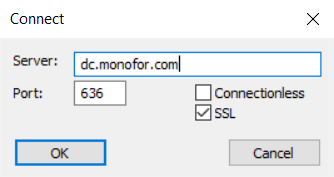
On the Connection menu, click Connect.
Type the name of the domain controller to which you want to connect.
Type 636 as the port number.
Click OK.
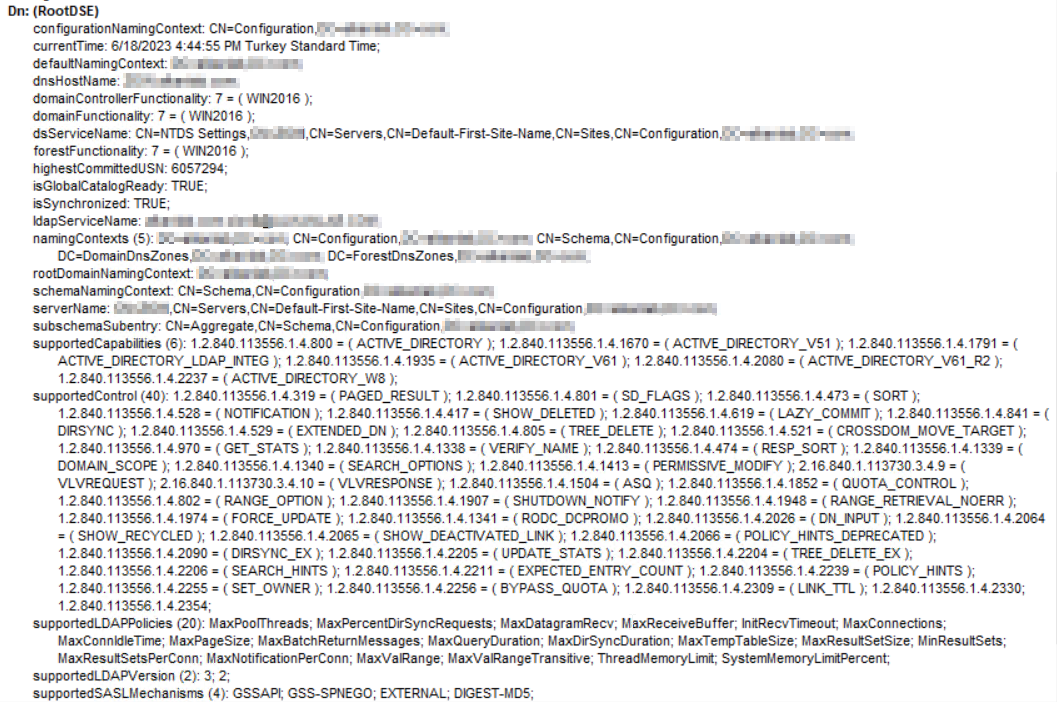
RootDSE information should print in the right pane, indicating a successful connection.
For communication from Monosync to Active directory firewall ports must be open.
Source | Destination | Port |
|---|---|---|
Monosync Servers | Active Directory Servers | TCP/636 |
